
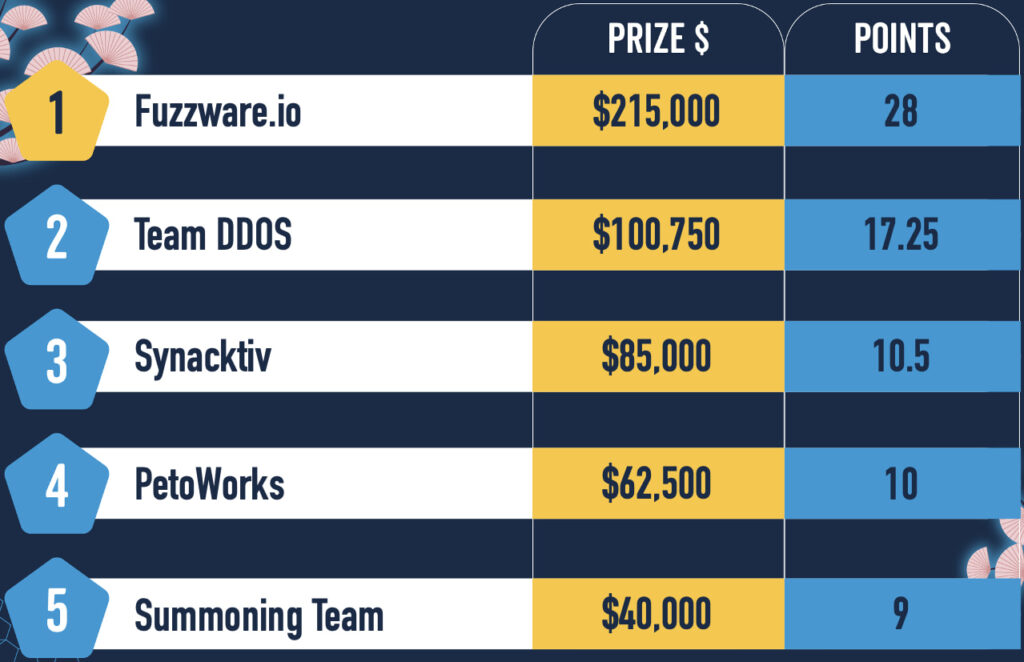
The third and final day of Pwn2Own Automotive 2026 concluded with a flurry of successful exploits and bug collisions, pushing the event’s total payout to $1,047,000 USD across 76 unique zero-day vulnerabilities.
Fuzzware.io’s trio, Tobias Scharnowski (@ScepticCtf), Felix Buchmann (@diff_fusion), and Kristian Covic (@SeTcbPrivilege), secured the top honor of “Master of Pwn,” finishing with 28 points and $215,500 in total rewards.
ZDI
Day three of Pwn2Own Automotive saw Fuzzware.io targeting the Alpine iLX-F511 again, but their submission encountered a bug collision with a previously demonstrated exploit. The team still earned $2,500 and one point toward their winning total.
The day was marked by a strong showing from both returning and new participants. Vietnamese researchers from Viettel Cyber Security (@vcslab) exploited a heap-based buffer overflow in the Sony XAV-9500ES, achieving arbitrary code execution and taking home $10,000 and two points. Another member of the same team, Nguyen Thanh Dat (@rewhiles), also targeted the Kenwood DNR1007XR but ran into a collision, earning $2,500 and a point.
PetoWorks (@petoworks) successfully exploited a buffer overflow in the Grizzl-E Smart 40A, earning $10,000 and four points, while Team DDOS, Bongeun Koo (@kiddo_pwn) and Evangelos Daravigkas (@freddo_1337), earned $5,000 by demonstrating a stack-based buffer overflow in the Alpine iLX-F511. The Grizzl-E unit, a Level 2 EV charger aimed at home users, saw multiple attempts throughout the event, reflecting its increasing relevance in the consumer automotive tech landscape.
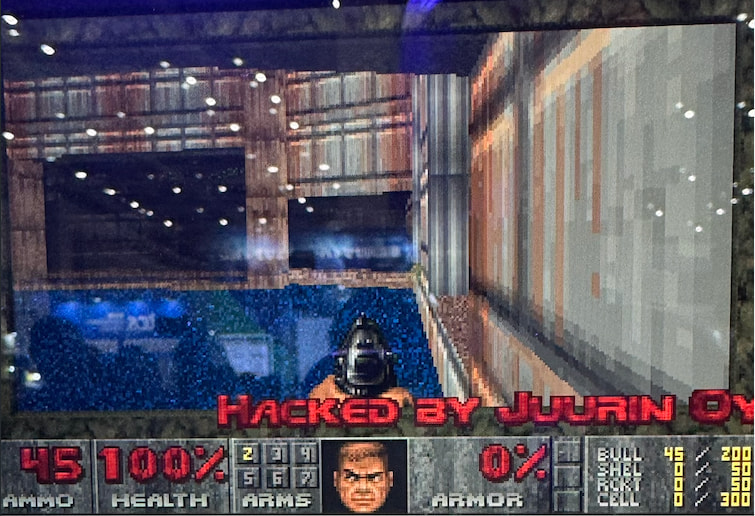
Finnish firm Juurin Oy brought flair and nostalgia to the floor with two standout entries. First, researchers Aapo Oksman, Elias Ikkelä-Koski, and Mikael Kantola exploited a time-of-check to time-of-use (TOCTOU) flaw in the Alpitronic HYC50 fast charger, installing a playable version of Doom in a flashy demo that netted them $20,000 and four points. In a second exploit, Ikkelä-Koski and Oksman successfully abused a link-following vulnerability in the Kenwood DNR1007XR, earning $5,000 and two points.
ZDI
Autocrypt’s team, consisting of five researchers, achieved root access on the Alpine iLX-F511 by chaining two vulnerabilities. One of the bugs overlapped with prior research, reducing the payout to $3,000 and 1.25 points. Qrious Secure (@qriousec), operating under the pseudonym “Slow Horses,” also faced collisions in both of their final-day entries, one against the Grizzl-E Smart 40A and another against the Kenwood head unit, still earning a combined $9,000 and 3.75 points.
The FPT NightWolf Team from Vietnam added to the scoreboard by uncovering a previously unknown bug in the Alpine iLX-F511 that granted root access, adding $5,000 and two more points to their record. Meanwhile, Team MST and Ryo Kato (@Pwn4S0n1c) demonstrated technically sound submissions that hit bug collisions but still resulted in partial payouts. Kato, in particular, chained three vulnerabilities in the Autel MaxiCharger AC Elite Home 40A, walking away with $16,750 and 3.5 points.
Kenwood’s DNR1007XR, a high-end digital receiver widely used in aftermarket automotive installations, was one of the most targeted devices of the event, revealing multiple issues across participants, from permission misconfigurations and race conditions to link traversal bugs.







Leave a Reply