
Cisco has disclosed a campaign targeting its Secure Email Gateway and Secure Email and Web Manager appliances using an unpatched zero-day vulnerability.
A Chinese state-linked hacking group, tracked as UAT-9686, leverages a critical vulnerability to execute system-level commands and maintain persistent access on compromised systems.
The campaign was first detected on December 10, 2025, and is believed to have been underway since at least late November. Cisco Talos researchers uncovered the activity during an investigation stemming from a technical support case, ultimately linking the threat to a Chinese-nexus APT actor. The attackers are exploiting a configuration-dependent flaw in Cisco AsyncOS Software (CVE-2025-20393), affecting appliances where the “Spam Quarantine” feature is exposed to the internet, a setup not recommended in official deployment guides.
The affected products include both physical and virtual instances of Cisco Secure Email Gateway (formerly Cisco Email Security Appliance, or ESA) and Secure Email and Web Manager (previously Cisco Content Security Management Appliance, or SMA). These appliances are widely used by government, enterprise, and critical infrastructure sectors to enforce email filtering, manage spam quarantines, and centralize reporting and policy enforcement across deployments.
UAT-9686’s activity centers around a bespoke malware framework composed of multiple tools designed for persistence, log evasion, and covert communications. At the core of this toolkit is AquaShell, a Python-based backdoor embedded into an existing web server script (/data/web/euq_webui/htdocs/index.py). AquaShell decodes specially crafted HTTP POST requests to execute arbitrary commands with root privileges. Its passive nature and custom encoding logic allow it to remain under the radar of standard monitoring tools.
In addition to AquaShell, Talos observed three other components:
- AquaTunnel: A Go-based reverse SSH tool derived from open-source ReverseSSH, enabling attackers to tunnel into systems behind NAT or firewalls.
- Chisel: An open-source TCP/UDP tunneling tool used to pivot laterally across internal networks.
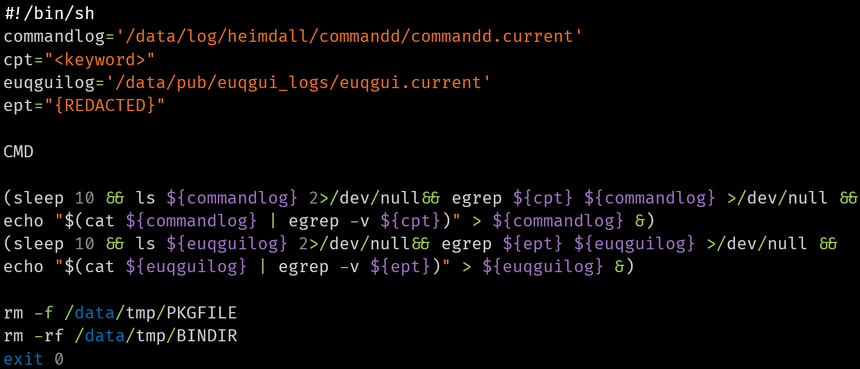
- AquaPurge: A log manipulation utility that scrubs activity traces by filtering out specific entries using the egrep command.
Cisco
According to Cisco, the compromise is based on a non-default setup in which the spam quarantine interface is accessible from the internet. Although the AsyncOS software is universally affected across versions, only systems with this exposure are vulnerable in practice. The exploitation allows the attacker to achieve full system compromise, including command execution with root privileges.
Cisco rates the flaw with a CVSS base score of 10.0, the highest possible severity. No patches are currently available, and there are no viable workarounds beyond immediate configuration changes and isolation of affected appliances.
Cisco recommends organizations take the following actions:
- Audit appliances for internet-exposed Spam Quarantine interfaces via the web management UI.
- Immediately remove or firewall external access to these interfaces.
- Monitor logs for known indicators of compromise (IOCs).
- Open a Cisco TAC case to assist in forensic analysis and determine if a compromise has occurred.
In confirmed cases, rebuilding the appliance is the only currently recommended remediation.
Cisco continues its investigation and has blocked IOCs across its ecosystem, while the company emphasizes that its cloud-based Secure Email service remains unaffected. However, the risk to on-premise and hybrid deployments remains high.







Leave a Reply