
A new phishing kit, Spiderman, enables cybercriminals to impersonate dozens of major European banks and crypto platforms with minimal effort, enabling real-time theft of credentials and multi-factor authentication tokens.
The kit's professional design and advanced filtering mechanisms suggest a rising level of maturity in phishing infrastructure aimed at the financial sector.
According to cybersecurity firm Varonis, Spiderman consolidates dozens of high-fidelity phishing page templates into a single, easy-to-use control panel that caters to attackers operating across borders. The platform supports real-time session monitoring and data harvesting, representing a growing threat to both traditional banks and cryptocurrency users across Europe.
The kit appears to have been circulating on underground forums and in private Signal groups, with one such group linked to its distribution boasting over 750 members. This level of adoption indicates Spiderman is not just a prototype or isolated tool but an active, well-supported framework already being used at scale.
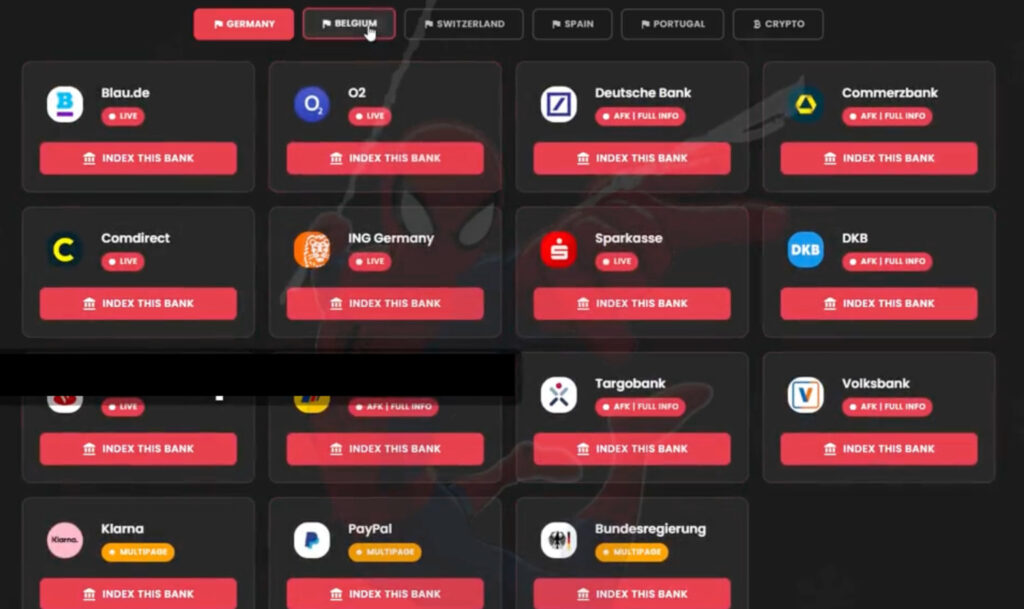
Spiderman's target list spans major financial institutions such as Deutsche Bank, Commerzbank, ING (Germany and Belgium), and CaixaBank, as well as several crypto wallet services, including Ledger, Metamask, and Exodus. This broad targeting reflects a trend toward hybridized financial fraud operations, where traditional banking credentials and crypto wallet seed phrases are harvested in tandem.
Varonis
At its core, Spiderman functions as a full-stack phishing framework. Once an operator selects a target institution from the control panel, the kit generates a pixel-perfect clone of that bank's login portal. Victims who interact with the phishing page are guided through multi-step prompts, including requests for usernames, passwords, two-factor authentication (OTP/PhotoTAN codes), credit card details, and personal information.
From a technical standpoint, Spiderman stands out due to its real-time session management and robust access-control system. The operator dashboard logs each victim's inputs live, allowing the attacker to dynamically prompt for additional data and keep the session active through a unique identifier. This interactive workflow increases the likelihood of bypassing multi-factor authentication and completing fraudulent transactions in real time.
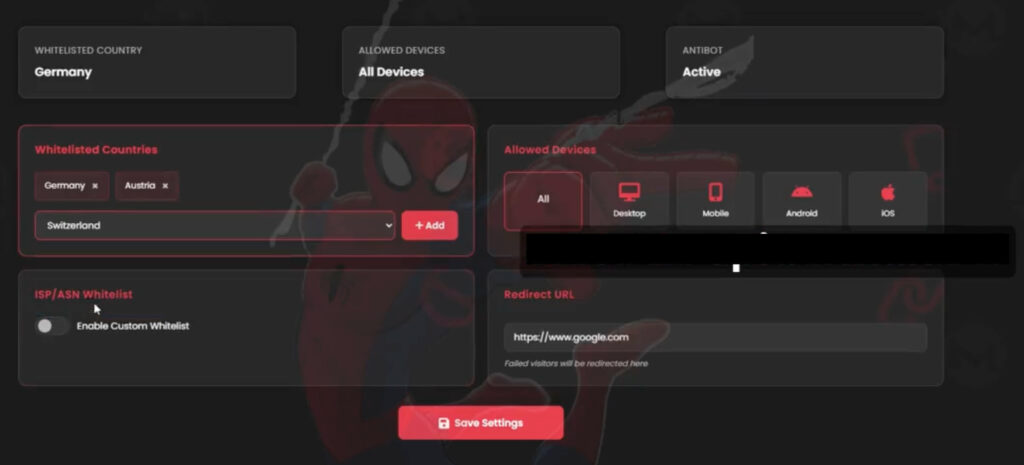
The kit's anti-detection features are equally advanced. Its access-control module includes:
- Country whitelisting, restricting access to specific regions (e.g., Germany, Belgium).
- ISP and ASN filtering, which blocks known VPNs, security scanners, and cloud infrastructure IPs.
- Device-type filtering, ensuring only users on targeted devices (mobile, desktop, Android, iOS) can access the phishing page.
- Custom redirects, which send non-target users to benign sites like Google, reducing the likelihood of exposure.
These features are designed to evade both automated security scanners and manual analysis by researchers, making the phishing pages much harder to detect or disrupt.
Varonis
The inclusion of real-time OTP capture, particularly PhotoTAN support, constitutes a significant escalation in the kit's capabilities. Many European banks rely on PhotoTAN apps or SMS-based TANs for transaction authorization. By intercepting these codes as users enter them, Spiderman enables attackers to bypass two-factor authentication mechanisms that have traditionally protected financial accounts.
Victims lured into the phishing workflow can have an entire identity packet harvested, including login credentials, full name, address, date of birth, credit card information, and device metadata. This data facilitates not only account takeovers but also downstream fraud techniques such as SIM swapping, credit fraud, and identity theft.







Leave a Reply