
Six VPN apps have been found to be infecting users’ systems with malware, contributing to one of the largest botnets ever dismantled.
A U.S. Department of Justice announcement earlier this week highlighted the takedown of the 911 S5 botnet, responsible for infecting over 19 million IP addresses worldwide, including 613,841 in the United States.
The botnet’s administrator, YunHe Wang, a Chinese national, was arrested on May 24, 2024. Wang and his associates had created and distributed illegitimate VPN applications since 2014, which connected to the 911 S5 service, transforming users’ devices into part of the botnet. This extensive network facilitated various criminal activities, including financial fraud, identity theft, and child exploitation.
The botnet generated nearly $99 million in illicit profits, allowing cybercriminals to access infected IP addresses for a fee. This facilitated large-scale fraud, including over 560,000 fraudulent unemployment claims and more than 47,000 Economic Injury Disaster Loan applications during the COVID-19 pandemic.
Malicious VPN applications
The VPN apps the fraudsters created specifically for the purpose of supporting their botnet malware operations were distributed as free downloads or bundled with other software and installed malware on users’ devices without their consent.
The VPN applications the authorities identified as part of this scheme include:
- MaskVPN
- DewVPN
- PaladinVPN
- ProxyGate
- ShieldVPN
- ShineVPN
These applications, once installed, made the users’ systems part of the botnet, allowing cybercriminals to use their IP addresses for illegal activities while concealing their true locations.
Detecting and removing the malware
The dismantling of the 911 S5 botnet and the arrest of its administrator significantly disrupted the botnet’s operations. However, while the botnet infrastructure has been compromised, it does not automatically deactivate all infected devices. The malicious software on affected systems could still pose risks if not removed, as the bots could be ordered to switch communications to new infrastructure set up by Wang’s co-conspirators.
If you installed any of the listed VPN applications at any point in the past, follow these steps to remove them:
Uninstall them:
- Click on the Start menu (Windows button) and type “Add or remove programs.”
- Search for the name of the malicious VPN application.
- If found, click on the application name and select “Uninstall.”
End malicious processes:
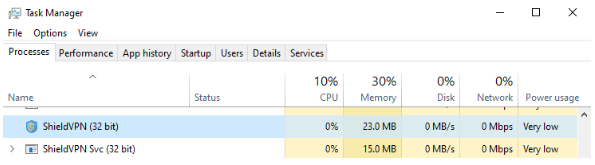
Open the Windows Task Manager by pressing Control+Alt+Delete and selecting “Task Manager,” or right-click on the Start menu and select “Task Manager.”
Under the “Process” tab, look for the following processes:
- MaskVPN (mask_svc.exe)
- DewVPN (dew_svc.exe)
- PaladinVPN (pldsvc.exe)
- ProxyGate (proxygate.exe, cloud.exe)
- ShieldVPN (shieldsvc.exe)
- ShineVPN (shsvc.exe)
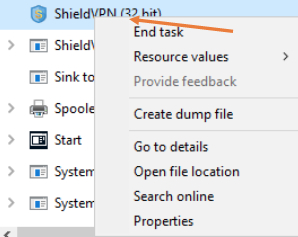
If found, select the process and choose “End task.”
Run a malware scan:
There are several free AV tools that should be able to detect the mentioned threat including Bitdefender, Avast, and AVG, so running a complete system scan with one of them is recommended.
Malwarebytes has confirmed via an update yesterday that it has added detection signatures for the mentioned VPN binaries, so people can use Malwarebytes Premium (a free trial is available) to scan for remnants.
Open the application and click the Scan button on the main dashboard. Wait for the scan to complete and review the Threat scan summary. If threats are detected, manually quarantine them by selecting the detections and clicking Quarantine.
The FBI has also published detailed removal instructions on this webpage.
In conclusion, users should exercise caution when installing VPN applications, ensuring they come from reputable sources. Trustworthiness should always take precedence over cost. Due to their popularity, VPN apps are the go-to choice for cybercriminals looking to establish an effective malware distribution mechanism. (1, 2, 3, 4)







Sven Sir what are your views on Antivirus? Are antivirus software necessary or worth it? Or they are not useful and are a thing of the past?
I think the best antivirus is common sense, but there are some options like Emsisoft that seem good, and not invasive.
Deep question!
Although RestorePrivacy does not devote much attention to antivirus software, one solution that offers the highest levels of security while also respecting user privacy is Emsisoft. Another potentially good option, which is entirely FOSS, is Clam AV.
[https://cyberinsider.com/privacy-tools/]
According to an FBI survey, major businesses lose $12 million annually dealing with virus incidents. A survey by Symantec in 2009 found that a third of small to medium-sized business did not use antivirus protection at that time, whereas more than 80% of home users had some kind of antivirus installed. According to a sociological survey conducted by G Data Software in 2010 49% of women did not use any antivirus program at all.
USAGE AND RISKS
[https://en.m.wikipedia.org/wiki/Antivirus_software]
Do you carry an umbrella when there is a chance of rain?
Think of a good antivirus as the queen in a bee hive, and virus with malware are the beekeeping pest.
So from one attack the whole hive is notified or on guard protecting in zero-day.
(A zero-day exploit is basically a vulnerability which security researchers / software developers don’t know about (and therefore don’t have a patch prepared for) until after the vulnerability has already been exploited in the wild (e.g. used to steal people’s credentials).
Malwarebytes is really good for such things. I have it for years. Light weight, no drama, silently does the job in the background and does it well. I recommend.
Malwarebytes and SUPERAntiSpyware had back in the day, offered lifetime license that I bought.
Though I haven’t used either program the last 6 years or more in time, and in being solely dependant on their protection.
I have added them on a system when trying out a main defence, in my case, when using the kaspersky suite and then later with Emsisoft Anti-Malware.
I’m still using Emsisoft by subscription!
Had you seen this?
[https://arstechnica.com/information-technology/2021/01/security-firm-malwarebytes-was-infected-by-same-hackers-who-hit-solarwinds/]
What about this?
SUPERAntiSpyware is now certified by AppEsteem!
The SUPERAntiSpyware application, website and installer passed nearly 200 tests, developed to ensure customers are protected from cybercrime and unwanted software.
[https://www.superantispyware.com]
[https://appesteem.com/]
Something else that was useful once and maybe still?
EULAlyzer helps you instantly analyze license agreements (EULAs), to determine the risks that software might pose. Advertising? Data collection? Hidden installation of third-party software? EULAlyzer breaks down long license agreements into easy-to-parse points of interest, instantly, to help you quickly zero in on potentially riskier behavior.
Last updated in 2012
[https://www.wilderssecurity.com/threads/eulalyzer-2-2-released.324853/]
Be interesting to see EULAlyzer revived with AI for the consumer.
Why is the US gov so behind (10 years) in cyber-security?
[https://en.m.wikipedia.org/wiki/Internet]
The origins of the Internet date back to research to enable time-sharing of computer resources and the development of packet switching in the 1960s. The set of rules (communication protocols) to enable internetworking on the Internet arose from research and development commissioned in the 1970s by the Defense Advanced Research Projects Agency (DARPA) of the United States Department of Defense in collaboration with universities and researchers across the United States and in the United Kingdom and France.
613,841 Internet-connected devices, each of which runs one or more bots in the US alone. Such as computers, smartphones or Internet of things (IoT) devices whose security have been breached and its control ceded to a third party.
“over 560,000 fraudulent unemployment claims”
“47,000 Economic Injury Disaster Loan applications”
All from the 911 S5 botnet, so what was the 911 S5 botnet (“robot” and “network”) responsible in, of the remaining 6,841 IP devices allowing the attacker to access these devices and its connection.
Botnets are increasingly rented out by cyber criminals as commodities for a variety of purposes, including as booter/stresser services.
The botnet controller community constantly competes over who has the most bots, the highest overall bandwidth, and the most “high-quality” infected machines, like university, corporate, and even government machines.
While botnets are often named after the malware that created them, multiple botnets typically use the same malware but are operated by different entities.
[https://en.m.wikipedia.org/wiki/Botnet]
dude behind ??? They have quantum computers since 90’s and Eddie in 2013 it was their game to buring truth what technology they have . This technology what we have now they consider as ancient .
I hear your talk without the walk of facts being supplied. Go back and understand what I supplied for the question of. . .
Why is the US gov behind in cyber security?
When (DARPA) was commissioned in the 1970s by the United States Department of Defense.
Who is DARPA’s main client if not the US government itself? That the US Dept. of Defense existence is to serve the United States governmant, the homeland and its population.
DARPA deployment should of protected us from the botnet controller community. Who constantly competes over who has the most bots, the highest overall bandwidth, and the most “high-quality” infected machines, like university, corporate, and even government machines.
This article mentions, 613,841 Internet-connected devices, each of which runs one or more bots in the US alone.
Not going into the 3-letter gov agencies or any kind of black-opps of them or our military. But the United States Department of Defense via DARPA.
The Cheyenne supercomputer array had a rigorous workflow over seven years of operation to earn its wear and tear. The array’s services were used by scientists across the state of Wyoming and the rest of the country when needed. The 5.34-petaflop system was mainly used for weather and climate studies, helping the National Science Foundation better study climate change and other Earth-related sciences.
[https://www.tomshardware.com/tech-industry/supercomputers/multi-million-dollar-cheyenne-supercomputer-auction-ends-with-480085-bid]