
Phishing actors are increasingly exploiting misconfigured email routing and authentication systems to spoof legitimate company domains, enabling credential theft, financial fraud, and business email compromise (BEC).
According to a detailed analysis by Microsoft Threat Intelligence, the technique has been gaining traction since mid-2025 and remains highly effective against organizations with complex mail flows and weak spoof protections.
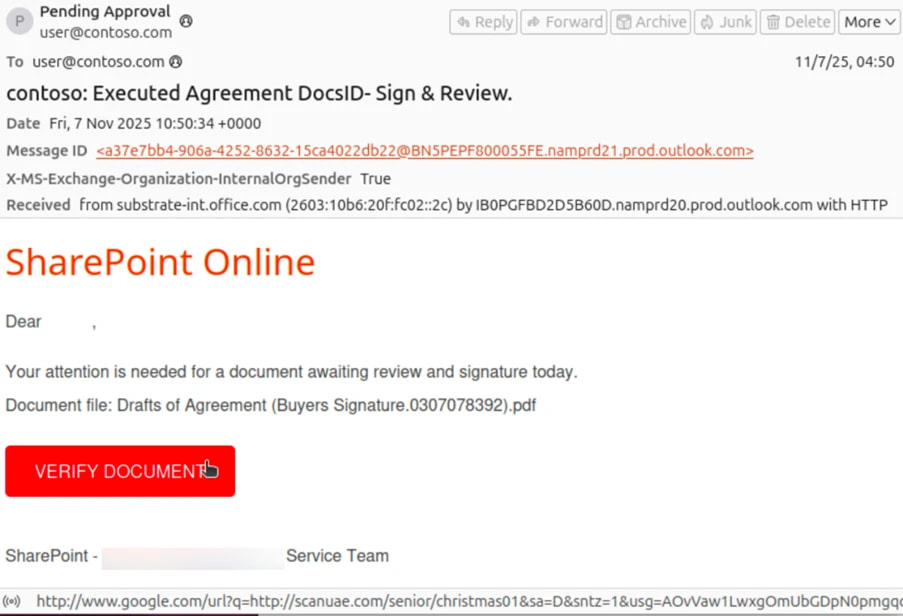
The malicious activity leverages email systems where the organization's domain appears in both the “From” and “To” fields, causing the messages to look like they originated internally. These phishing messages, often crafted with themes like HR communications, shared document alerts, or password reset notifications, are distributed at scale and typically linked to phishing-as-a-service (PhaaS) platforms such as Tycoon2FA. Microsoft's telemetry shows that over 13 million malicious emails associated with Tycoon2FA were blocked in October 2025 alone, underscoring the scale of these operations.
Microsoft
Microsoft emphasizes that this attack vector is not due to flaws in Exchange Online's “Direct Send” capability, but rather in cases where organizations have diverted their MX (mail exchanger) records to third-party services or on-premises environments without properly enforcing anti-spoofing protocols like SPF, DKIM, and DMARC. Insecure configurations allow threat actors to bypass authentication checks and land in users' inboxes.
Tycoon2FA and similar PhaaS platforms equip attackers with tools to bypass multifactor authentication (MFA) via adversary-in-the-middle (AiTM) phishing kits. Attackers host phishing pages on actor-controlled domains, using redirectors such as Google Maps URLs or obfuscated JavaScript loaders. Victims are led through CAPTCHAs and other decoy mechanisms before arriving at phishing sites that harvest credentials. These pages often mimic Microsoft 365 login portals and are dynamically generated using base64-encoded email addresses.
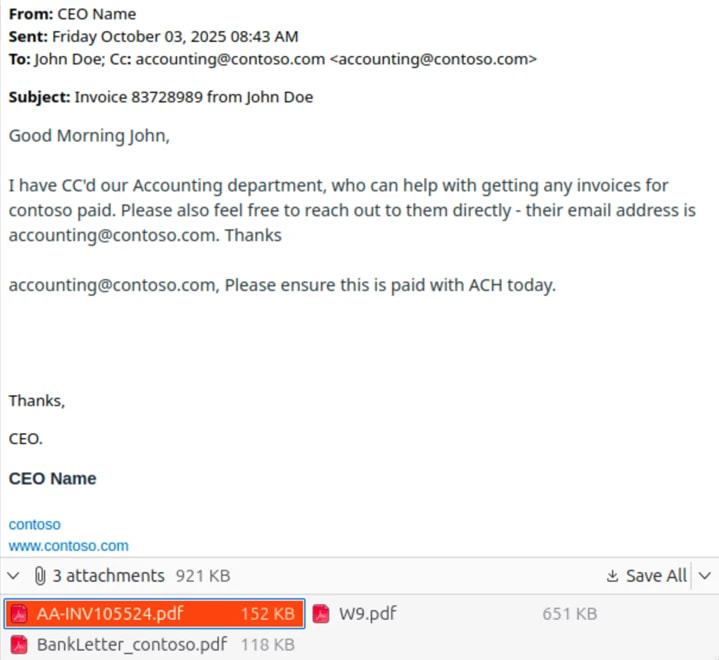
Beyond credential theft, Microsoft has tracked spoofed email campaigns designed to trick organizations into fraudulent wire transfers. These scams often impersonate internal financial correspondence threads such as invoice requests from an executive or supplier and include attachments like fake invoices, falsified W-9 forms, and fabricated bank letters. The documents use stolen identities and realistic branding to increase legitimacy. In one example, a scam email used the recipient's address for both sender and recipient, displayed the CEO's name as the sender, and attached payment instructions to a fraudulent bank account likely opened using stolen personal information.
Microsoft
The success of these spoofing attacks often hinges on the appearance of internal legitimacy. Email headers provide subtle but critical clues to detection such as SPF or DMARC failures, unexpected sender IP addresses, and inconsistencies like messages marked as “InternalOrgSender=True” while showing “MessageDirectionality=Incoming”. Unfortunately, many tenants either lack the expertise to configure these controls or operate under permissive policies (e.g., DMARC set to “none”), allowing spoofed emails to evade even basic filtering.
Microsoft clarifies that tenants whose MX records point directly to Office 365 benefit from native spoofing protections and are not exposed to this particular vector. However, organizations using hybrid deployments or routing email through third-party services must take steps to close these gaps.







Leave a Reply