
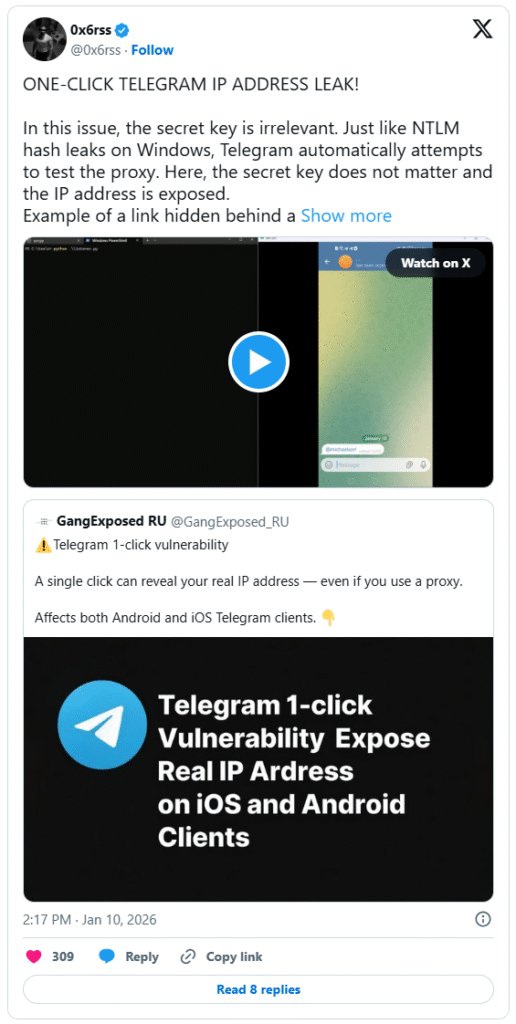
Telegram client behavior with proxy links may allow attackers to reveal a user’s real IP address with a single click, even when a proxy is configured.
According to a series of posts by the researcher collective GangExposed RU, the issue affects both Android and iOS clients and appears to stem from how Telegram internally processes proxy server links disguised as normal usernames.
The claims, posted over the weekend, describe how a Telegram user can be tricked into clicking on what appears to be a regular internal profile mention (e.g., @durov) that actually conceals a t.me/proxy link. Once clicked, Telegram automatically attempts to validate the proxy by pinging it directly. Crucially, this action bypasses any currently configured proxy settings, resulting in the client sending a direct request that can expose the user’s actual IP address to the proxy server operator, before the user has a chance to reject or configure the proxy.
This behavior, while not involving remote code execution or persistent compromise, introduces a targeted attack surface that undermines user trust assumptions. Unlike traditional IP-leak scenarios involving external links or content, this attack uses a Telegram-native mechanism to create what appears to be an internal UI element, thereby reducing user suspicion. According to GangExposed RU, “the secret key is irrelevant” for this leak; it is the act of clicking that triggers the exposure.
Telegram, as of the time of writing, has not officially responded to inquiries or clarified whether this behavior is intended or will be addressed.
Telegram is a widely used encrypted messaging platform with over 700 million active users globally. While its secret chats are end-to-end encrypted, standard chats and other functionalities, including proxy connections, rely on Telegram’s own infrastructure and client-side logic. Users can route their traffic through SOCKS5 proxies to circumvent censorship or enhance anonymity, especially in regions with restricted internet access.
Proxy servers on Telegram are configured manually or via shared links. When a proxy link is clicked, Telegram attempts to validate the server before offering to apply it. The issue arises from this validation step, which appears to occur outside any existing proxy or VPN tunnels, potentially exposing the user’s IP address to an attacker-controlled server without any user prompt.
Some users argue that this is not a vulnerability in the conventional sense, as it requires a user action (a click), and that direct proxy validation is expected behavior. However, this design violates privacy expectations. A key concern is that Telegram does not warn users or differentiate these links from standard usernames or internal Telegram actions, making the attack stealthy and effective in social engineering scenarios.
In practical terms, attackers could craft proxy links and embed them behind innocuous mentions, or distribute them through bots and channels, relying on curiosity or habit to get targets to click.
Until Telegram pushes a fix for this, users should avoid clicking on suspicious @username mentions, especially in untrusted groups or channels, and consider using VPNs to hide their real IP address during network requests.
[Article Update] – A Telegram spokesperson sent CyberInsider the following statement, indicating that the behavior will not change, but a warning will be added to increase safety for users.
Any website or proxy owner can see the IP address of those who access it regardless of platform. This is not any more relevant to Telegram than WhatsApp or any other service that accesses the internet.
That said, we're adding a warning that will show when clicking proxy links so users can be more aware of disguised links. – Telegram






Leave a Reply