
A recent investigation by Huntress researchers has unveiled a previously unreported macOS variant of the LightSpy malware, initially mistaken for an iOS threat in a BlackBerry report. This revelation highlights the evolving threat landscape for macOS users, once considered less vulnerable to such attacks.
The discovery was initially sparked by BlackBerry's April 11, 2024, report about a VirusTotal upload of what was thought to be an iOS version of LightSpy. However, subsequent analysis by Huntress researchers showed that the sample was, in fact, targeting macOS, specifically running on Intel macOS devices or Apple Silicon devices with Rosetta 2 enabled.
Technical details confirmed by Huntress include the malware's compilation for the x86_64 architecture, rendering it incompatible with the ARM-based architecture of iPhones. The technical analysis further revealed that the macOS variant employs a sophisticated structure similar to its iOS counterpart, involving a dropper that downloads multiple dynamically loaded modules (dylibs) containing the malicious functionalities.
macOS LightSpy details
The macOS variant shares many operational similarities with the previously known iOS version but exhibits more refined development practices and improved operational security.
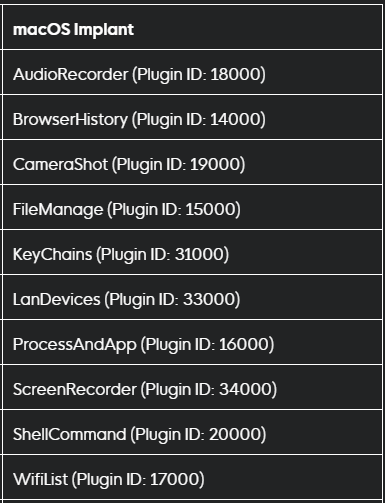
LightSpy for macOS showcases a range of capabilities through various plugins. Each plugin is designed to perform specific tasks, such as audio recording, browser history extraction, and keychain access, indicating a high level of sophistication and targeted espionage.
Specifically, Huntress highlights the following plugins and features:
- Data Extraction: LightSpy extracts browsing history, keystrokes, and media files.
- Keychain Access: It accesses the macOS keychain to retrieve passwords and secure credentials.
- Audio Recording: Includes a plugin for covert audio recording via the device's microphone to capture conversations and nearby sounds.
- File Management: The FileManage plugin manipulates files, allowing downloading, uploading, deletion, and modification for data extraction or payload deployment.
- Device Information Collection: Gathers comprehensive details about the device's system settings, hardware, and network configurations to tailor attacks and evade detection.
- Webcam Access: Some variants can access the webcam to record video.
- Network Information: Scans for local network and device details, aiding in lateral movement and identifying additional potential targets within the network.
Huntress
Defense recommendations
Apple's recent security enhancements across their operating systems, including Lockdown Mode and evolving XProtect features, are crucial in defending against such threats. Users are urged to keep their devices updated and remain vigilant against possible spyware attacks.
For macOS users, it is recommended to utilize available detection tools and maintain strict software update policies to mitigate the risk posed by such sophisticated malware frameworks.
Huntress has also provided YARA and Sigma on its GitHub repository to help detect potential use of this macOS LightSpy variant.







Leave a Reply