
Microsoft has uncovered and disrupted RedVDS, a virtual server provider that has quietly fueled large-scale cybercriminal activity across the globe, enabling mass phishing, business email compromise (BEC), and financial fraud operations targeting multiple industries.
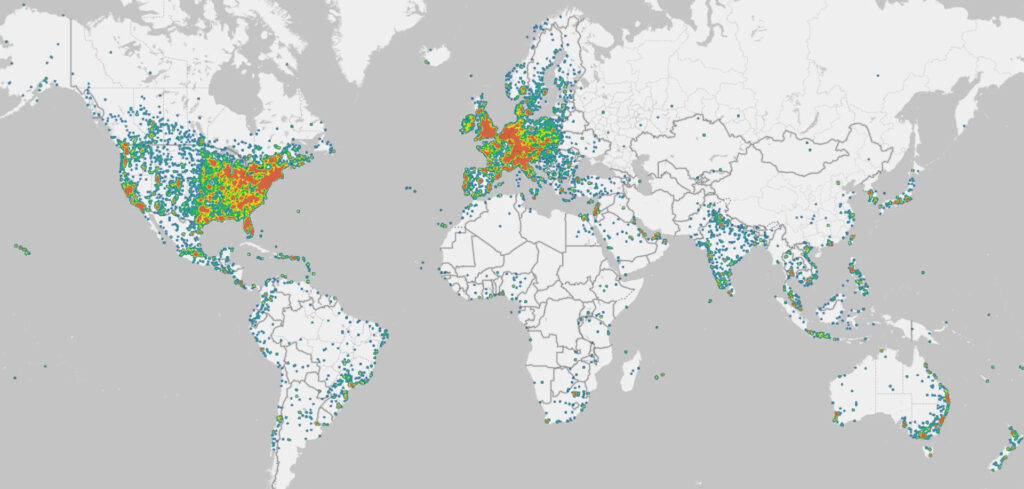
Microsoft traced RedVDS’s role as a central infrastructure enabler for dozens of financially motivated threat actors. Operating since at least 2019, RedVDS offered remote desktop servers for a nominal fee, facilitating thousands of cyberattacks against sectors including healthcare, real estate, legal services, education, and construction across the US, UK, France, Germany, Australia, and Canada.
Microsoft
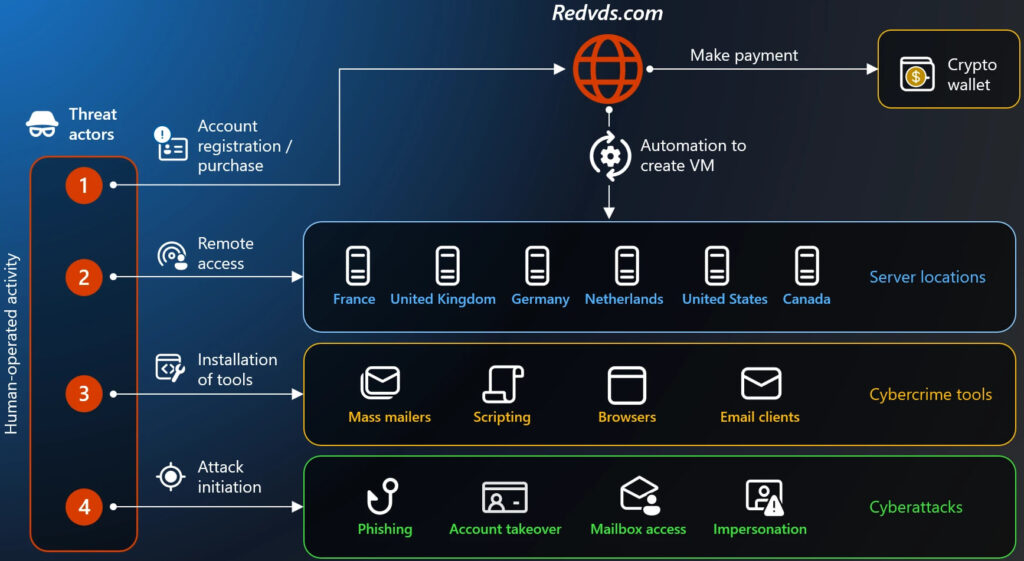
RedVDS is operated by a threat actor tracked as Storm-2470, who built the marketplace to offer cloned, administrator-access Windows servers via Remote Desktop Protocol (RDP). These virtual machines were sold anonymously using cryptocurrencies such as Bitcoin and Litecoin, with support for privacy-focused tokens like Monero and TRON. Microsoft observed over $40 million in fraud losses in the US alone since March 2025, linked to campaigns run from RedVDS infrastructure.
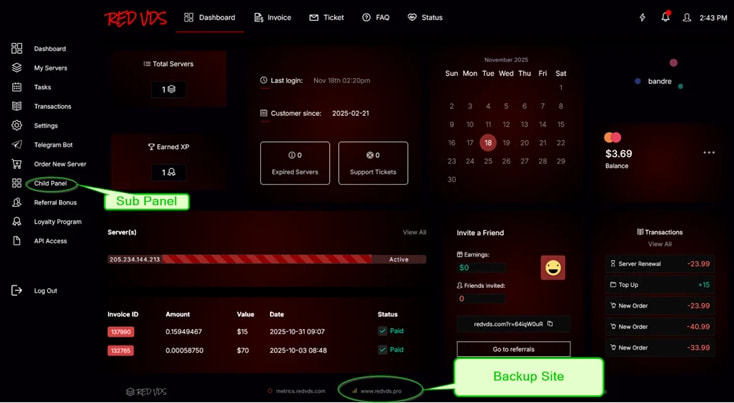
Microsoft’s Digital Crimes Unit (DCU), working with international law enforcement partners, has recently coordinated a takedown operation targeting RedVDS infrastructure and associated services, including the primary domain redvds[.]com and backups hosted at redvds[.]pro and vdspanel[.]space.
Microsoft
RedVDS enabling cybercrime
The RedVDS platform operated as a “no questions asked” VDS provider that allowed cybercriminals to spin up servers almost instantly using cloned Windows Server 2022 virtual machine images. Every RedVDS instance shared the same hostname and product key, allowing defenders to fingerprint and detect activity tied to the service.
Provisioning was handled via QEMU virtualization and VirtIO drivers, letting RedVDS deploy new servers in minutes, with full admin access and no usage caps. These cloned machines formed the backbone of criminal operations, blending into legitimate data center traffic from hosting providers in the US, Canada, the UK, France, and the Netherlands.
Importantly, RedVDS didn’t operate physical infrastructure but instead rented servers from third-party hosts, helping threat actors bypass geolocation filters and improve delivery rates for phishing campaigns.
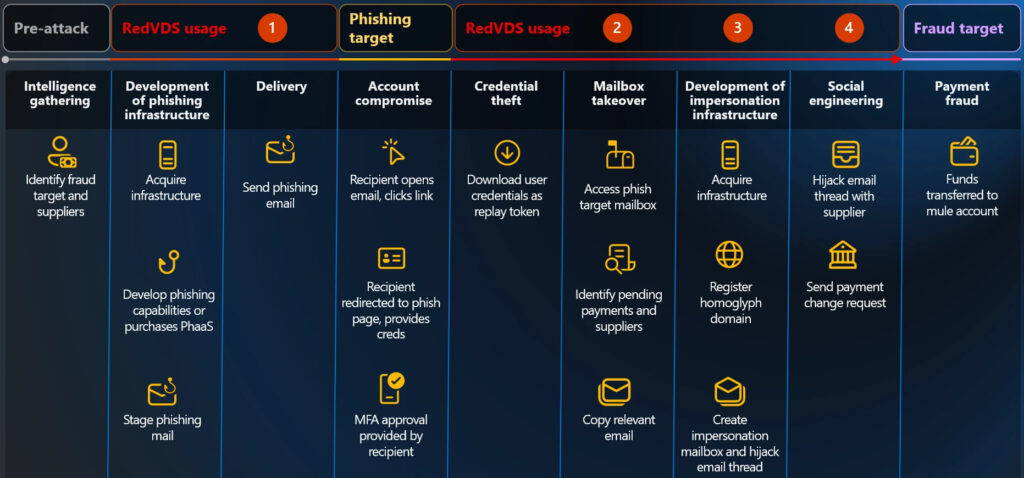
Once a server was provisioned, RedVDS customers typically followed a multi-stage attack chain:
- Reconnaissance – gathering financial and organizational data from targets
- Tool deployment – setting up phishing kits, spoof domains, and automation pipelines
- Phishing and credential theft – stealing login data, often bypassing MFA via session hijacking
- Mailbox takeover – harvesting sensitive emails, invoices, and financial records
- Impersonation – launching homoglyph domain-based BEC attacks
- Fraud execution – sending fake invoices or payment change requests to trick victims into wire transfers
Microsoft
RedVDS’s infrastructure was used by multiple prominent cybercrime groups, including Storm-0259, known for high-volume phishing attacks, Storm-2227, Storm-1575, and Storm-1747, involved in BEC and credential theft, and users of RaccoonO365, a phishing-as-a-service kit.
RedVDS tenants deployed a consistent toolkit of mass-mailing and harvesting tools, including UltraMailer, Sky Email Extractor, and Email Sorter Pro. For operational security, they used VPNs (NordVPN, ExpressVPN), privacy browsers, and proxy tools to hide activity and reroute traffic.
Microsoft
Remote access software like AnyDesk enabled easier management or sharing of access among threat actors, while scripting environments like Python and automation attempts using Microsoft Power Automate suggest a growing push toward scalable, scripted phishing workflows. In some cases, criminals also used AI tools such as ChatGPT, Grammarly, and QuillBot on the RedVDS boxes to craft more convincing English-language phishing lures.
Although the takedown of RedVDS is a major disruption to a key player in the cybercriminal infrastructure supply chain, the continued demand for anonymous, low-cost hosting services by threat actors almost guarantees that another service will soon fill the void.







Leave a Reply