
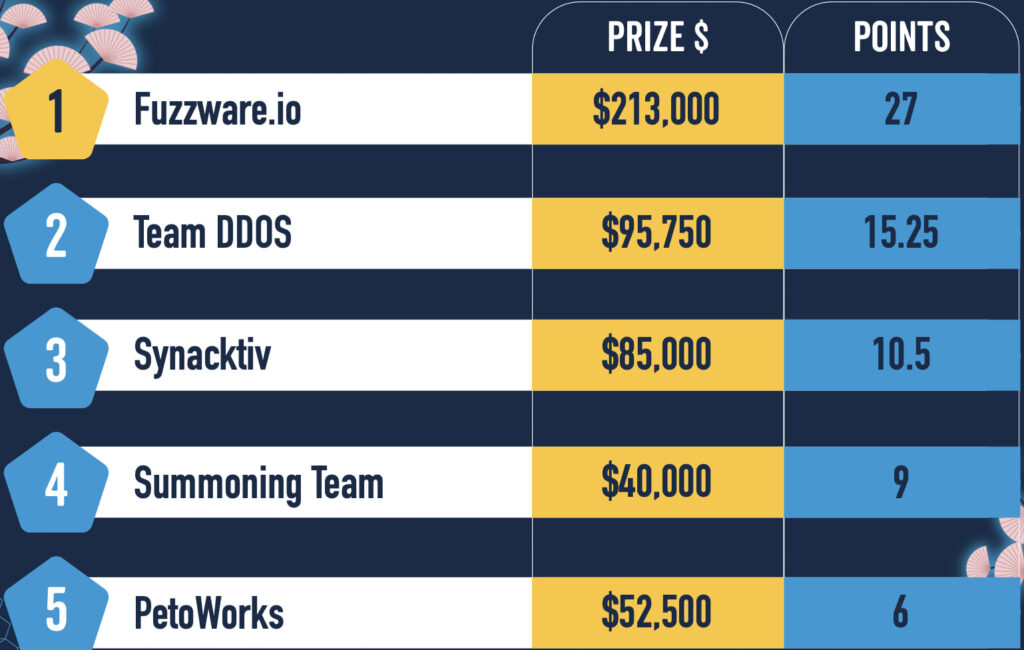
The second day of Pwn2Own Automotive 2026 concluded with researchers earning an additional $439,250 for discovering 29 new zero-day vulnerabilities across modern automotive systems.
This brings the event’s cumulative total to $955,750 for 66 unique bugs, with Munich-based Fuzzware.io continuing to dominate the leaderboard ahead of the final day.
ZDI
Once again, infotainment systems and electric vehicle (EV) charging infrastructure were in the spotlight. The Alpine iLX-F511, Kenwood DNR1007XR, and Phoenix Contact CHARX SEC-3150 were repeatedly targeted, while the Autel and ChargePoint home EV chargers remained high-value targets. The event, held in Tokyo and hosted by Trend Micro’s Zero Day Initiative (ZDI), continues to expose systemic weaknesses in consumer automotive tech.
Among the standout discoveries was a powerful triple-bug chain demonstrated by Rob Blakely of Technical Debt Collectors against Automotive Grade Linux (AGL), a collaborative open-source platform used by major car manufacturers. By chaining an out-of-bounds read, memory exhaustion, and a heap overflow, Blakely earned $40,000 and four Master of Pwn points.
Fuzzware.io extended its lead through several high-impact submissions. Team members Tobias Scharnowski, Felix Buchmann, and Kristian Covic delivered successful exploits across multiple devices, including:
- A three-bug chain against the Phoenix Contact CHARX SEC-3150 worth $50,000.
- A command injection attack on ChargePoint’s Home Flex charger for $30,000.
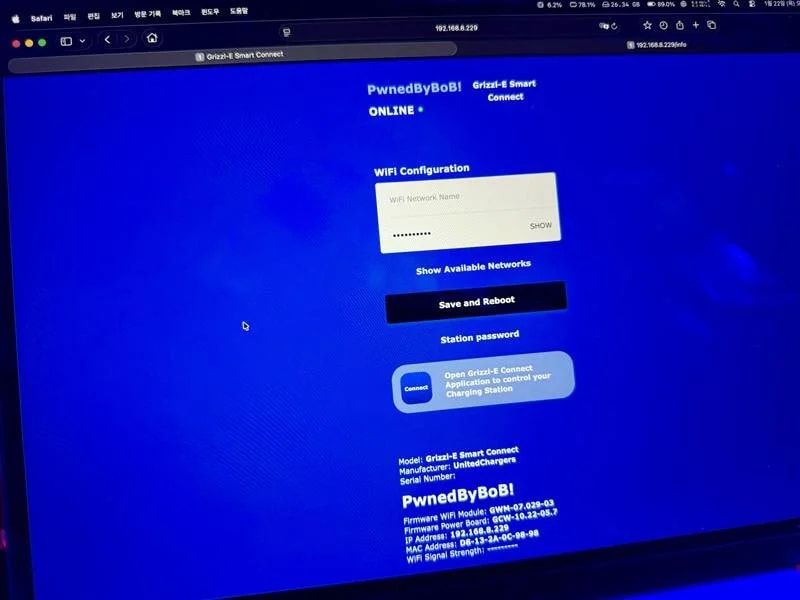
- A collision-heavy but still rewarding submission against the Grizzl-E Smart 40A, netting $15,000.
FuzzingLabs’ Julien Cohen-Scali also made a strong showing, combining an authentication bypass and privilege escalation to compromise the Phoenix Contact CHARX SEC-3150 and earn $20,000. Phoenix Contact, a key supplier of industrial-grade EV charging controllers, has proven particularly vulnerable this year, with multiple teams breaching its defenses via logic flaws, injection vectors, and access control issues.
Other critical wins included:
- InnoEdge Labs’ Hank Chen exploiting a dangerous method in Alpitronic’s HYC50 charger (Lab Mode) for $40,000.
- Synacktiv targeting the Autel MaxiCharger AC Elite Home 40A with a stack-based buffer overflow for $30,000.
- BoredPentester compromising the Grizzl-E Smart 40A and Kenwood DNR1007XR across multiple rounds with command injection chains totaling $25,000.
Infotainment systems remained heavily targeted, particularly the Alpine iLX-F511 and Kenwood DNR1007XR, both popular in aftermarket installations. Several researchers, including Team MAMMOTH, Sina Kheirkhah of Summoning Team, and BoB::Takedown, showcased successful command injection exploits or collisions on these devices.
With only one day left in the competition, Fuzzware.io holds a commanding lead in the Master of Pwn race. However, with hundreds of thousands still on the table and several devices yet to be fully explored, the final day may bring surprises. If you're looking for Day 1 results, check our previous coverage here.







Leave a Reply