
Security researchers at KU Leuven have disclosed a critical flaw in Google's Fast Pair protocol that allows attackers to forcibly hijack Bluetooth accessories and covertly track users.
The vulnerability, dubbed WhisperPair, affects a wide range of popular wireless audio devices and demonstrates systemic security oversights in Fast Pair's design and certification process.
The attack was discovered by researchers from KU Leuven's COSIC group and the DistriNet group. Their research uncovered fundamental flaws in how many flagship Bluetooth accessories implement the Fast Pair protocol, a system intended to simplify and speed up pairing between Android devices and accessories such as earbuds, headphones, and speakers.
Google Fast Pair works by allowing Android devices (Seekers) to initiate a Bluetooth connection with accessories (Providers) using a streamlined process that includes account synchronization and device discovery. However, many devices fail to enforce a key requirement: they do not verify whether they are in pairing mode before responding to a pairing request. This oversight allows attackers to simulate a legitimate connection and forcibly initiate a Bluetooth pairing without user consent.
Once paired, an attacker can take full control of the accessory, playing disruptive audio at maximum volume or, more concerningly, recording audio through the device's microphone. In lab conditions, the attack succeeded in a median time of 10 seconds at distances up to 14 meters, requiring only standard Bluetooth-capable hardware, such as a phone or laptop. No physical access to the victim's device is needed.
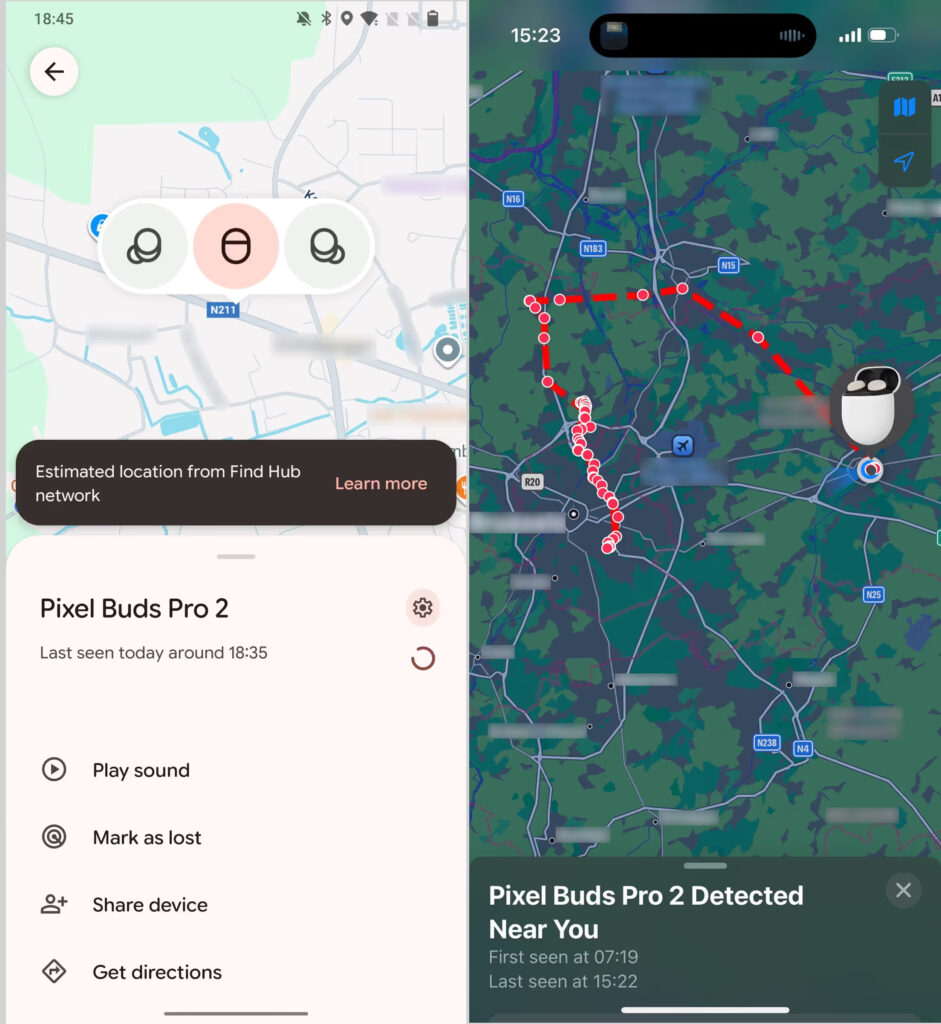
Location tracking also possible
The study also highlighted how these compromised accessories can be exploited for real-world tracking. Some Bluetooth devices integrate with Google's Find My Device network (also known as Find Hub), which leverages nearby Android phones to update the location of lost accessories. If an accessory has never been paired with an Android device, an attacker can bind it to their own Google account, effectively enrolling it into the network. As the victim carries the accessory, the attacker receives periodic location updates via the Find Hub network. Alarmingly, users may receive delayed and ambiguous tracking alerts showing their own device as the source, leading many to disregard the warning as a glitch.
KU Leuven
The affected accessories passed both manufacturer-level QA and Google's certification process without the vulnerability being detected, indicating deep-rooted weaknesses in Fast Pair's compliance and security review pipeline. The vulnerability spans multiple vendors and chipsets, further underscoring its ecosystem-wide impact.
WhisperPair was responsibly disclosed to Google in August 2025 and has been assigned CVE-2025-36911. Google classified the issue as critical and awarded the maximum bug bounty of $15,000. A coordinated 150-day disclosure window was agreed upon, allowing vendors time to develop and deploy patches. While some manufacturers have released firmware updates, many vulnerable devices remain unpatched and exposed.
Users concerned about WhisperPair have limited options because the vulnerability resides in the accessory's firmware, and Fast Pair cannot be disabled. Neither updating the phone nor factory-resetting the device resolves the issue. The only effective defense is to install firmware updates issued by the accessory's manufacturer.
Even users outside the Android ecosystem, such as iPhone owners using compatible accessories, are affected, since the flaw lies within the accessory's Bluetooth implementation, not the operating system.
KU Leuven researchers propose a long-term fix by embedding cryptographic binding of pairing intent into the protocol itself, ensuring devices cannot initiate unauthorized pairing outside of expected workflows. Full technical details will be published in an upcoming academic paper.







Leave a Reply