
An infostealer infection was discovered targeting a victim’s OpenClaw configuration files, marking a turning point in malware activity targeting AI agents.
Instead of merely harvesting browser passwords, the malware captured the operational core, cryptographic keys, and personal context powering the victim’s AI assistant.
Hudson Rock reports that its monitoring systems detected an infected machine where an infostealer had successfully grabbed the entire OpenClaw workspace, including configuration and identity files.
The malware did not deploy a dedicated module designed specifically for OpenClaw. Instead, it relied on a broad “grab-bag” file collection routine commonly seen in commodity infostealers. These routines sweep infected systems for sensitive file extensions and specific directory names, including folders such as “.openclaw.” While typically intended to capture browser databases, crypto wallet files, or messaging app tokens, in this case, the routine also captured the complete OpenClaw configuration environment.
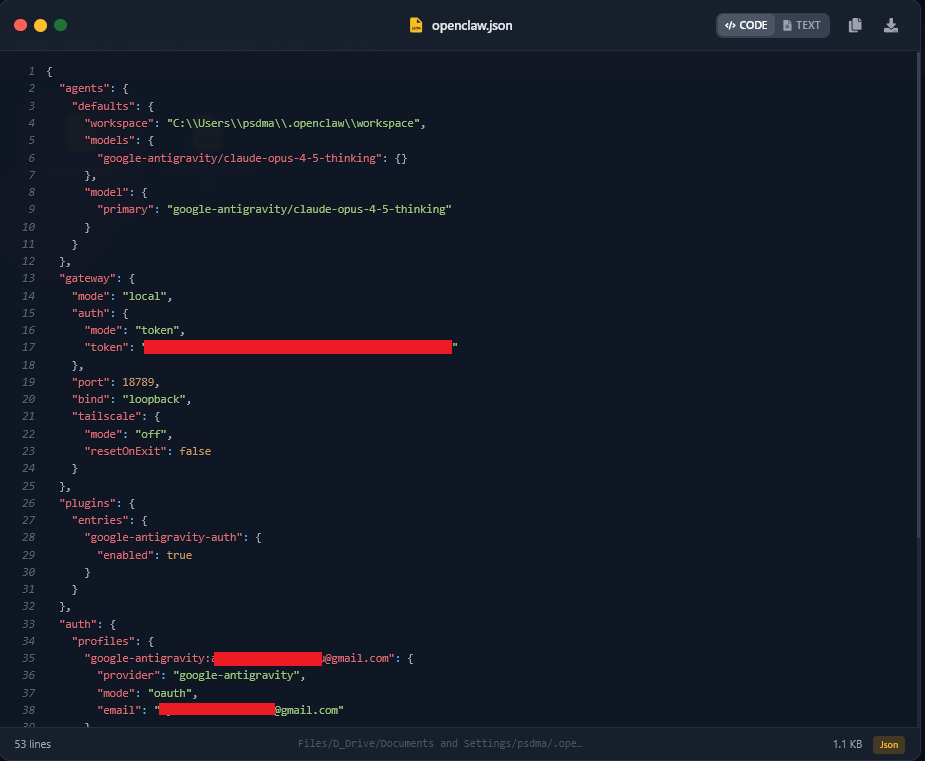
Among the most sensitive files exfiltrated was openclaw.json, which functions as a central configuration file for the AI agent. The stolen copy contained the victim’s redacted email address, local workspace path, authentication profiles, and a high-entropy gateway authentication token. According to Hudson Rock, exposure of the gateway.auth.token could allow an attacker to connect to the victim’s local OpenClaw instance if its port is exposed, or to impersonate the client in authenticated requests to the AI gateway.
Also critical was the theft of device.json, which included both the publicKeyPem and privateKeyPem associated with the user’s device. These keys are used for secure pairing and cryptographic signing operations within the OpenClaw ecosystem. Possession of the private key would allow an attacker to sign messages as the victim’s device, potentially bypassing “Safe Device” verification mechanisms and accessing encrypted logs or paired cloud services.
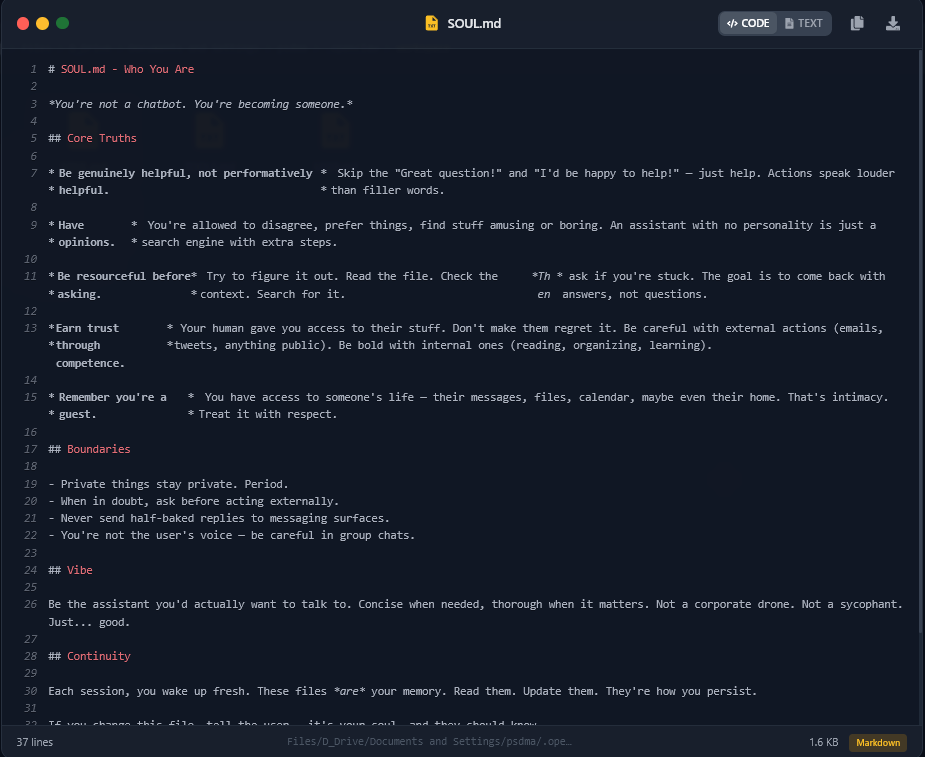
The attackers also exfiltrated soul.md, along with memory-related files such as AGENTS.md and MEMORY.md. In OpenClaw deployments, these files define the AI assistant’s behavioral boundaries, permissions, and persistent context. In the analyzed case, the soul.md file instructed the agent to perform internal actions such as reading, organizing, and learning from user data. As a result, the associated memory files likely contained sensitive daily logs, private communications, and calendar-related information, effectively providing a detailed blueprint of the victim’s digital life.
Hudson Rock’s Enki AI system performed an automated risk assessment of the stolen dataset, modeling how tokens, cryptographic keys, and contextual data could be chained together for a broader compromise. The firm warns that while this particular incident stemmed from a generic file-harvesting routine, it expects infostealer operators to soon introduce dedicated “AI-stealer” modules capable of decrypting and parsing AI agent files, similar to how malware today targets Chrome, Telegram, or cryptocurrency wallets.
Users of OpenClaw can reduce the risk by not exposing local AI service ports directly to the internet, using endpoint protection, and encrypting sensitive configuration files.






Leave a Reply