
A newly discovered Android remote access trojan (RAT) named Cellik enables full device compromise, real-time surveillance, and stealthy deployment through bundled Play Store apps.
The malware was uncovered by iVerify on dark web cybercrime channels. The researchers' analysis reveals that Cellik combines a powerful remote control suite with a sophisticated app injection system, capabilities more commonly associated with state-level spyware than the tools sold to low-level cybercriminals.
The malware is part of a growing trend in Android malware-as-a-service (MaaS), where fully-featured RATs are packaged with intuitive control panels, automated APK builders, and integration with legitimate app ecosystems. With Cellik, attackers can browse the Google Play Store from the RAT's backend interface, select popular apps, and wrap them with Cellik's payload in a single click, producing a new malicious APK for distribution via phishing sites, alternative app stores, or SMS lures.
Once installed on a target device, Cellik gives the operator total control. It supports real-time screen streaming with remote interaction, effectively turning the attacker's panel into a live feed of the victim's device with the ability to simulate taps, swipes, and other inputs. This includes live keylogging, allowing attackers to capture everything typed on the device, from messages to login credentials.
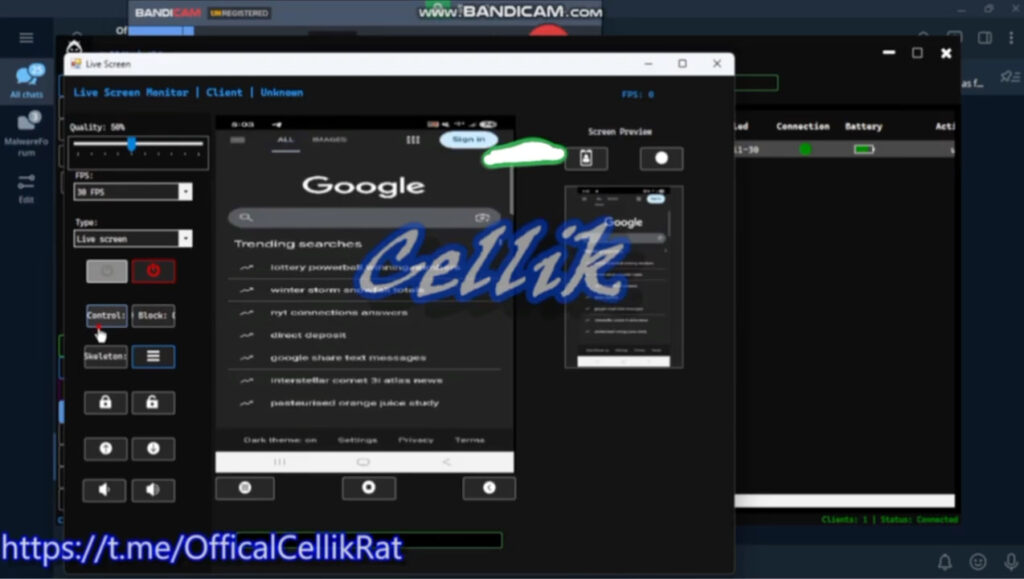
The malware also intercepts all incoming notifications, granting access to messages, alerts, and even one-time passcodes. The attacker can browse the full file system, upload or download files, delete data, and access linked cloud directories, operations conducted over encrypted channels to evade detection.
One of Cellik's more insidious features is its hidden browser module. This headless browser runs invisibly on the victim's phone, allowing attackers to navigate to websites, interact with them, and submit forms, all without the user seeing any of it. By leveraging stored cookies or autofill data, the attacker can hijack sessions, steal credentials, or perform phishing attacks in real time.
Cellik also features an “injection system” designed to overlay fake login screens or inject malicious scripts into legitimate apps. The attacker can craft templates for specific apps, such as Gmail, Facebook, or banking apps, and deploy multiple simultaneous overlays. Harvested credentials are exfiltrated silently, giving attackers seamless access to victim accounts.
Google Play Protect is designed to detect and block malicious apps, but attackers may evade this protection by using trusted app packages as vehicles, reducing the likelihood of triggering security flags during app reviews or on-device scans.
Users are advised to avoid sideloading APKs from unofficial sources, restrict accessibility and notification permissions, and monitor for increased battery drain and inexplicable overheating.







New ?! Seriously ? I get the premise , but I thought google users liked this .