
A targeted spearphishing campaign has abused the npm package registry as a long-term hosting platform for credential-stealing phishing pages aimed at manufacturing and healthcare organizations in the US and allied countries.
The operation was uncovered by the Socket Threat Research Team, which identified 27 malicious npm packages published under six aliases over a period of at least five months. Rather than acting as software dependencies, the packages delivered browser-executed HTML and JavaScript phishing components that impersonated document-sharing portals and Microsoft sign-in pages.
Socket
Socket identified 25 targeted individuals, primarily in sales, account management, and business development roles at organizations in manufacturing, industrial automation, plastics, and healthcare. The hardcoded targeting and role alignment indicate deliberate victim selection rather than opportunistic phishing.
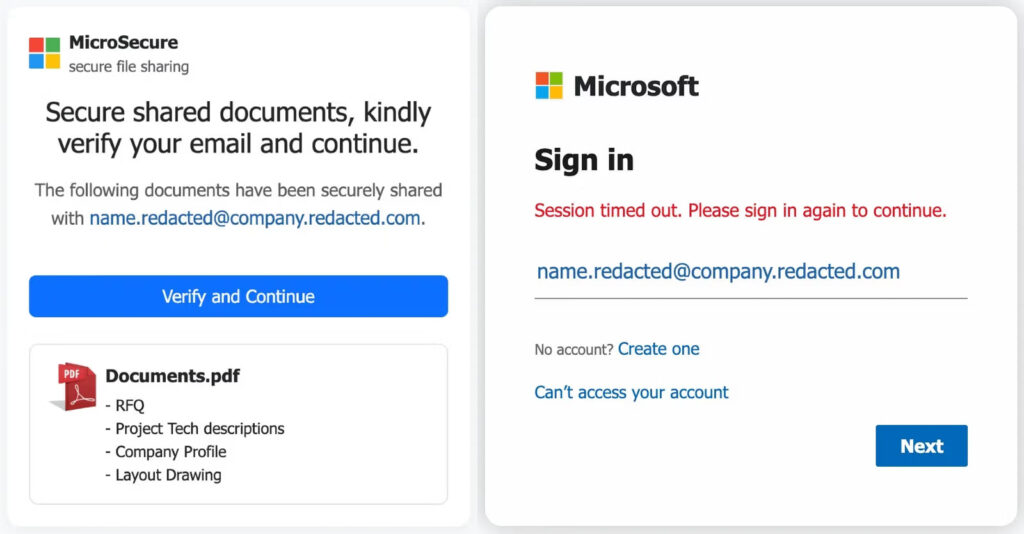
The packages functioned as self-contained phishing lures. When loaded in a browser, the code wiped the existing page and replaced it with attacker-controlled content using document.open() and document.write(). A typical flow presented a fake “secure document-sharing” verification page referencing RFQ-style documents, then transitioned the victim to a Microsoft-branded login prompt with the recipient’s email address prefilled to encourage credential submission.
To evade detection, the lures included multiple client-side anti-analysis controls. These checks screened for headless browsers and automation using signals such as navigator.webdriver, empty plugin lists, abnormal screen dimensions, and crawler user agents. Progress was also gated on real mouse or touch interaction. Hidden honeypot form fields were used to detect automated form fillers, causing the flow to fail closed when triggered.
After credentials were submitted, the script redirected victims to threat actor-controlled infrastructure, passing the victim identifier in the URL fragment. The researchers identified several embedded domains, including hexrestore[.]online, leoclouder[.]online, livestore[.]click, and jigstro[.]cloud. These endpoints overlap with publicly documented Evilginx adversary-in-the-middle (AiTM) phishing infrastructure, which can capture session cookies or tokens during interactive authentication and bypass traditional MFA.
Socket reported the campaign to the npm security team, requested suspension of the remaining live package, and notified all identified target organizations.
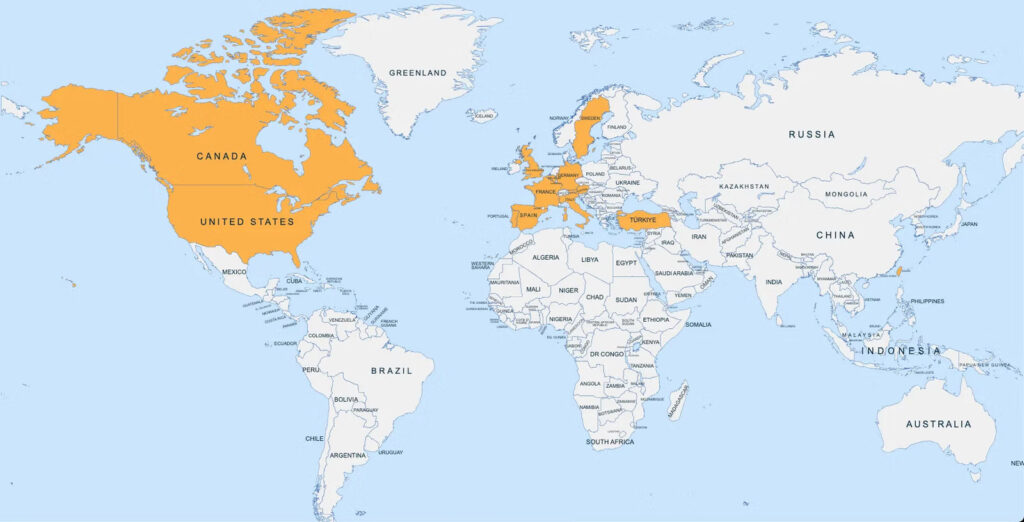
Geographically, the targets span the United States, Canada, Europe, and East Asia, largely within US-aligned countries. Socket noted that many affected companies participate in major industrial trade shows, suggesting attackers may have sourced sales contacts from exhibitor directories and public professional profiles.
Socket
Socket warned that package registries continue to be abused as durable phishing infrastructure rather than malware delivery channels. Recommended mitigations include scrutinizing npm dependencies for unexpected browser-side artifacts, monitoring CDN access from non-development environments, blocking known malicious domains, and adopting phishing-resistant MFA such as WebAuthn or passkeys, alongside monitoring for post-authentication compromise indicators.







Leave a Reply