
The Gootloader malware now uses a deliberately malformed ZIP archive designed not only to bypass antivirus detection but also to thwart traditional analysis workflows used by defenders.
The unusual structure of the ZIP file makes it unreadable to many forensic tools, yet it remains fully functional on target systems, delivering a JScript payload that initiates a multi-stage infection chain.
Expel reports that this first stage of the infection, specifically the delivery format, has been quietly evolving in the background of Gootloader campaigns.
Gootloader, a malware family historically used for initial access in ransomware operations, reemerged in November 2025 following a brief hiatus. Huntress and other independent researchers have linked the current campaign to Vanilla Tempest, a threat actor known for deploying Rhysida ransomware. While earlier reporting covered the infection chain’s second stage, Expel’s research centers on the ZIP delivery method, which plays a crucial role in evading detection and impeding incident response.
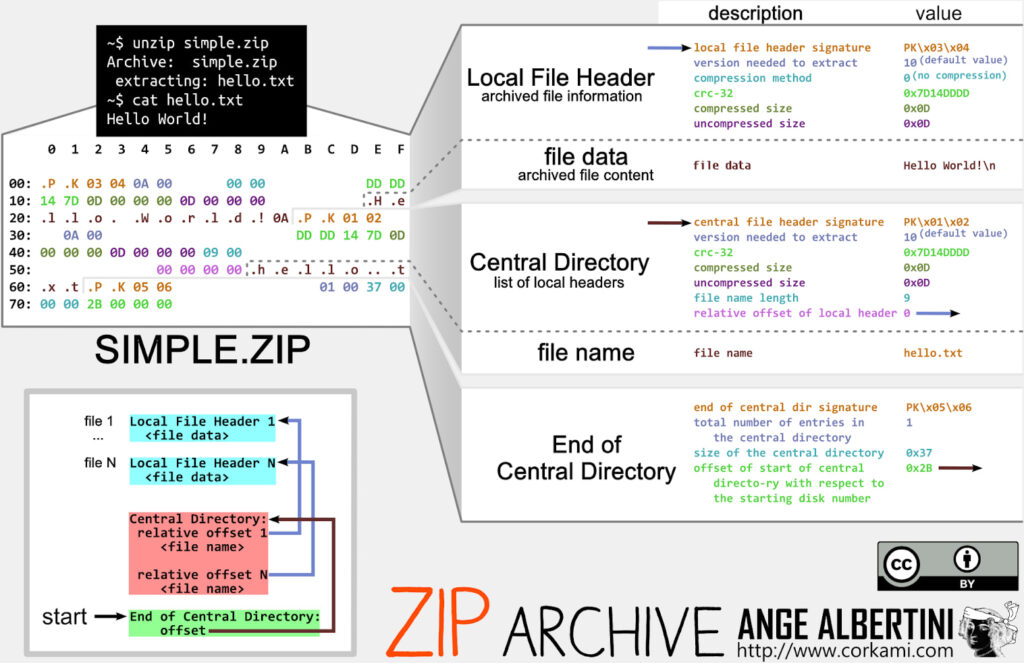
The ZIP archive used in current Gootloader campaigns is purposefully corrupted. Most forensic unarchivers, including tools like 7-Zip and WinRAR, fail to parse or extract its contents correctly. However, Microsoft’s built-in Windows ZIP handler opens it without issue, ensuring targets can still execute the embedded JScript file.
corkami.com
Expel’s reverse engineering reveals that the ZIP archive is not a single compressed file but a massive concatenation of hundreds of ZIP files, ranging from 500 to 1,000. This tactic works because the ZIP file format is read from the end, so the last ZIP structure remains valid despite all previous junk data. Additionally, each archive is generated on-the-fly per victim, using randomized metadata fields and hashbusting techniques to make static detection nearly impossible.
Gootloader’s ZIP archives are crafted to evade analysis through several key techniques. The “End of Central Directory” is deliberately truncated, breaking compatibility with many forensic tools. Non-critical fields like “Disk Number” are randomized to further disrupt parsing. Instead of a standard download, victims receive an XOR-encoded blob that is decoded and assembled into a ZIP file by the browser, bypassing network detection. Additionally, mismatches between the Local File Header and Central Directory, such as differing filenames and CRC32 values, cause tools to misinterpret the file as corrupt.
These features mark a substantial departure from earlier variants. Prior to this, Gootloader archives contained only simple mismatches, such as filename inconsistencies, tactics that were mildly disruptive but not formidable anti-analysis techniques.
When executed, the JScript inside the ZIP file launches PowerShell to establish persistence and initiate further payload delivery.
In its current form, the infection chain continues beyond ZIP execution:
- A malicious JScript drops a shortcut (.LNK) into the user’s Startup folder.
- This shortcut points to another .LNK in a randomly selected directory.
- The second .LNK launches a secondary, hidden JScript file.
- This file, in turn, launches PowerShell scripts to complete the infection.
These scripts frequently employ NTFS short names and obfuscated commands, making process tracking and behavioral detection more difficult.
Expel says that, despite Gootloader’s novel obfuscation tactic, its publicly available YARA rule can reliably detect it by looking at multiple instances of the same ZIP file header, repeated malformed EOCD structures, and specific byte patterns in the archive’s local headers.







Leave a Reply