
A newly discovered phishing campaign is targeting LastPass users with convincingly crafted emails urging recipients to “create a backup” of their password vaults ahead of a purported maintenance schedule.
The campaign, identified on January 19, 2026, has been flagged by LastPass’ Threat Intelligence, Mitigation, and Escalation (TIME) team as an active and ongoing threat.
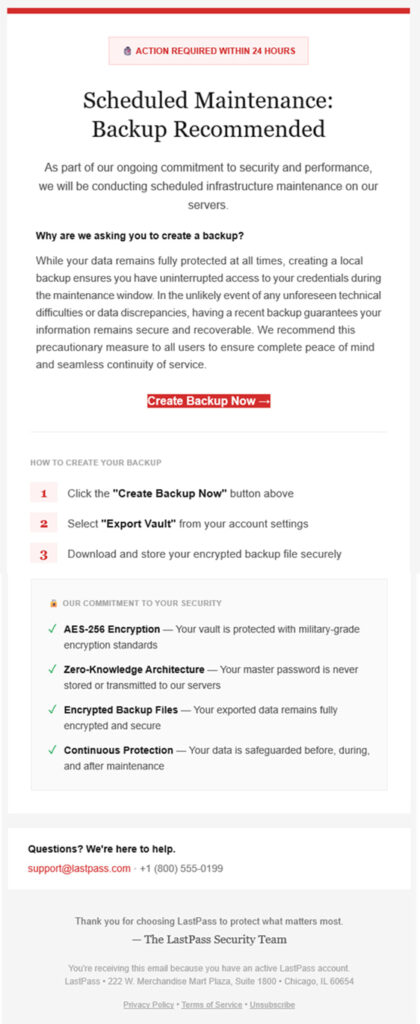
The phishing emails mimic LastPass's official branding and claim that users must take urgent action within 24 hours to avoid losing access to their stored credentials. While the emails appear legitimate, complete with claims of military-grade encryption and instructions for exporting encrypted backup files, they are in fact designed to redirect victims to a phishing site that aims to steal credentials.
The TIME team began receiving reports from vigilant users on January 19, shortly before the US holiday weekend. This timing, likely intentional, leverages reduced staffing at many firms to prolong detection and response. The emails were sent from various suspicious domains such as:
- support@sr22vegas[.]com
- support@lastpass[.]server3
- support@lastpass[.]server7
- support@lastpass[.]server8
The phishing emails used misleading subject lines like “Important: LastPass Maintenance & Your Vault Security” and “Backup Your Vault (24-Hour Window)” to create urgency.
LastPass
Targets who clicked the “Create Backup Now” button in the email were redirected through a malicious S3 bucket URL to a fake site (mail-lastpass[.]com). These domains are not affiliated with LastPass, and the real company has already begun working with third-party partners to take them down.
Associated phishing email servers were identified as operating behind private or spoofed IPs, such as 192.168.16[.]19 and 172.23.182.202.
The fake site closely replicates the appearance of legitimate LastPass communication, complete with instructions for exporting vault data and promises of “AES-256 encryption” and “Zero-Knowledge Architecture.” However, any interaction with the site likely results in the exfiltration of the user’s encrypted vault data, or worse, their master password, if entered.
Users are strongly urged to avoid clicking any unsolicited email prompts to back up vaults or perform emergency actions.
LastPass is a widely used password management service with millions of users worldwide, offering secure credential storage and multi-factor authentication. Due to the sensitive nature of the data it protects, the service is a frequent target of sophisticated phishing and social engineering campaigns. Recent incidents identified by the platform include a CryptoChameleon campaign targeting users’ digital assets, impersonation attacks using fake breach alerts, and a scam promoted via reviews on the LastPass Google Chrome Web Store page.







Leave a Reply