
A data breach affecting 17.5 million Instagram accounts has been confirmed by security firm Malwarebytes, which warns that the leaked data is already being shared freely on hacker forums.
According to an email alert sent to Malwarebytes users earlier today, the data was discovered during the firm's ongoing dark web monitoring operations. The leak includes a broad range of sensitive user data, including:
- Usernames
- Full names
- Email addresses
- Phone numbers
- Partial physical addresses
- Other contact details
Malwarebytes cautions that attackers are likely to exploit this information in impersonation attacks, phishing campaigns, and credential harvesting attempts, especially by leveraging Instagram's password reset mechanism to gain access to user accounts.
The stolen data appears to originate from an Instagram API leak that occurred in 2024. A threat actor operating under the alias “Solonik” published the dataset on BreachForums on January 7, 2026, offering it for free. The post claims to contain over 17 million records in JSON and TXT formats, targeting instagram.com and allegedly affecting users worldwide. A large number of sample entries included in the post show raw data such as usernames, email addresses, international phone numbers, and user IDs, corroborating Malwarebytes' findings.
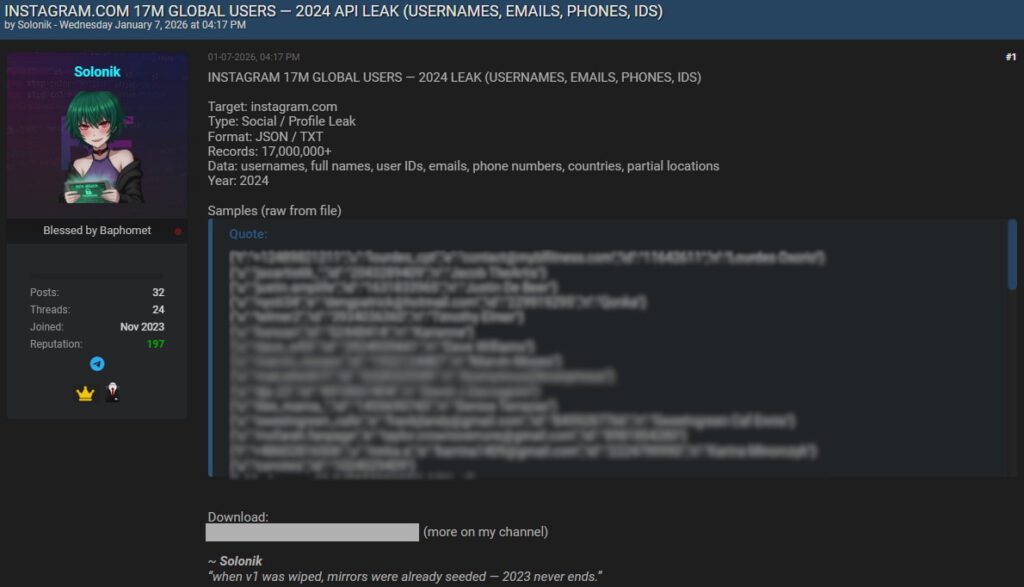
Meta, Instagram's parent company, has yet to confirm the breach. CyberInsider's requests for comment from Meta have so far gone unanswered, and there is currently no official statement or public acknowledgment of the incident on Meta's security pages or social media accounts.
While it is unclear whether the compromised data came from an exposed API endpoint, third-party integration vulnerability, or internal misconfiguration, the leak contains entries with structured JSON fields typical of API responses. Some entries include indicators of data collection from profile metadata, possibly scraped or accessed via insecure endpoints before 2025.
Users whose contact details were exposed may receive legitimate-looking emails or messages that prompt them to reset their passwords or verify their identities. Malwarebytes notes that some affected users are already receiving password reset notifications from Instagram, which may be legitimate or part of ongoing abuse by malicious actors.
To assess exposure, Malwarebytes offers a free Digital Footprint scan via its portal, which lets users check whether their email addresses appear in the leaked dataset. Meanwhile, it is recommended to reset Instagram passwords and enable two-factor authentication (2FA).
Article Update (1/11) – Instagram has claimed on X that there has been no breach on its systems, but rather an exploitation of its password reset system from an external party.
The social media platform has still not explained if the data posted on hacker forums is genuine or related to these notifications users have been receiving in the past couple days.
Our requests for a comment have remained unanswered.
Update (1/12) – Have I Been Pwned added the Instagram security breach on its database, claiming that it is unrelated to Instagram disclosure about the password reset abuse from yesterday. HIBP determined the number of impacted users to be 6.2 million.







Leave a Reply