
New technical reports from Kaspersky and Rapid7 have revealed extensive details about the Notepad++ supply chain attack, confirming it was a months-long, highly targeted cyber-espionage campaign linked to the Chinese APT group Lotus Blossom.
The attackers leveraged hijacked infrastructure to push custom malware to select victims worldwide, combining multiple infection chains and stealthy loader techniques.
Kaspersky’s telemetry shows that the attackers rotated infrastructure, downloaders, and payloads between July and October 2025, delivering malicious updates through forged manifests hosted on attacker-controlled servers. These updates were distributed selectively, targeting fewer than two dozen machines, including government and financial institutions in Southeast Asia and Central America, and IT providers in Vietnam.
All malicious updates were packaged as NSIS installers and executed via Notepad++’s legitimate updater, GUP.exe. Initial access always relied on infrastructure-level redirection, not vulnerabilities in Notepad++ itself.
Kaspersky identified three distinct infection chains:
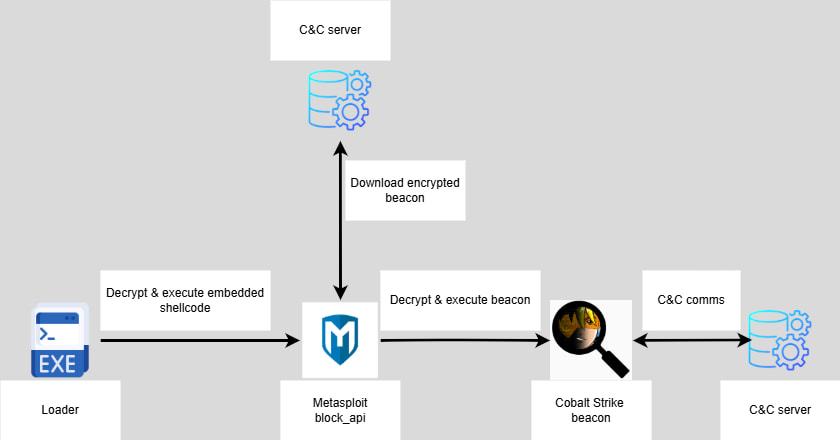
- Chain #1 (late July–early August): Used a repurposed copy of ProShow software, exploiting a legacy vulnerability rather than DLL sideloading. This variant fetched a Metasploit loader, which downloaded and executed a Cobalt Strike Beacon. The Beacon contacted domains like cdncheck.it[.]com and 45.77.31[.]210.
- Chain #2 (mid–late September): Dropped Lua interpreter components that executed shellcode embedded in a configuration file (alien.ini). The shellcode similarly deployed Cobalt Strike Beacons, using modified URLs and a stealthy system information collection technique. Attackers continued iterating on this chain into October, changing domains and communication methods.
- Chain #3 (October): Shifted to DLL sideloading via BluetoothService.exe, a renamed legitimate Bitdefender tool. This variant loaded a malicious DLL (log.dll), which decrypted and executed a sophisticated custom backdoor that Rapid7 has dubbed Chrysalis.
Advanced Chrysalis malware
Rapid7’s deep analysis of Chain #3 revealed Chrysalis, a previously undocumented and advanced backdoor. It uses custom encryption, reflective loading, API hashing, and a stealthy configuration hidden in an encrypted shellcode blob. The backdoor supports persistence via service creation or registry keys, and can execute over a dozen commands, including spawning reverse shells, file transfers, and full self-removal.
Chrysalis communicates over HTTPS using domains like api.skycloudcenter[.]com, blending into normal traffic with Chrome user-agent strings and a DeepSeek-style URL format (/a/chat/s/{GUID}).
During forensic investigation, Rapid7 also discovered secondary payloads deployed via tiny C compilers and shellcode wrappers, further confirming the use of Metasploit and Cobalt Strike in tandem with custom tools. All payloads showed signs of shared infrastructure and encryption keys (notably the XOR key CRAZY) and reused domains like api.wiresguard[.]com.
Rapid7
The attackers’ tactics, custom loaders, staged shellcode, domain masquerading, and selective delivery strongly align with Lotus Blossom, also known as Billbug, a Chinese APT active since 2009. Rapid7 attributes the campaign to this group with moderate confidence, based on overlapping infrastructure, toolchains, and past behavior.
Users of Notepad++ should upgrade immediately to version 8.8.9 or newer, which includes hardened update verification mechanisms.







Leave a Reply