
A $6,000 malware toolkit known as “Stanley” is being sold on Russian cybercrime forums, offering a malicious Chrome extension that spoofs entire websites while preserving the real domain in the browser’s address bar, complete with a promise that it will pass Chrome Web Store review.
Discovered by Varonis researchers in mid-January 2026, Stanley is part of a growing trend in commercialized browser malware. The toolkit was first advertised on January 12 by a seller using the alias “Стэнли,” who promoted it with demo videos targeting cryptocurrency platforms like Binance and Coinbase. Varonis reported the campaign to Google and the extension's hosting provider on January 21; the command-and-control (C2) infrastructure was taken offline the next day, but the extension remains live in the Chrome Web Store.
Varonis
According to Varonis, Stanley surfaced on underground forums on January 12, 2026, advertised by a seller using the alias “Стэнли.” The listing frames the toolkit as a packaged service rather than a custom build, complete with demo videos showing live attacks against well-known cryptocurrency platforms such as Binance and Coinbase. The premium tier includes customization, access to a web-based command-and-control (C2) panel, and the promise of successful publication on Google’s extension store.
At its core, the toolkit is designed to masquerade as a legitimate Chrome extension. Varonis analyzed a sample extension named “Notely,” presented as a minimalist note-taking and bookmarking tool. While the extension does provide basic advertised functionality, this benign feature set primarily serves as cover for its extensive permissions, including access to all URLs, scripting, web navigation, storage, and notifications. The malicious code executes at document_start, giving it control over pages before legitimate content loads.
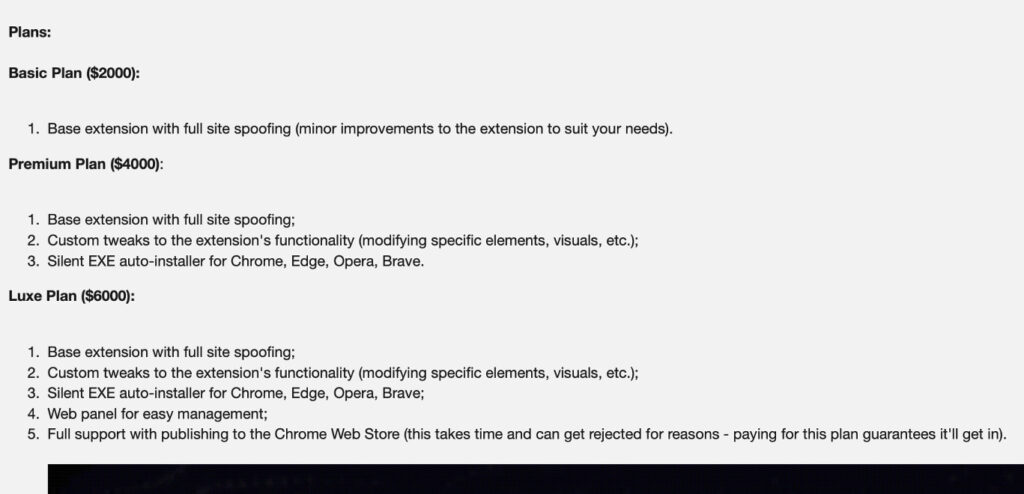
Once installed, the extension checks in with its C2 infrastructure every 10 seconds, using the victim’s IP address as a unique identifier rather than a randomly generated ID. This design allows operators to track users across sessions, perform geographic targeting, and selectively activate attacks. The management panel shown in the seller’s demo shows operators configuring per-victim URL-hijacking rules, specifying which legitimate site should be intercepted and which phishing page should be displayed instead.
Varonis
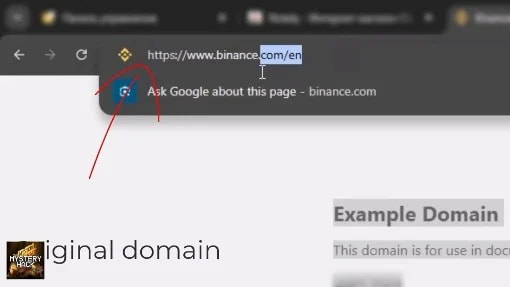
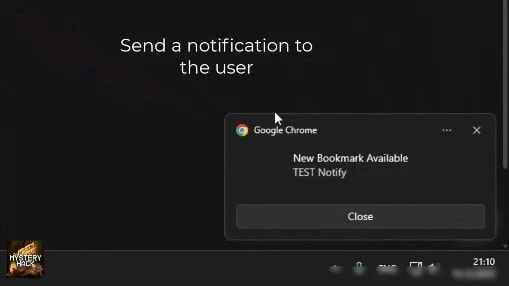
The primary attack technique involves overlaying a full-screen iframe containing attacker-controlled content over the legitimate site. Crucially, the browser’s address bar continues to display the correct domain, such as binance.com, while all interactions occur on the phishing page. Stanley also supports Chrome-native push notifications, enabling attackers to lure victims to targeted pages using messages that appear more trustworthy than standard web prompts. Backup domain rotation ensures the malware remains functional even if the primary C2 server is taken offline.
Varonis
Varonis reported the infrastructure to the Chrome Web Store and the hosting provider on January 21, 2026. While the C2 server was taken down the following day, the malicious extension itself remained available at the time of writing.
Users are advised to regularly audit installed extensions, remove unused ones, and be wary of add-ons that request broad permissions such as access to all websites.







Leave a Reply