
A new browser fingerprinting technique dubbed AdBleed reveals a previously overlooked privacy leak vector, country-specific adblock filter lists, that can partially de-anonymize users even when traffic is routed through a VPN or Tor.
The proof-of-concept, developed by independent researcher Melvin Lammerts and publicly demonstrated at adbleed.eu, shows that the combination of localized adblocking rules and client-side timing analysis can expose a user’s likely country of residence or language preferences. This discovery adds a new dimension to the browser fingerprinting landscape, which already includes vectors like screen resolution, fonts, and timezone.
melvin.ovh
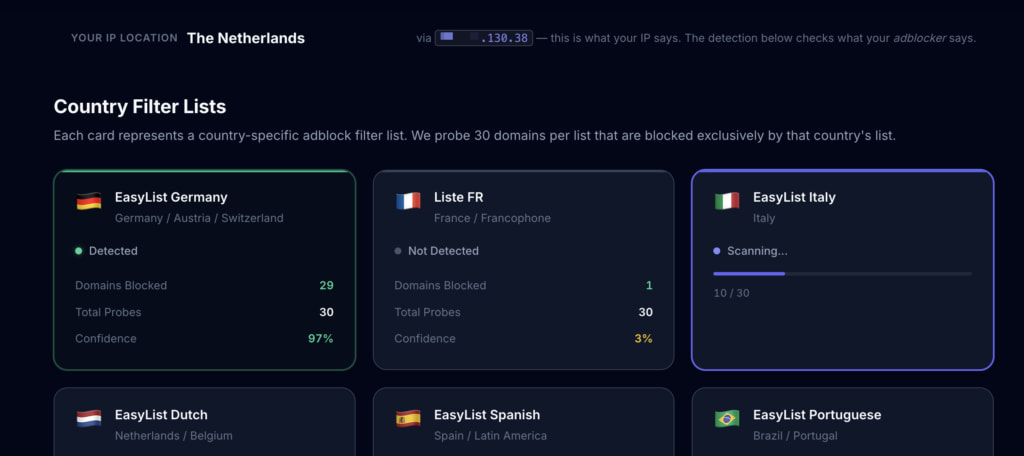
Exposed via adblock filter lists
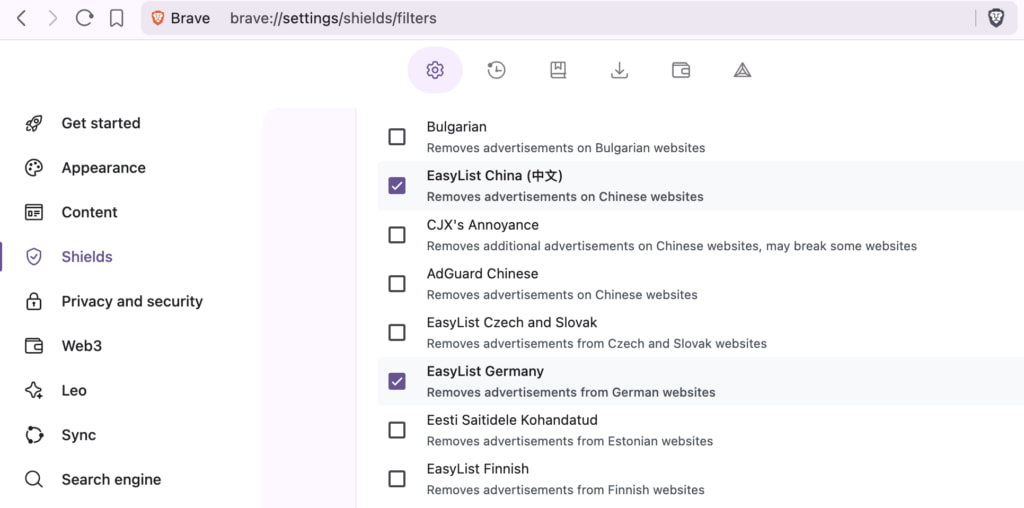
The technique works by probing the presence of regional adblock filter lists through JavaScript executed in the browser. Adblockers like uBlock Origin, AdBlock Plus, AdGuard, and Brave’s Shields rely on community-maintained rule sets, such as EasyList, which target ad and tracker domains. Many users, either through default settings or installer prompts, also enable country-specific filter lists like EasyList Germany, Liste FR, or EasyList Italy, tailored to block localized ad networks.
melvin.ovh
By checking which of these localized domains are blocked in the browser, the AdBleed technique infers which regional list is active. Because VPNs only mask IP addresses, and not browser-side configurations like adblock filters, this detection method remains effective regardless of how traffic is routed.
The detection relies on a timing-based heuristic. JavaScript in the browser attempts to load a small resource, typically a favicon, from domains included in country-specific filter lists. If the resource is blocked, the browser fires an onerror event almost instantly, typically within 5 milliseconds, because the request is intercepted before reaching the network stack. If the domain is not blocked, the request attempts a DNS lookup or TCP connection, resulting in a noticeably longer delay. By analyzing this timing across 30 domains per region, and using a conservative threshold (e.g., 20/30 blocked), the technique can confidently determine which country's filter list is in use.
Lammerts carefully curated the domain sets to avoid overlap with general lists like EasyList by programmatically subtracting those entries. Positive and negative control domains were used to validate the presence of an adblocker and eliminate edge-case errors from the scan. The proof-of-concept currently tests lists for Germany, France, Italy, the Netherlands, Spain, Brazil, and Russia, providing a live confidence score and full scan breakdown.
The research was initially conducted using Brave Browser with default Shields enabled, then extended to other adblockers like uBlock Origin and AdBlock Plus, which may ship different base rule sets and affect the accuracy of the detection.
Unlike traditional fingerprinting, AdBleed operates entirely in the browser, requires no server-side cooperation, and doesn't rely on cookies or storage APIs. It bypasses common anonymity tools such as VPNs, proxies, and even Tor Browser, by exploiting the adblock configuration as a behavioral signal.
Affected are virtually all users employing regional adblock filters, which are commonly enabled either automatically based on browser locale or through user prompts. The targeted services include regional ad networks specific to each country, which are otherwise absent from global filter lists.
For users focused on anonymity, mitigation is challenging. Avoiding regional filter lists entirely increases exposure to localized ads and trackers. One potential workaround is to enable several unrelated country lists to dilute the signal. However, this may result in overblocking or reduced site functionality. More extreme options include not using an adblocker, ironically reducing privacy in other ways. Adblocker developers could address this by adopting context-aware filtering, where country-specific rules are only triggered for matching local content or domains.







O.O . VPNs are only good for torrenting . I never did depend on them for anamity beyond P2P . Even if you were to somehow catch a server with logs , the information they can gather is limited . It would say X shared encrypted packets with Y . The fingerprint is totally different .