
A long-running DNS hijacking campaign has been uncovered abusing compromised routers to redirect internet traffic through rogue DNS resolvers hosted in Aeza International, a bulletproof hosting provider sanctioned by the US Treasury in 2025.
The attackers built an invisible traffic redirection network that enabled targeted user fingerprinting, malicious ad delivery, and potentially broader adversary-in-the-middle (AiTM) attacks.
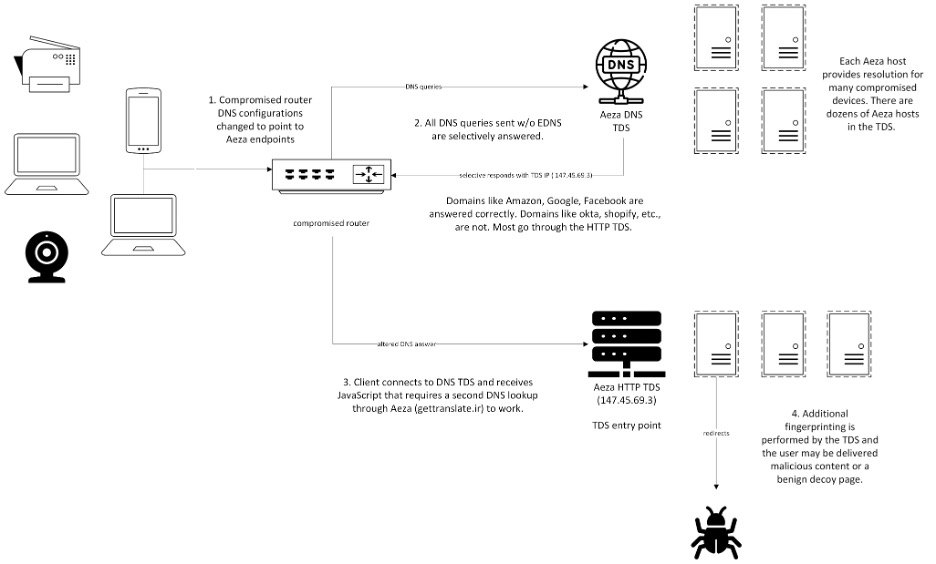
The operation was discovered by Infoblox researchers investigating anomalous DNS behavior and was traced back to a complex system involving router exploitation, DNS manipulation, and an HTTP-based traffic distribution system (TDS). The campaign has been active since at least mid-2022 and appears to be financially motivated.
Aeza International (AS210644) was designated by US authorities in July 2025 for offering services to cybercriminal actors. Known for its bulletproof hosting practices, Aeza remains a haven for malware operators, phishing campaigns, and illicit content distribution. In this campaign, its resolvers played a key role by masquerading as legitimate DNS servers, silently hijacking DNS queries from users behind compromised routers.
This compromise typically happens on outdated or misconfigured devices whose DNS settings are changed to point to attacker-controlled resolvers. This reroutes all DNS queries from any device connected to the infected router. The substituted resolvers selectively manipulate responses, directing users to domains hosting malicious JavaScript payloads, scam pages, or affiliate-driven ad pages.
Unlike typical DNS hijacks, this campaign features an elaborate obfuscation mechanism:
- The rogue resolvers respond only to DNS queries without the EDNS0 extension, causing most modern tools and researchers to receive malformed or blank replies.
- TTL (time-to-live) values are set to just 20 seconds, ensuring that devices must frequently re-query the rogue resolvers, enabling rapid redirect changes and evading caching.
- Domains used for redirection include typo-squatted or unregistered entries like gettranslate[.]ir, used to verify whether a device is behind a compromised router.
Infoblox
Devices behind affected routers that attempt to connect to popular sites may receive either genuine or altered IP addresses depending on the request's domain, location, and timing. Well-known domains like Google or Facebook are often resolved accurately, but others, including domains tied to authentication services like Okta, receive altered responses, raising the risk of credential theft or phishing.
Once a DNS request resolves to an attacker-controlled IP, the victim's browser receives a JavaScript payload that fingerprints the device and checks for compromise validation by attempting to resolve intentionally broken domains. If the criteria are met, the user is redirected through a cascade of affiliate ad platforms. In some cases, the infrastructure also installed cryptocurrency miners and locked out administrative access on compromised devices.
The use of a non-standard DNS query restriction (disabling EDNS0) allowed the actors to fly under the radar for years. The researchers only began piecing together the campaign after correlating passive DNS data from “port 53” monitoring with previously unexplained resolution anomalies, including false responses to domains linked to malware such as Kimwolf.
To defend against this type of DNS hijacking, users and administrators should regularly audit router configurations and perform firmware updates when available. Also, it is advisable to use secure DNS protocols such as DNS-over-HTTPS (DoH) or DNS-over-TLS (DoT) to bypass router DNS settings.







Leave a Reply