VPN provider Surfshark has successfully completed a comprehensive infrastructure security audit conducted by Polish cybersecurity firm SecuRing, uncovering two medium-severity issues.
The assessment focused on the resilience of Surfshark's systems against unauthorized access and disruptions, confirming that the company’s backend infrastructure demonstrates strong resistance to real-world attack scenarios with no critical security issues discovered.
The audit was conducted in late 2025 and focused on black-box penetration testing against Surfshark’s network infrastructure. SecuRing's specialists operated without insider knowledge or elevated access, aiming to simulate realistic external threats. The auditors probed for weaknesses that could impact service availability, data integrity, and client confidentiality. The engagement also evaluated the overall security posture, including server hardening, misconfiguration risks, and transport layer protections.
Surfshark is among the most prominent VPN providers globally, offering privacy-preserving tools such as VPN, DNS-based ad blocking, and data breach monitoring. As part of its broader transparency efforts, Surfshark has undergone previous audits of its no-logs policy and server architecture, though this latest review focused specifically on infrastructure-level defenses.
Main findings
The key technical finding of the audit involved a TLS configuration inconsistency on one of Surfshark’s servers. While the system primarily enforced modern encryption standards such as TLS 1.3 with strong cipher suites, SecuRing noted that legacy cipher support had not been entirely disabled. This could, under certain conditions, have allowed downgrade attacks or weakened session confidentiality, especially if an attacker was positioned to intercept client traffic. Surfshark responded by removing the legacy options entirely and aligning the configuration with best practices, ensuring strict use of strong cipher suites across its fleet.
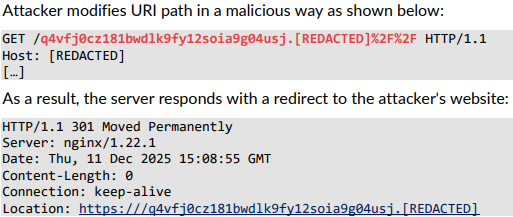
In addition to the TLS-related configuration weakness, SecuRing identified a URL parsing flaw that could be exploited for malicious redirection. By crafting a request with a specially formatted URI, an attacker could trigger the server to issue an HTTP 301 redirect to an attacker-controlled domain. This behavior stemmed from the server misinterpreting parts of the path as an external URL due to insufficient sanitization, potentially exposing users to phishing or traffic hijacking. The issue was mitigated by adjusting URI handling logic to prevent unintended redirects to untrusted destinations.
Surfshark
Aside from this, the audit uncovered no critical or high-risk vulnerabilities. All other identified issues were considered low in severity and posed no immediate threat to client data or system availability.
SecuRing's methodology included network scanning, service fingerprinting, brute-force and enumeration attempts, and targeted attacks against publicly exposed infrastructure. The firm concluded that Surfshark’s internal segmentation, authentication controls, and automated monitoring mechanisms functioned as intended and provided robust defensive depth.
While the audit did not result in the release of the full technical report to the public, Surfshark shared a summary containing sufficient details with CyberInsider to allow us to verify the findings. The company emphasized that it views audits not as promotional tools but as part of an ongoing commitment to operational security and accountability.







SURFSHARK fails even in 2026 to this day Jan 2026 to have ONLY BETA KILLSWITCH that malfunctions , including shutting down internet connection!!! PLUS, with every single computer login, SURFshark asks for USER’s computer login before connecting!!!