
A joint investigation by the German Federal Office for Information Security (BSI) and the Consumer Center of North Rhine-Westphalia (VZ NRW) has found that widely used password managers show critical security and privacy shortcomings.
Conducted in the first half of 2025, the study assessed 10 popular password managers on their technical security features and compliance with data protection regulations. The research was driven by the central role password managers play in safeguarding user credentials across a range of digital services, email, shopping, social media, and more.
Scope and methodology
The audit was carried out by BSI in collaboration with the FZI Research Center for Information Technology and covered the following tools: 1Password, Avira Password Manager, Chrome Password Manager, KeePass2Android, KeePassXC, Firefox Password Manager, mSecure, PassSecurium, SecureSafe, and S-Trust.
Each product was subjected to a threat model analysis, security feature assessment, and review of its privacy policies and registration processes. Vendors were given the opportunity to respond to preliminary findings.
Key findings on security
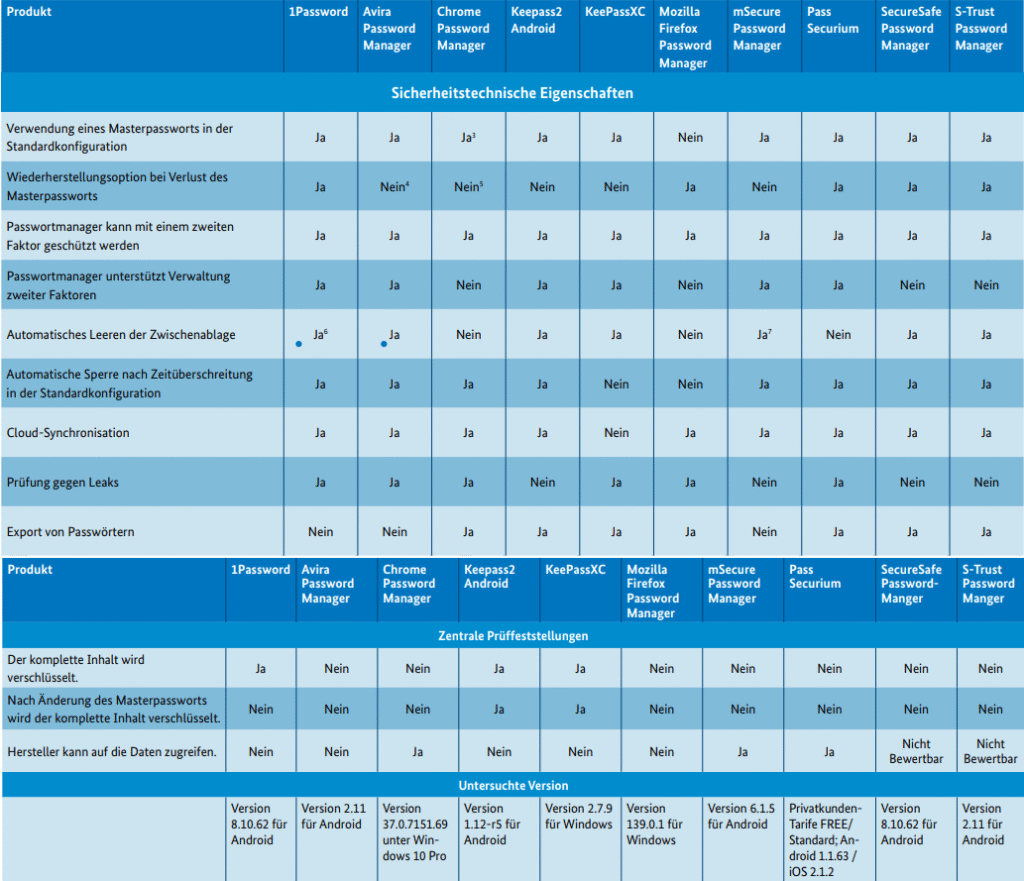
The investigation found that three of the ten tested password managers store passwords in a way that theoretically allows manufacturer access, increasing the potential attack surface. Specifically, Google Chrome Password Manager, mSecure, and PassSecurium failed to demonstrate that data was fully inaccessible to providers.
Only two products, KeePass2Android and KeePassXC, fully re-encrypt the vault after a master password change, a critical security measure to prevent access using outdated credentials.
Other technical observations included:
- Only six out of ten products stored all vault contents encrypted by default.
- Leak monitoring features were missing from several apps, notably mSecure, PassSecurium, and SecureSafe.
- Some managers (e.g., Firefox, Chrome) failed to use a master password by default, which could allow local access to credentials on shared devices.
Privacy and data handling concerns
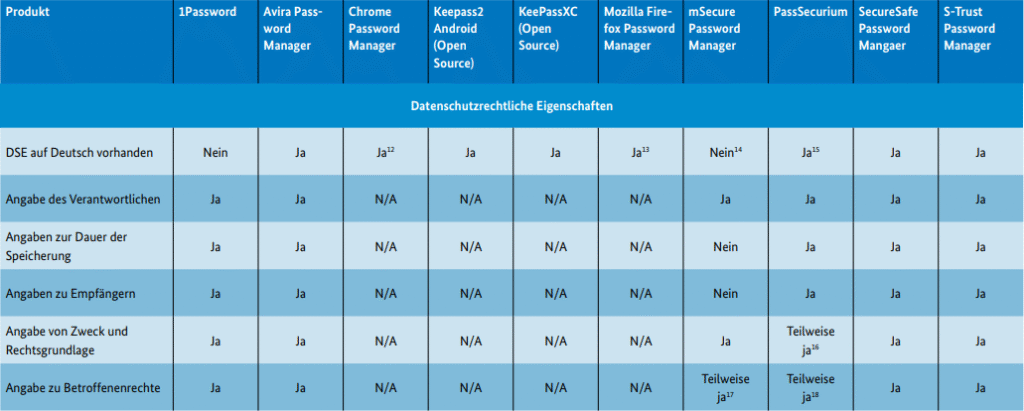
The VZ NRW assessed each vendor's data protection practices against GDPR criteria (Articles 12 and 13). Major concerns included:
- Opaque data-sharing practices: Services like 1Password, Avira, and SecureSafe reportedly share user data with third-party marketing and infrastructure providers, often without clear disclosure of recipient identities or data-handling safeguards.
- Use of dark patterns and opt-out designs during account registration, notably by 1Password and mSecure, potentially manipulates users into consenting to data collection and advertising practices.
- Some managers failed to provide local-language privacy notices, undermining accessibility for local users. Only about half of the products demonstrated a strong commitment to data minimization and transparency.
Open-source solutions KeePass2Android and KeePassXC were highlighted as the most privacy-conscious, storing user data locally and collecting no identifiable information.
Despite the shortcomings, the BSI strongly affirms that password managers remain far safer than manual or reused password practices. Reusing weak passwords remains a significant vector for phishing and account hijacking, outweighing the risks posed by implementation flaws in most password managers.







Nice, so easy explanation, that I even can’t read it in freaking German language on English news station? Is it really difficult to write tables in English, when publishing?
Kind of a letdown Bitwarden was not on their study. Interesting nonetheless
Ditto