
Researchers from ETH Zurich have identified serious architectural weaknesses in three leading cloud-based password managers, Bitwarden, LastPass, and Dashlane, demonstrating that a fully compromised server could expose and even modify users’ stored credentials.
Collectively, Bitwarden, LastPass, and Dashlane account for more than 60 million users and roughly 23% of the market.
In controlled tests, the team was able to recover passwords and tamper with vault data, challenging long-standing “zero-knowledge encryption” claims made by vendors.
The findings were published today in a technical paper and disclosed to vendors under a coordinated 90-day process.
Putting zero-knowledge claims to the test
The research, conducted by ETH Zurich and Università della Svizzera italiana in Lugano, evaluated the products under what is known as a “fully malicious server” threat model, assuming attackers had already breached the provider’s infrastructure and could arbitrarily manipulate server responses to users’ apps and browser extensions.
Cloud-based password managers store users’ encrypted “vaults” on remote servers, allowing synchronization across devices and secure sharing between users. Vendors typically advertise “zero-knowledge encryption,” meaning vault contents are encrypted locally and cannot be accessed by the provider, even if servers are breached.
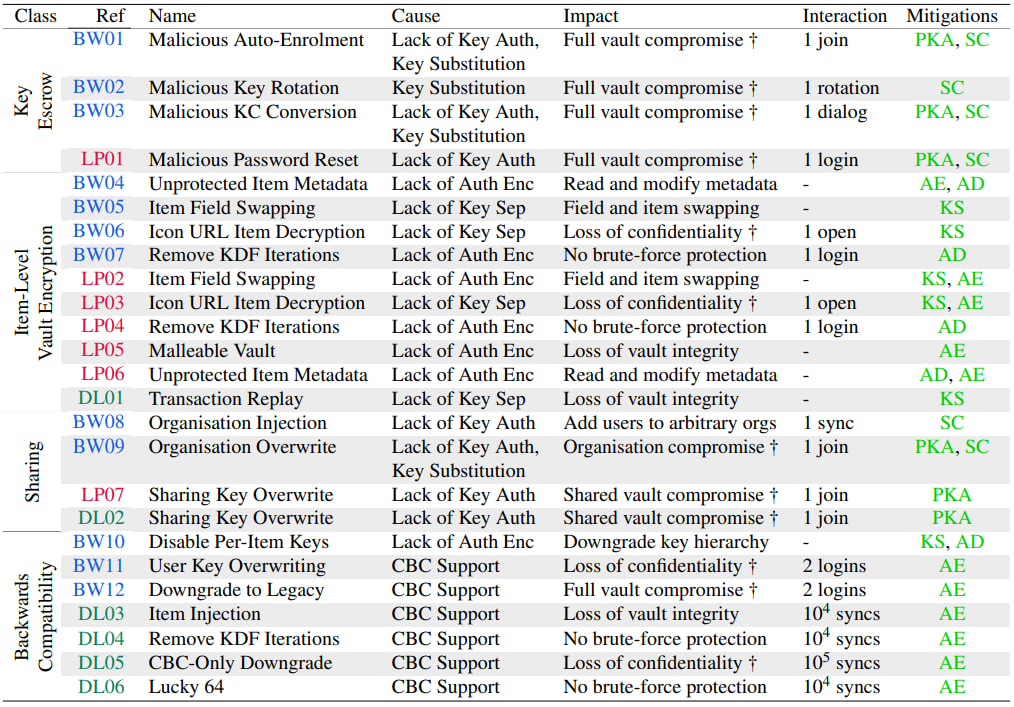
However, the ETH researchers found that, in practice, this protection breaks down if the server actively manipulates how data is delivered to clients. The researchers identified:
- 12 attacks against Bitwarden
- 7 attacks against LastPass
- 6 attacks against Dashlane
Many of these attacks enabled recovery of stored passwords. Others allowed vault integrity violations, such as injecting new items, modifying metadata, or silently weakening cryptographic protections.
ETH Zurich
Rather than exploiting traditional bugs like buffer overflows, the attacks targeted architectural design decisions.
In several cases, the server could substitute cryptographic keys during account recovery or password reset workflows. For example, in Bitwarden and LastPass enterprise recovery features, the client retrieved public keys from the server without cryptographic authentication. A malicious server could replace those keys with attacker-controlled ones, tricking the client into encrypting vault keys for the attacker.
Other weaknesses stemmed from item-level encryption. Instead of encrypting the entire vault as a single authenticated object, many managers encrypt individual fields separately. This design allows flexibility and efficient syncing, but the researchers showed it can enable “cut-and-paste” style attacks, swapping encrypted fields between entries or manipulating unprotected metadata.
LastPass stood out for relying on AES-CBC encryption without built-in integrity protection for vault items, allowing classic ciphertext manipulation. Meanwhile, Bitwarden and Dashlane maintained legacy cryptographic paths for backward compatibility. The researchers demonstrated downgrade attacks that forced clients to fall back to weaker encryption modes.
Another class of attacks involved modifying password-based key derivation settings stored on the server. By lowering iteration counts for PBKDF2 during login, a malicious server could significantly reduce the computational cost of brute-forcing a user’s master password.
The team emphasized that most attacks required only routine user actions, such as logging in, syncing, opening a vault, or joining an organization.
Vendors’ response
Bitwarden published a response today stating that the ETH audit focused on a hypothetical “fully malicious server” scenario and that all identified issues have been addressed. The company said most findings were categorized as medium or low impact and required an attacker to already have full server control. Bitwarden emphasized that it has never suffered a breach and credited its open-source architecture for enabling independent scrutiny.
Dashlane similarly confirmed it worked with researchers ahead of publication and deployed fixes in browser extension version 6.2544.1 (released November 5, 2025). The company said it found no evidence of exploitation and noted that some issues involved legacy cryptography maintained for backward compatibility, which has since been removed.
LastPass has not yet issued a public statement at the time of publishing, but they released an announcement later.
Update 2/17 – Added link to LastPass announcement.







Leave a Reply