As threats from advanced tracking and state-sponsored surveillance continue to grow, some privacy enthusiasts are looking for more protection in the form of multi-hop VPNs. If you consider the resources being spent by surveillance agencies to de-anonymize users, choosing a VPN service that offers a higher level of anonymity is indeed a valid consideration.
A multi-hop VPN simply encrypts your connection across two or more servers (multiple hops) before exiting to the regular internet. Routing your traffic through two or more servers in separate jurisdictions gives you a higher level of privacy and security — even if one server were to be compromised.
In this guide we will explain why people are using multi-hop VPNs and how they can help you achieve higher levels of privacy and security. The key factor when considering whether you need a multi-hop VPN is your threat model. How much privacy do you need and want for your unique situation?
Below we are going to go into more detail on this topic, showing you exactly what we mean with multi-hop and double VPN in the context of VPN services. But first, for those in a hurry, let's see which are the best VPN services that offer multi-hop and double VPN features.
The best multi-hop and double VPN services in 2025
Double-hop VPN services (fixed locations, not self-configurable)
- NordVPN – $3.39 per month (with this 76% off coupon); based in Panama; 31 double VPN configurations; 7,800+ total servers (see the NordVPN review)
- Proton VPN – $3.59 per month; based in Switzerland; 113 double VPN (Secure Core) servers; 13,500+ total servers (see the Proton VPN review)
- VPN.ac – $3.75 per month; based in Romania; 30+ double VPN configurations; 30+ total servers (see the VPN.ac review)
Self-configurable VPN services:
- Surfshark – Up to two servers; $1.99 per month; based in the Netherlands (see the Surfshark VPN review)
- Perfect Privacy – Up to four servers, plus the NeuroRouting feature; $8.95 per month; based in Switzerland (Perfect Privacy review)
- OVPN – Up to two servers; $4.22 per month; based in Sweden (see he OVPN review)
- IVPN – Up to two servers; $3.89 per month (but the multi-hop feature is only available in the Pro plan, which starts at $6.11/month); based in Gibraltar
Now let's dive into the details and specifically answer why you need a multi-hop or double VPN.
Surveillance and advanced online anonymity
A multi-hop VPN is a good privacy tool against targeted monitoring and other theoretical attack vectors we will discuss below. It may also be useful for those in dangerous situations, such as journalists or political dissidents living in oppressive countries.
One key question is whether you can trust the data center where the VPN server is located.
VPN services will rent, lease, or colocate servers in data centers all over the world for their network. These servers will be fully encrypted, secured, and under the control of the VPN provider, thereby preventing third-party access to sensitive user data and traffic.
What can the data center see with an encrypted VPN server?
Even with strong encryption of the VPN server, the data center (host) — or perhaps an external state surveillance agency — could potentially monitor incoming and outgoing traffic on the server.
While this may seem alarming, it would still be very difficult for the data center (or third party) to gather useful information because:
- The traffic remains securely encrypted on the VPN tunnel, which right now is considered to be unbreakable (AES-256 encryption with the OpenVPN protocol, for example).
- Correlating outgoing traffic with incoming traffic is extremely difficult. Theoretically, traffic correlation for some users may be possible through advanced statistical analysis and studying traffic patterns. However, this remains difficult, especially on a large scale, even for powerful adversaries.
- Most VPNs utilize shared IPs, with many users on a given server (and IP address) at the same time, with all traffic being mixed. Note: this is also why you should not “roll your own VPN” that only you will be using.
Even though a standard, single-hop VPN configuration will be adequate for the vast majority of users, incoming/outgoing traffic correlation may still be possible — at least in theory.
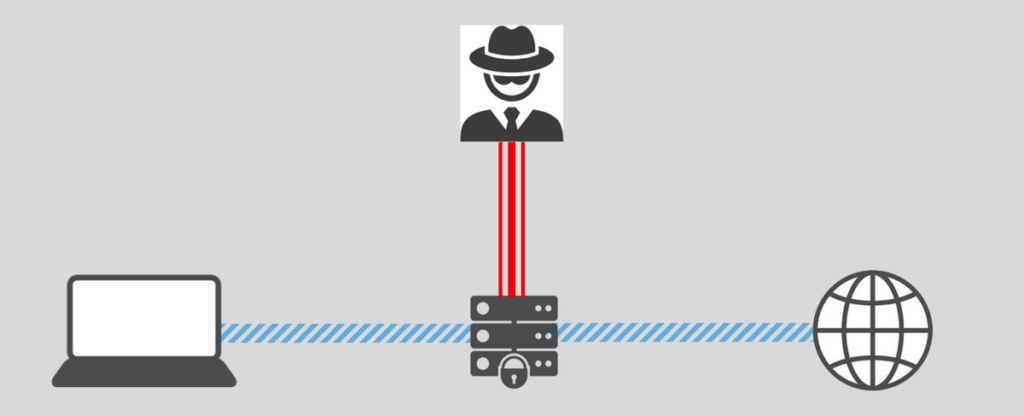
Are data centers really being targeted for traffic correlation attacks?
We have no way to know for sure. In many cases when authorities wanted customer data, they simply went to the data center and physically seized the server:
- Perfect Privacy servers were seized in the Netherlands (no customer data was affected)
- ExpressVPN servers were seized in Turkey (no customer data was affected) — as pointed out in my guide on no logs VPN services
In other cases, some VPNs have cooperated with authorities and handed over user information after being pressured by law enforcement agencies. These cases related to criminal investigations being conducted by US authorities. For example, see the IPVanish logs case and also the PureVPN logging example.
Multi-hop VPN cascade
The first example of a multi-hop VPN we will examine is a “cascade” — where traffic is encrypted across two or more of the VPN's servers.
One provider offering the ability to create custom VPN cascades with up to four servers is Perfect Privacy. Here is a basic visual explanation of how that would work using a four-hop VPN cascade:
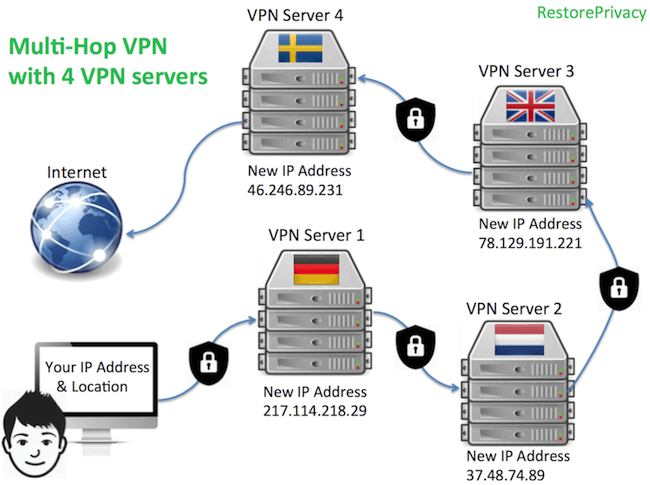
In the picture above, the user's identity is changed at every hop and re-encrypted using OpenVPN 256-bit AES encryption (for example), before the traffic exits the VPN cascade on to the regular internet. With every hop, the new VPN server only gets the previous VPN server's IP address/location — further obscuring and protecting the user's true identity.
Perfect Privacy also makes some interesting points in this article:
With a cascaded connection this [traffic correlation] attack becomes much more difficult because while the ISP/eavesdroper still knows the VPN entry node of the user, it does not know on which server the traffic exits. He would need to monitor all VPN servers and take a guess at which exit node the user is using. This makes it next to impossible to successfully identify users by traffic correlation.
Also it is theoretically possible that an attacker has physical access to the VPN server in the data center. In that case he can possibly execute a de-anonymization attack on the VPN user. A cascaded connection protects against this attack vector: Since the user’s traffic is encapsulated with an additional layer of encryption for each hop in the cascade, no traffic can be read or correlated with incoming traffic.
The attacker would still see outgoing encrypted traffic to another VPN server but he cannot determine whether this is a middle or exit node. To successfully intercept and decrpyt the traffic, the attacker would need to have physical access to all hops in the cascade simultaneously. This is practically impossible if the hops are in different countries.
Using a multi-hop setup with strong encryption and other privacy tools provides you with a high level of online anonymity and security.
Double VPN services
Double VPN servers are a unique feature with some services.
With a double-VPN configuration, the first server could see your originating IP address, and the second server could see your outgoing traffic, but neither server would have both your IP address and your outgoing traffic.
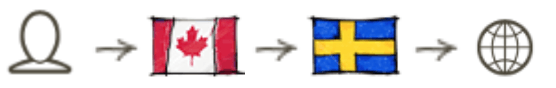
This setup should still offer decent performance, and it will also offer a higher level of security and privacy over a single-hop setup.
Based on my tests, if you want the most features with your double VPN, then either NordVPN or Surfshark would be a good decision.
Can you still get fast speeds with double VPN?
Are double VPN servers fast?
In my own tests, I have found that you can still get excellent speeds with some double VPNs (but not all).
The fastest double VPN we have tested was with NordVPN on a USA-Canada server configuration at 614 Mbps download speeds, as you can see with the speed test result below.
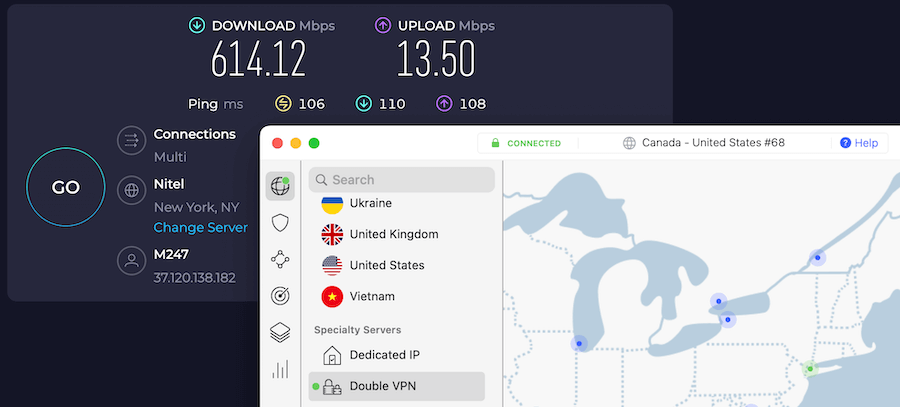
You can see server options and prices on the NordVPN website here.
There are two types of double VPN (or multi-hop) setups: fixed configurations, where the VPN provider pre-selects the server pairs and you can’t customize the route, and self-configurable setups, which let you manually choose both the entry and exit servers for greater control over your connection path.
Self-configurable multi-hop VPNs
A self-configurable multi-hop VPN allows you to individually select the servers in the VPN cascade from the whole server network of a provider. Here are a few VPN services offering this feature.
1. Surfshark — Dynamic MultiHop with 2 servers
| Total nr. of servers | 3200+ |
Surfshark offers a standard double VPN setup through its “MultiHop” feature, which routes your internet traffic through two servers instead of just one. This setup uses fixed server pairs, meaning Surfshark pre-selects the entry and exit servers for each MultiHop route. For example, you might see a connection path like “USA via UK” or “Germany via Singapore.” While this approach enhances privacy by masking your IP address twice and making tracking more difficult, it doesn’t allow for custom configuration — you can only choose from the list of available MultiHop pairs.
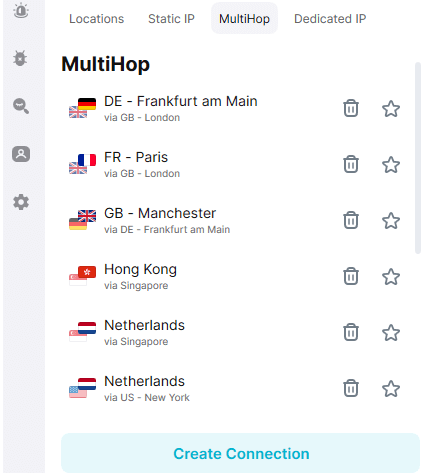
To give users more flexibility, Surfshark also includes a “Dynamic MultiHop” feature. This option lets you create your own custom double VPN connection by manually selecting both the entry and exit servers from Surfshark’s global network. It’s ideal for users who want more control over their traffic routing — for example, to optimize speeds, reduce latency, or target specific countries.
Find out more in our extensive Surfshark review.
2. Perfect Privacy — Multi-hop VPN with up to 4 servers
| Total nr. of servers | 35+ |
Perfect Privacy allows you to create self-configurable VPN cascades with up to four hops directly in the VPN client. I tested this feature out for the Perfect Privacy review with both the Windows and Mac OS clients and found everything to work well.
Here is a four-hop VPN server cascade: Frankfurt >> Copenhagen >> Calais >> Malmo
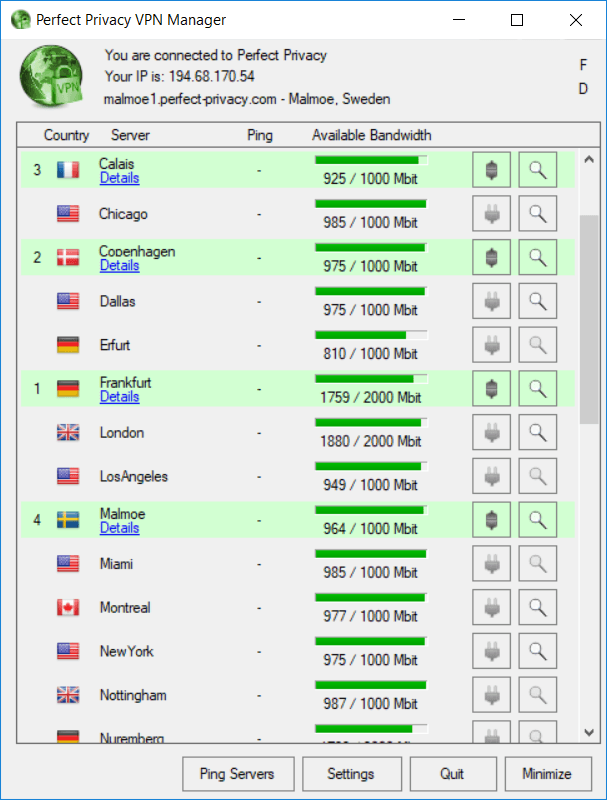
With this configuration, your true identity and IP address will be protected behind four different encrypted VPN servers.
Every website you visit will only see the server details of the last hop in the VPN cascade. You can simply enable the multi-hop configuration setting, and then dynamically add or remove VPN servers in the VPN client. The last server in the cascade will reflect your publicly-visible IPv4, IPv6, and DNS resolvers.
Perfect Privacy is also one of the few VPNs with IPv6 support.
See our Perfect Privacy review for more information.
3. OVPN (two hops)
| Total nr. of servers | 32 |
OVPN is a privacy-focused VPN service based in Sweden, known for its strong commitment to security and minimal data retention. It operates on a no-logs policy, runs all servers on RAM, and supports advanced features like port forwarding. With open-source apps and a transparent approach to privacy, OVPN is a solid choice for users who prioritize anonymity and data protection.
OVPN offers multi-hop configurations on its longer-term plans (12- and 36-month options), and you can route traffic over two hops. It also supports IPv6.
Get more details in our dedicated OVPN review.
4. IVPN (two hops)
| Total nr. of servers | 88 |
IVPN is a VPN service based in Gibraltar. It offers users the ability to route traffic over two hops, but does not support IPv6. However, IVPN does support the WireGuard VPN protocol.
Like some of the others we've covered, IVPN prices are above-average, and you need to get the even pricier Pro plan to be able to use the multi-hop feature. However, it is also a fully-featured VPN with clients for all major operating systems and devices.
Dynamic multi-hop VPN configurations (NeuroRouting)
Another interesting development in multi-hop connections and advanced security is NeuroRouting.
This is a unique feature that was officially launched in October 2017 by Perfect Privacy.
NeuroRouting is a dynamic, multi-hop configuration that allows you to simultaneously route your traffic across numerous unique/different server configurations in the network. Here is an overview of this feature:
- Dynamic – Your internet traffic is dynamically routed across multiple hops in the VPN server network to take the most secure route. The routing path is based on TensorFlow, an open-source software for machine learning, and data remains in the network as long as possible. Being based on TensorFlow, the network continually learns the best and most secure route for a given website/server.
- Simultaneous – Each website/server you access will take a unique route. Accessing multiple different websites will give you numerous, unique multi-hop configurations and IP addresses at the same time, corresponding to the location of the website server and the last VPN server in the cascade.
- Server-side – This feature is activated server-side, meaning every time you access the VPN network, NeuroRouting will be active (unless you disable it from the member dashboard). This also means it will work on any device – from routers to MacOS and Android. Finally, NeuroRouting works with OpenVPN (any configuration) as well as IPSec/IKEv2, which can be used natively on most operating systems.
The image above shows NeuroRouting in action, with the user connected to a VPN server in Iceland, while accessing four different websites located in different parts of the world.
You can learn more about NeuroRouting here.
Multi-hop VPN chains with different VPN providers
Ok, what if you want to add different VPN providers to the mix?
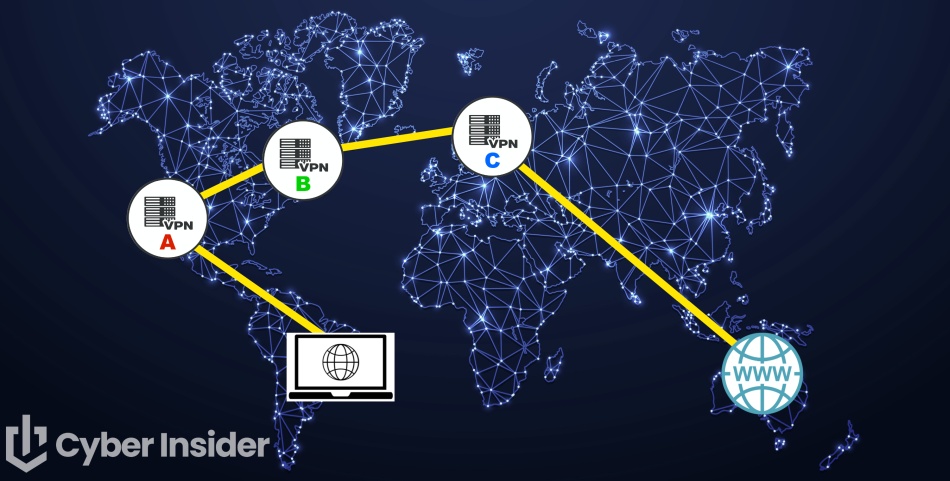
Another option is to create chains using more than one VPN provider at the same time. This is sometimes referred to as a “VPN within a VPN” or a “nested chain” of VPNs.
This is a good option for protecting users against a VPN that may be compromised, as well as a VPN server that may be compromised.
Here are a few different ways to do this:
VPN 1 on router > VPN 2 on computer/device
This is an easy setup with a VPN on a router and then using a different VPN service on your computer or device, which is connected through your VPN router. Choosing nearby servers will help minimize the performance hit with this setup.
VPN 1 on computer (host) > VPN 2 on virtual machine (VM)
This is another setup that can be run without much hassle. Simple install VirtualBox (free), install and set up the operating system within the VM, such as Linux (free), and then install and run a VPN from within the VM. This setup can also help protect you against browser fingerprinting by spoofing a different operating system from your host computer.
You can also add a router to the mix, using three different VPN services:
VPN 1 on router > VPN 2 on computer (host) > VPN 2 on virtual machine (VM)
Lastly, you could also create virtual machines within virtual machines, or daisy-chain virtual machines. If you are new to virtual machines, there are many videos available online that explain setup and use.
Virtual machines are a great privacy and security tool, since they allow you to create isolated environments for different purposes — also known as compartmentalization. Within VirtualBox, you can create numerous different VMs using various operating systems, such as Linux, which you can install for free. This also allows you to easily create new browser fingerprints with each additional VM, while also concealing your host machine's fingerprint.
Use Linux — When setting up VMs, I'd recommend running a Linux OS, for the following reasons:
- Free
- Open source
- More private and secure than Windows or Mac OS
Ubuntu is user-friendly and easy to get going in minutes.
Note: Be sure to disable WebGL in Firefox with all your VMs (see the instructions in the Firefox privacy guide using about:config settings). This will prevent graphics fingerprinting since all the VMs will be using the same graphics driver.
We cover the topic of nested VPN chains more in the Advanced Privacy Guides series.
Mirimir has also written some guides on setting up nested VPN chains:
- How to create dynamic nested VPN chains.
- A series of guides about using nested VPN chains and Tor.
When should you not use multi-hop VPN chains?
If your top priority is speed and performance, I would recommend using a single-hop VPN. So when would you want to prioritize speeds? Here are a few situations:
- If you are using a VPN for streaming, especially if you are streaming in high definition (HD)
- When using a VPN for torrenting and P2P downloads
- Watching a Netflix with a VPN (or using any other streaming service)
- Using a VPN for gaming where you will need fast ping / low latency
Conclusion on multi-hop VPNs in 2025
A multi-hop VPN configuration is an excellent way to achieve a higher level of privacy and security while also distributing trust across data centers and adding extra layers of encryption.
However, you should also understand that even when routing traffic over numerous hops, you are still placing all your trust in a single VPN service. Therefore, this won't protect you if the VPN itself is compromised. To get around this issue and further distribute trust, you can use nested VPN chains, which we discuss more in our advanced privacy guides.
Several VPNs offer easy-to-use multi-hop features across devices. For example, Surfshark provides a Dynamic MultiHop feature that allows you to create custom server-to-server routes directly in the app — ideal for users who want more control over how their traffic is routed.
For an even more seamless experience, Perfect Privacy offers NeuroRouting, a server-side feature that automatically applies a dynamic multi-hop configuration to all devices connected to the VPN. Once activated in the member dashboard, it works with any device, protocol, or app — no manual configuration needed.
Ultimately, multi-hop VPNs are a powerful tool in your privacy arsenal, especially when combined with the right provider and thoughtful configuration.

Leave a Reply