
A newly disclosed browser extension campaign dubbed The Zoom Stealer has exposed the corporate meeting activity of over 2.2 million users.
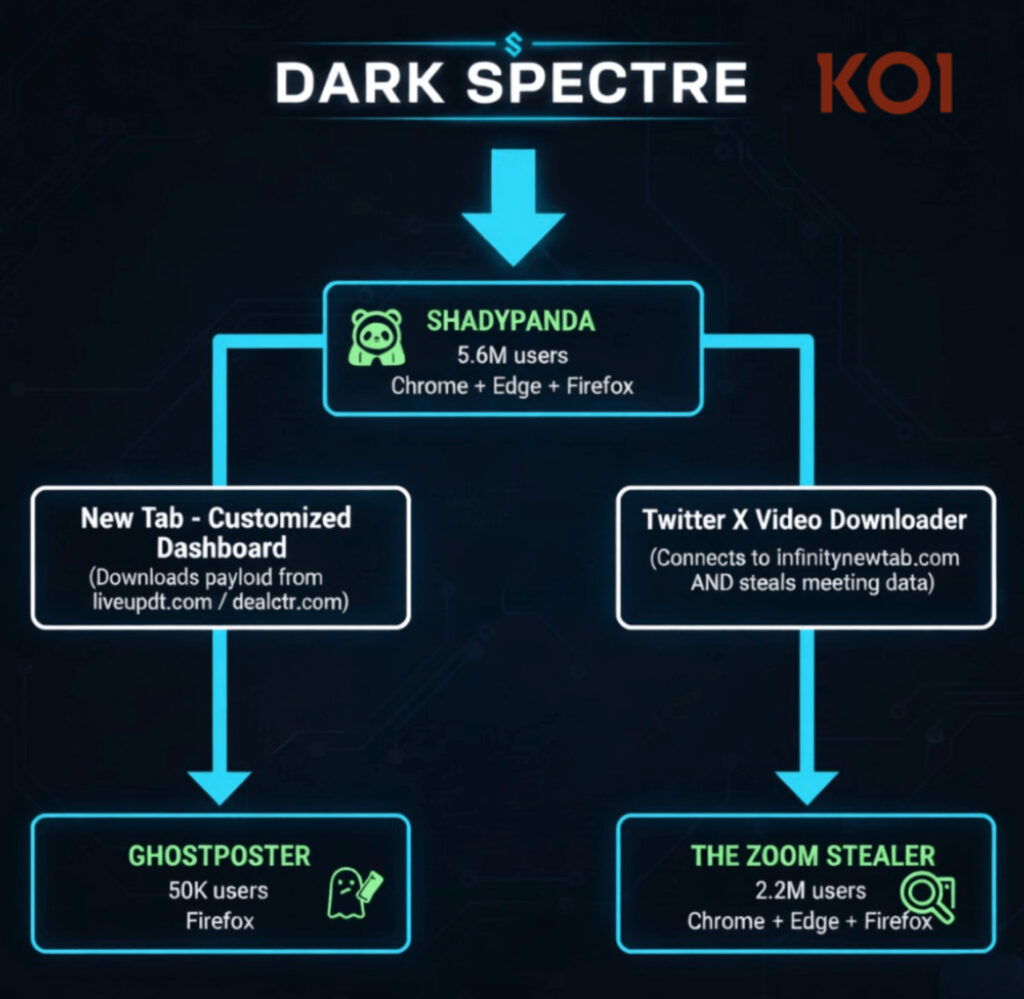
The campaign, active for years but only now unmasked, is part of a broader malware ecosystem operated by a sophisticated Chinese threat actor known as DarkSpectre, previously linked to the GhostPoster and ShadyPanda campaigns.
The Koi report connects Zoom Stealer, ShadyPanda, and GhostPoster to a single, well-resourced actor using overlapping infrastructure, code reuse, and highly coordinated operations across Chrome, Edge, and Firefox. Together, the campaigns span more than 7.8 million compromised browsers and demonstrate a patient, strategic approach far beyond typical criminal operations.
A hidden web of espionage
While mapping ShadyPanda infrastructure, Koi Security encountered an outlier, a Chrome extension titled Twitter X Video Downloader. Its behavior was unique, accessing over 28 video conferencing platforms and exfiltrating meeting data in real time. Following this lead uncovered 17 additional extensions, all participating in a previously unknown surveillance effort now called The Zoom Stealer.
Unlike prior campaigns that focused on user profiling or affiliate fraud, Zoom Stealer targets corporate meeting intelligence. The extensions present as productivity tools, meeting timers, auto-admit assistants, video downloaders, and function as advertised. However, behind the scenes, they quietly build dossiers on meetings and their participants.
Every extension in this campaign requests access to a wide array of conferencing platforms like Zoom, Microsoft Teams, Google Meet, Cisco Webex, and ON24, regardless of their stated purpose. Once installed, they scrape meeting URLs, registration forms, speaker bios, company affiliations, and even promotional graphics.
Chrome Audio Capture, one of the most prolific extensions, alone has over 800,000 installations, making it the largest single vector in the campaign.
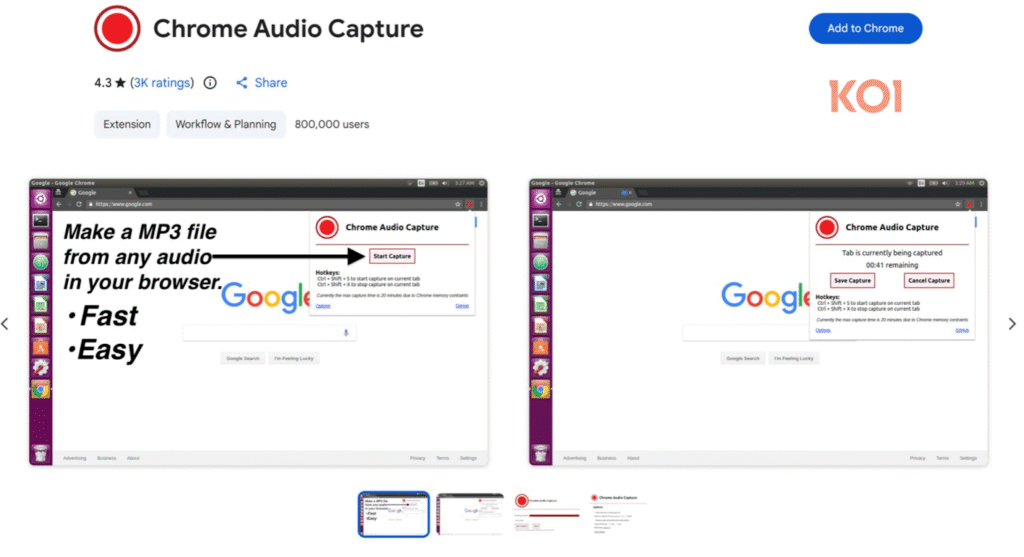
Collected data is exfiltrated using persistent WebSocket connections, allowing real-time streaming of activity. The data is stored in Firebase Realtime Database instances, with operations masked behind legitimate-looking domains like zoomcorder.com, an actual recording service used as a front for the campaign’s backend.
The infrastructure linked to DarkSpectre is largely hosted on Alibaba Cloud, with ICP registrations pointing to Hubei Province in China. Code artifacts contain Chinese language comments, and campaign operations align with Chinese time zones. Fraud schemes in ShadyPanda specifically target Chinese e-commerce platforms like JD.com and Taobao, reinforcing the attribution.







Leave a Reply