
The creators of the Raccoon Stealer malware-as-a-service (MaaS) have announced the launch of version 2.3.0, which adds several features that enhance its stealthiness and ease of use.
Via a post on the hacking forum XSS, the malware’s operators toot their return to cybercrime forums and invite fellow cybercriminals to renew their subscriptions to the MaaS program and take advantage of key new features.
Raccoon is an information stealer sold to hackers for a subscription of $200 per month, or $75 per week, giving them access to a central panel that receives “logs,” which are stolen data from successfully compromised systems.
The data Raccoon targets include account credentials, credit cards, cookies, and internet history stored on web browsers (32 supported), email clients (3), cryptocurrency wallet apps (6), and more. The malware can also target specific directories on infected systems, create files, and obtain decryption keys for encrypted databases.
New in Version 2.3.0
According to a post by cybersecurity firm Cyberint, the latest version of Raccoon Stealer promoted on underground forums features updates that improve the tool’s usability and ability to evade detection.
The first new feature is a powerful, quick search tool implemented on the administrator panel, giving users an easy way to locate specific files, names, URLs (for cookies), and other data types from vast databases. This not only makes retrieving specific logs easier but can also help create specialized data packs that can be sold for a premium on the dark web.
Another feature that improved the tool’s user-friendliness is a new log statistics tool that generates graphs on the user’s activity and campaign success, helping them develop more effective strategies for penetrating specific markets.
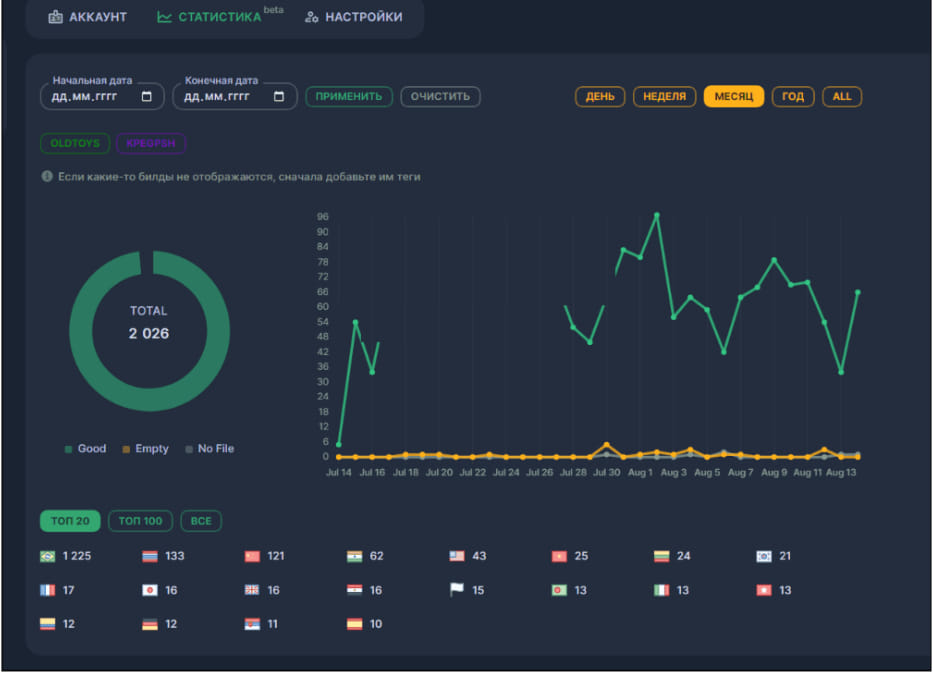
Raccoon 2.3.0 has also introduced features that block security analysts, like an automatic filter that can identify IP addresses used by crawlers and bots created to monitor network traffic from the stealer and report to cyber-intelligence platforms. Additionally, the malware authors have added a risk-evaluation system on the dashboard to inform the user of suspicious activity from specific IP addresses, which carry activity signs pointing to them being honeypots.
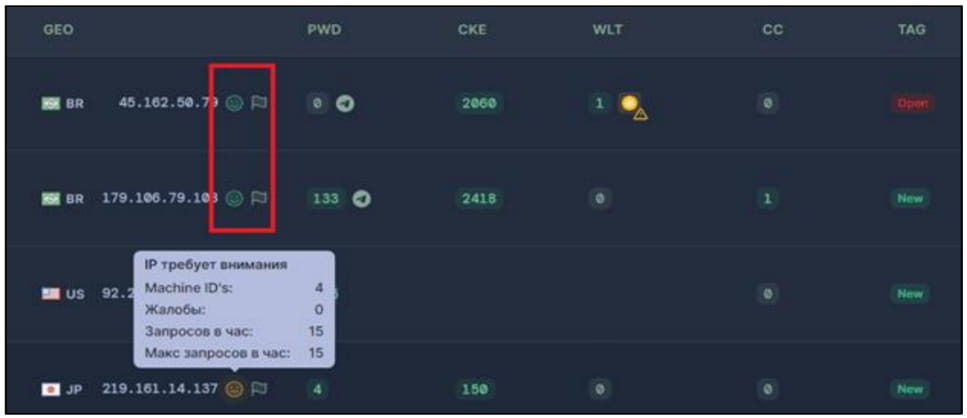
“If this system identifies suspicious behavior, it automatically deletes records associated with those activities and updates the information on each client pad. This makes it harder for security tools that use automation and bots for the detection of malware.”Cyberint
Raccoon Holding Strong
Raccoon Stealer appeared online over four years ago and has remained one of the top most used information stealer malware families out there, despite the increasing competition from novel MaaS operations that often try to break into the space with better pricing and technical superiority. In June 2023, a Group-IB report examining ChatGPT logs available for purchase on the DarkWeb placed Raccoon Stealer in the first spot of the most prolific malware.
However, the operation has recently faced challenges and upheavals, unwelcome characteristics in the cybercrime realm. In March 2022, Raccoon’s operators paused their activities due to the death of a core developer in the Russo-Ukrainian war. Yet, by June 2022, Raccoon Stealer 2.0 was unveiled, introducing significant enhancements and positioning the MaaS operation for a fruitful year. But in October 2022, Mark Sokolovsky, one of Raccoon’s primary operators from Ukraine, faced charges in a U.S. court. This stirred concerns about potential information leaks to law enforcement, which could compromise the malware tool’s users.
The launch of version 2.3.0 poses a significant threat to internet users globally. Its importance to Raccoon users is not only due to the malware’s enhanced features but also because it reaffirms the MaaS operation’s robust and active status.







Fully undetectable crypter bypass Windows Defender in 2024
Malware can bypass all major antivirus like Windows Defender McAfee and etc with Data Encoder Crypter. Also, Chinese users can bypass 360 Total security in 2024 with this FUD Crypter.
Thank you Heinrich Sir for the information. This is why one should have good paid antivirus on one’s PC and smartphone and should practice good cyber security hygiene and should also prefer to run Windows as non-administrator for improved security. These malwares are very dangerous.
Wait windows can be run as non admin? Does it have to run something like linux as well?