
Google has released a security update for Chrome to address a high-severity zero-day vulnerability that was actively exploited in a sophisticated espionage campaign targeting Russian organizations.
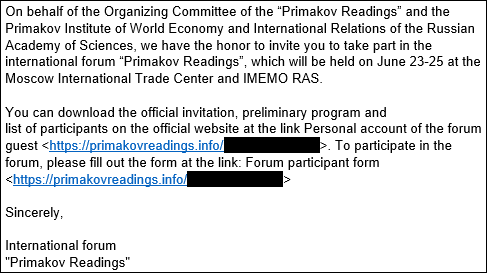
The flaw was discovered by Kaspersky researchers who linked the exploitation to a broader attack dubbed Operation ForumTroll. According to their analysis, the campaign began in mid-March 2025, when victims received phishing emails containing personalized links masquerading as invitations to a legitimate Russian expert forum, Primakov Readings. Clicking the link triggered a silent infection through Google Chrome, with no further user interaction required.
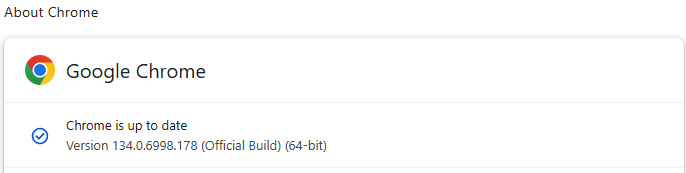
The vulnerability, tracked as CVE-2025-2783, stems from an “incorrect handle provided in unspecified circumstances in Mojo on Windows,” as described in Google's security bulletin. The issue allowed attackers to bypass Chrome's sandbox — a critical component of the browser's security model — due to a logical flaw in how Chrome interfaces with the Windows OS. Google confirmed the vulnerability was under active exploitation and released Chrome version 134.0.6998.177/.178 to address the issue on Windows platforms.
Kaspersky's telemetry first detected the zero-day during a spike in infections from a previously unknown malware strain. Upon investigation, the team reverse-engineered the exploit and submitted it to Google, prompting the fast-tracked patch. While Google's security advisory notes limited details until a majority of users are updated, Kaspersky confirmed the exploit chain leveraged CVE-2025-2783 to escape the sandbox, and likely depended on a secondary, unrecovered exploit to achieve full remote code execution.
The operation's phishing lures were well-crafted and narrowly targeted, aiming at media, academic, and governmental sectors within Russia. The attackers' infrastructure was short-lived, with malicious links rapidly deactivated after use. Currently, visiting the previously weaponized domain, primakovreadings[.]info, redirects to the real Primakov Readings website, suggesting a covert operation disguised in plain sight.
Kaspersky
Kaspersky believes the campaign is the work of a state-sponsored APT group based on the malware's sophistication, precision targeting, and the nature of the victims. Malware identified in the operation includes components labeled Trojan.Win64.Agent, Trojan.Win64.Convagent.gen, and several heuristic detections under Exploit.Win32.Generic.
To mitigate the risk posed by CVE-2025-2783 and similar threats, users should update Google Chrome immediately to version 134.0.6998.177 or .178 (on Windows). Users should also avoid clicking links in unsolicited emails, even if they appear relevant or personalized.
Kaspersky plans to release a detailed technical report on the exploit and malware used in Operation ForumTroll after more users have installed the Chrome patch.







Leave a Reply