
A malware campaign dubbed GhostPoster, which used steganography to embed malicious code in extension logos, has infected over 50,000 Firefox users across 17 add-ons.
The campaign, discovered by Koi Security, was exposed while investigating an innocuous-looking Firefox extension called Free VPN Forever, which had accumulated over 16,000 installations since its debut in September 2025. Analysis tools flagged it for anomalous behavior, such as reading the raw byte data of its own logo file, a PNG icon named logo.png, and searching for a suspicious marker.
Koi Security
Multi-stage infection chain
Stage 1: Logo
The extension's logo.png contained more than just image data. Hidden after a marker string of three equals signs (===) was an obfuscated JavaScript loader. This steganographic technique allowed the malware to evade static detection tools and human reviewers alike, as the logo rendered normally in the browser while concealing the first stage of the attack.
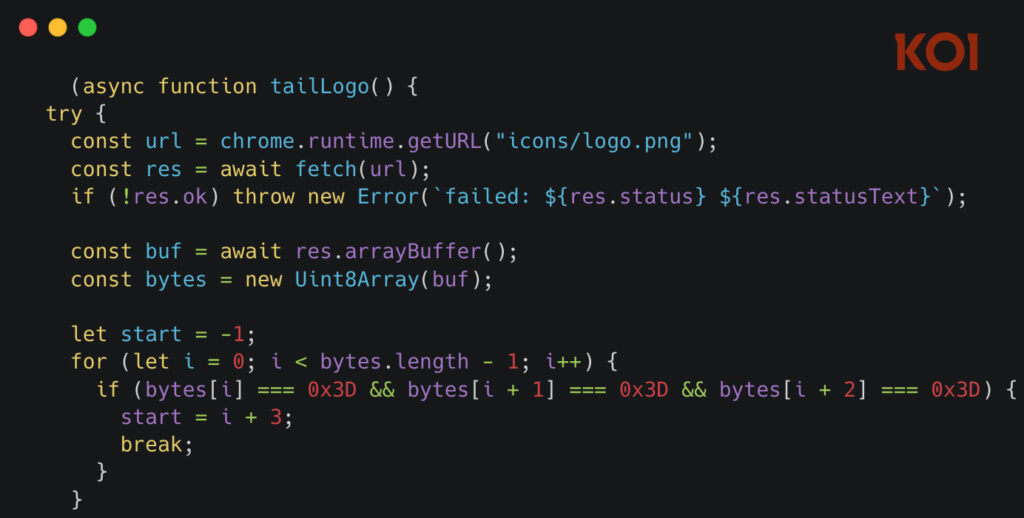
Koi Security
Stage 2: Loader
Once extracted, the loader contacted a primary command-and-control (C2) server at www.liveupdt.com, or a fallback at www.dealctr.com. It didn't fetch malware on every check-in, instead using randomized timing and 10% payload delivery rates, a calculated strategy to avoid drawing attention from network monitoring tools.
Stage 3: Cipher
When the final payload was delivered, it came encrypted via a custom encoding scheme that reversed letter casing, swapped digits 8 and 9, and base64-decoded the result. The decrypted code was then XOR-encrypted using a key tied to the extension's runtime ID and saved to browser storage, ensuring persistence.
Stage 4: Payload
The payload granted attackers extensive control over the user's browser, enabling a wide range of malicious activities:
- Affiliate link hijacking on e-commerce sites like Taobao and JD.com.
- Google Analytics-based tracking, including infection timestamps, merchant sites visited, and browser fingerprints.
- Security header stripping, removing protections like Content-Security-Policy and X-Frame-Options across all sites visited.
- CAPTCHA bypass techniques, using overlays, GitHub-hosted solvers, or Baidu account status.
- Invisible iframe injection for ad fraud and further tracking, with lifespans as short as 15 seconds.
The GhostPoster campaign spans at least 17 Firefox extensions, all tied to the same infrastructure and behavioral patterns. Beyond Free VPN Forever, others include “screenshot-saved-easy”, “weather-best-forecast”, “google-translate-pro-extension”, and “dark-reader-for-ff”.
Some used steganography, while others downloaded obfuscated scripts or used encoded eval() calls. These variations suggest active experimentation, testing different evasion and monetization methods.
Despite the differences in delivery, all extensions communicated with the same backends at liveupdt.com and dealctr.com, and in some cases, used additional domains like mitarchive.info and CAPTCHA helpers from refeuficn.github.io.
Mozilla's Firefox Add-ons marketplace, typically seen as more privacy-conscious than Chrome's Web Store, remains vulnerable to these advanced threats. All 17 malicious extensions passed Mozilla's review process and are still publicly available at the time of Koi's report.
Only yesterday, Koi Security disclosed that Urban VPN Proxy, with over 8 million users, was harvesting AI chat logs from services like ChatGPT and reselling them to third parties. Prior to that, FreeVPN.One was found taking full-page screenshots and exposing sensitive user data.







horrible that this happened but you have admire the technique.