
Trust Wallet has acknowledged a critical security incident affecting version 2.68 of its browser extension, following mounting community reports that began surfacing on Christmas Day.
The breach appears to stem from a supply chain attack that compromised a recent update, exposing users to immediate wallet draining upon importing their seed phrases.
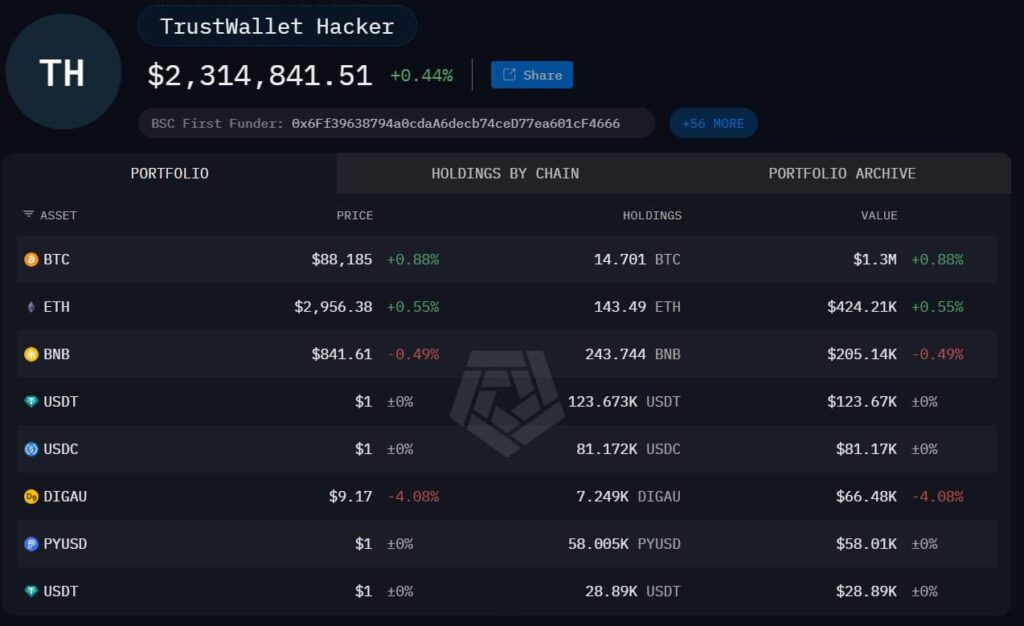
The first public signs of trouble came from blockchain researcher @0xakinator, who issued a warning on X late on December 25. In the alert, Akinator alleged that version 2.68 of the Trust Wallet extension, pushed on December 24, had been compromised with malicious code that transmitted wallet data to an external domain. Within hours, multiple users began reporting significant losses, with estimates exceeding $2 million across various addresses controlled by the attackers.
@0xakinator
The breach was reportedly tied to a file named 4482.js, which was added or modified in the tainted update. According to Akinator’s analysis, this script masqueraded as an analytics module while silently harvesting sensitive wallet data. The stolen data was then transmitted to a domain, metrics-trustwallet[.]com, registered just days before the breach. The domain has since been taken offline, but not before allegedly siphoning off substantial funds.
Trust Wallet admits breach
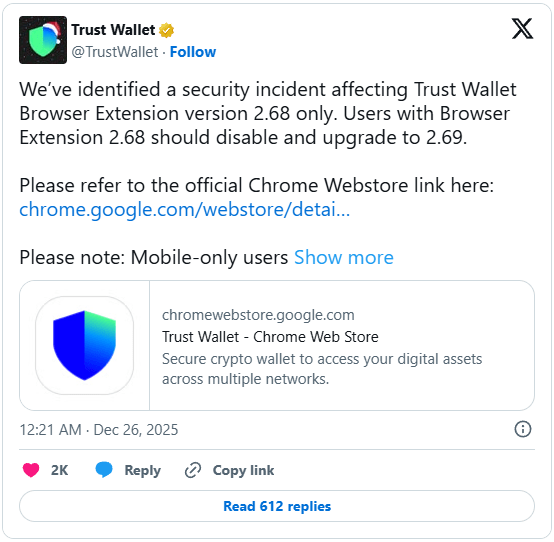
Trust Wallet formally confirmed the breach in the early hours of December 26. The company stated that only users of version 2.68 of the browser extension are affected and urged immediate upgrades to version 2.69. Mobile users and those running any other extension version were confirmed to be unaffected.
Trust Wallet is a widely used non-custodial crypto wallet that allows users to store, manage, and swap assets across multiple blockchains. Originally developed by a third party, it was acquired by Binance in 2018 and now operates as a standalone project. The browser extension is a relatively recent addition that offers desktop users an alternative to the mobile app experience.
In a follow-up thread, Trust Wallet provided a step-by-step guide to safely disable the compromised version and upgrade to the patched release. The company emphasized that users should not open the extension until they’ve updated to version 2.69, to avoid triggering any malicious activity. The update is currently live on the Chrome Web Store.
The incident has sparked concern in the broader crypto community, with users questioning the vetting process behind browser extension updates and the potential for more widespread supply chain vulnerabilities in wallet software. Prominent crypto investigator ZachXBT reported receiving messages from impacted victims and requested clarity from Trust Wallet regarding potential compensation. The company responded that its customer support team is actively in touch with affected users via its official help portal.
While Trust Wallet has not confirmed the full scope or origin of the attack, the targeted nature of the compromise and the use of a newly registered exfiltration domain strongly point to a well-executed supply chain attack. The actor behind the breach also left a taunting message referencing Frank Herbert’s Dune: “He who controls the spice controls the universe.”
Trust Wallet users are advised not to activate the extension until they have updated to version 2.69. Those who have imported seed phrases into version 2.68 should assume compromise and immediately migrate funds to a new wallet generated on a secure device.







Leave a Reply