
An apparent coordinated attack has forced Ubisoft to shut down Rainbow Six Siege servers and the in-game marketplace, following reports of widespread unauthorized bans, currency exploits, and backend compromises.
Ubisoft acknowledged a serious service disruption affecting Rainbow Six Siege, a competitive tactical shooter with a large global player base. The company confirmed the incident via its official X account, stating that its teams are investigating the issue and have taken down both the game and its associated marketplace as a precaution. According to a follow-up update, all transactions since 11:00 AM UTC are being rolled back, and Ubisoft has reassured players that no one will be banned for spending the erroneously granted credits.
Launched in 2015, Rainbow Six Siege is one of Ubisoft’s flagship multiplayer titles, boasting tens of millions of registered players worldwide. Known for its competitive gameplay and esports scene, the game operates a live-service model with a robust in-game economy involving credits, renown, and cosmetic purchases.
While Ubisoft has not yet publicly disclosed the root cause of the incident, a wave of user reports paints a grim picture of what appears to be a major backend compromise. Players reported sudden bans, a flood of in-game currency and premium items, including exclusive developer skins, and what appeared to be unauthorized control of the game’s ban feed.
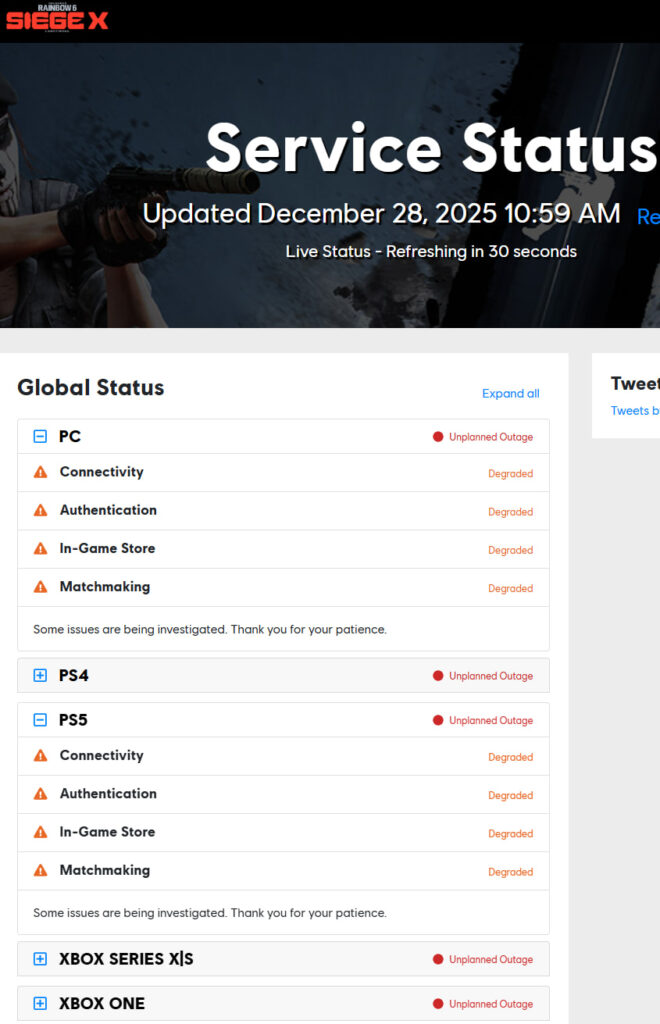
The attack has resulted in unplanned outages across all platforms, including PC, PlayStation 4/5, and Xbox Series X|S/One, according to the official Rainbow Six Siege service status page. Core services such as authentication, connectivity, in-game store access, and matchmaking are currently degraded or offline, with Ubisoft confirming that investigations are ongoing.
Adding complexity to the situation, the cybersecurity group vx-underground has shared unverified information suggesting the involvement of at least four distinct hacker groups. According to them, the first group is believed to have compromised a live Rainbow Six Siege service, granting them the ability to ban players, modify inventories, and distribute vast amounts of in-game currency, reportedly totaling over $339 trillion. This aligns with what many players have observed firsthand.
A second group, allegedly separate from the first, is said to have exploited a misconfigured MongoDB database via the MongoBleed vulnerability. They purportedly pivoted from this initial access to Ubisoft’s internal Git repositories, exfiltrating source code and proprietary assets spanning from the 1990s to the present. This claim has not been independently verified, but vx-underground rates it with “medium to high confidence” based on cross-verification with unnamed sources.
A third group has emerged claiming to have accessed user data through a similar MongoDB exploit. This group is reportedly attempting to extort Ubisoft and has surfaced on Telegram channels.
A fourth group has accused the second group of deception, claiming they have had long-standing access to Ubisoft's codebase and are now using the recent chaos to justify a planned full-scale leak.
Ubisoft’s response and status
Ubisoft has officially confirmed a ban wave initiated by its R6 ShieldGuard system, but clarified it is unrelated to the current incident. They have also stated that the “ban ticker” feature was disabled in a previous update, meaning any messages seen recently were not triggered by Ubisoft itself. This appears to support the theory that attackers gained some level of internal access, allowing them to impersonate backend actions.
As of December 28 at 10:59 AM local time, all platforms remain affected, and core online functionality is still disrupted. Ubisoft has not confirmed a timeline for resolution or commented on the unverified claims regarding an internal data compromise.
Until Ubisoft confirms that systems are fully restored and secure, users are strongly advised not to log into the game or interact with in-game purchases or earned currency. As the situation involves a potential backend compromise and unverified claims of data theft, players should refrain from spending in-game currency earned during the outage, enable two-factor authentication (2FA) on their Ubisoft accounts, and remain alert for phishing attempts or suspicious login activity.







Leave a Reply