
A new cybercrime toolkit dubbed ErrTraffic v2 is weaponizing psychological manipulation at scale, exploiting user trust through highly convincing browser-based deception.
According to Hudson Rock, this tool represents a major shift toward commoditized social engineering, offering novice criminals an effective infection system for just $800.
The threat was uncovered in early December 2025, when researchers at Hudson Rock identified a forum advertisement on a prominent Russian-language cybercrime marketplace. The post, published by a threat actor using the alias LenAI, promoted ErrTraffic v2.Panel, a full-featured ClickFix deployment suite. The panel allows attackers to craft fake “glitch” scenarios in victims' browsers, tricking them into manually executing malicious PowerShell commands under the guise of system recovery.
ClickFix is an attack type where, instead of delivering malware via an automatic download, attackers present what appears to be a critical system error, urging users to manually fix the problem by pasting code into system-level tools like Windows Run or PowerShell. As a result, the malicious payload executes with full user privileges, often bypassing antivirus and behavioral monitoring solutions.
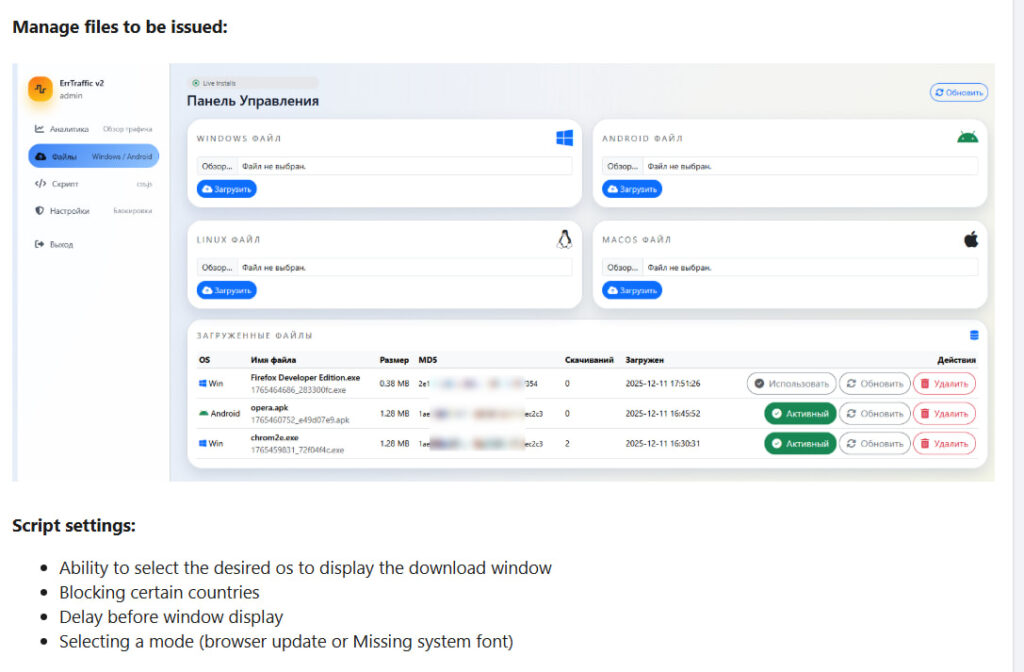
The ErrTraffic system is designed to be deceptively user-friendly. Built on a standard LAMP stack (Linux, Apache, MySQL, PHP), the attacker-hosted dashboard mimics commercial SaaS platforms in look and feel. Once deployed, attackers inject a single line of JavaScript into a compromised site.
Hudson Rock
This script is responsible for delivering the visual payload, a fake glitch effect that visually disrupts the website's content. Victims are presented with corrupted or unreadable text, often using “Zalgo” characters, triggering anxiety and urgency. A prominent “Fix Glitch” button then initiates the infection chain.

Hudson Rock
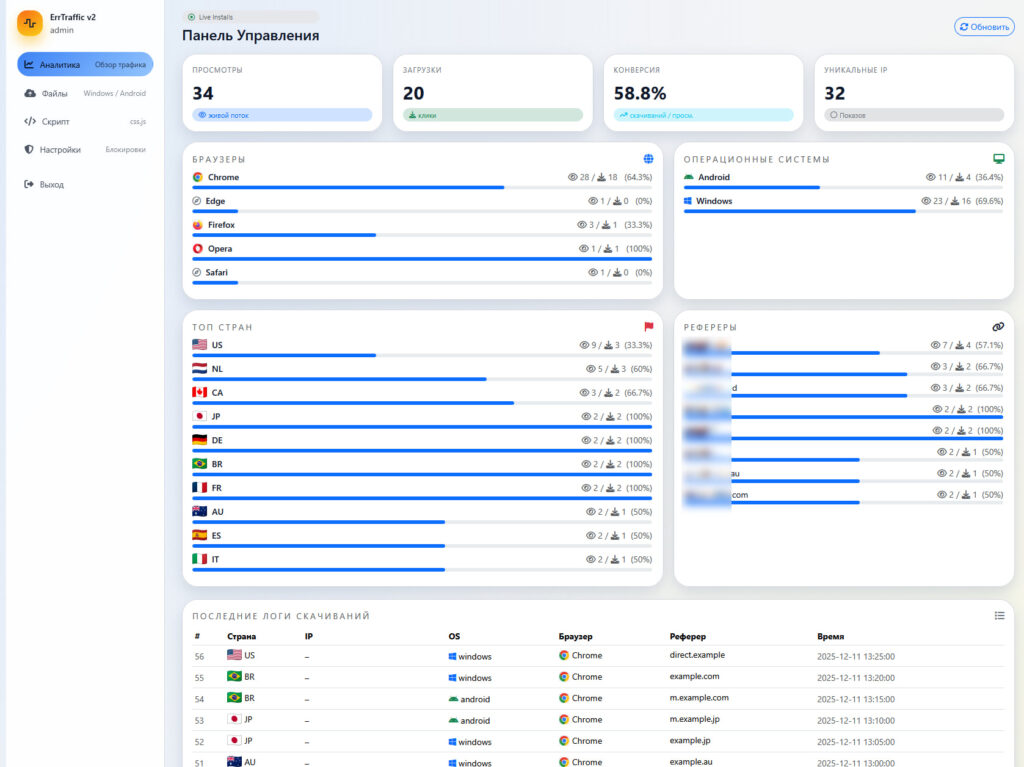
In terms of infrastructure, ErrTraffic operates as a Traffic Distribution System (TDS). Attackers upload malware payloads for Windows, Android, macOS, or Linux, which are selectively delivered based on the victim's operating system. Supported payloads include infostealers like Lumma and Vidar for Windows, Cerberus banking trojans for Android, and likely Atomic Stealer (AMOS) for macOS users.
Hudson Rock
In observed test campaigns, ErrTraffic achieved nearly 60% conversion rates among victims who interacted with the lure, an unprecedented figure in the malware ecosystem.
The actor LenAI, unrelated to the legitimate AI product of the same name, registered on the cybercrime forum in early December 2025 and currently holds “Seller” status. According to Hudson Rock, the complete ErrTraffic package sells for $800, a relatively low price given its capabilities. Notably, the tool includes built-in geofencing, excluding delivery to users in CIS countries (Russia, Belarus, Kazakhstan, etc.), a standard tactic among Russian-speaking threat actors to avoid local prosecution.







Leave a Reply