
A new cross-platform spyware suite, dubbed ZeroDayRAT, is openly sold on Telegram, offering buyers full remote access to both Android and iOS devices and enabling everything from real-time surveillance to financial theft within minutes of infection.
Discovered less than 48 hours before the publication of the analysis report, ZeroDayRAT is marketed as a turnkey mobile spyware platform. Its developers manage public Telegram channels to coordinate sales, offer technical support, and distribute updates, effectively creating a streamlined ecosystem for threat actors with little to no technical expertise.
ZeroDayRAT details
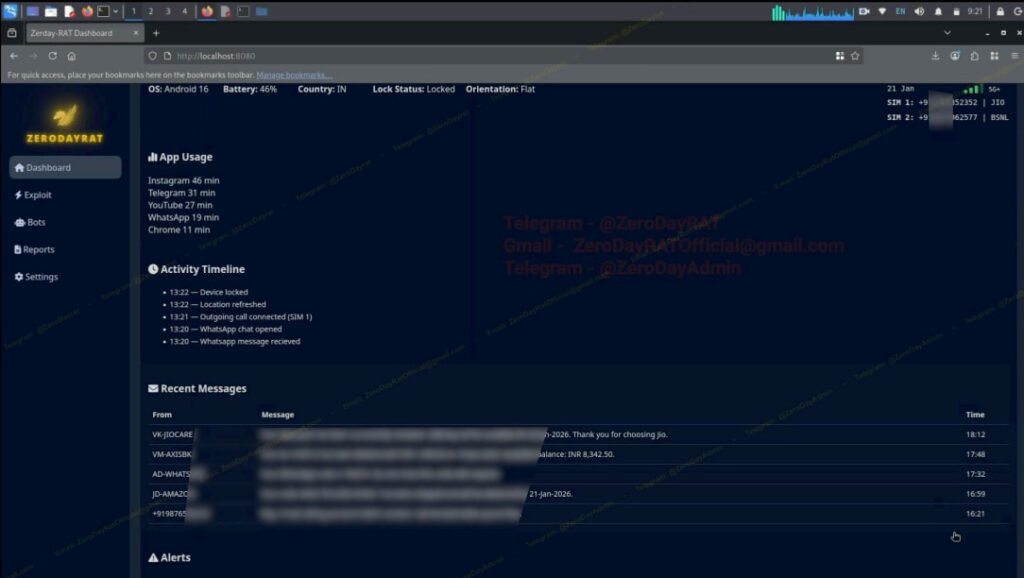
Once a device is infected, ZeroDayRAT presents operators with a comprehensive control panel that displays detailed information about the compromised device. This includes hardware specs, battery status, lock screen status, SIM data, app usage by time, recent SMS messages, and even a real-time timeline of user activity.
The spyware supports Android versions 5 through 16 and iOS up to version 26, including the iPhone 17 Pro, making it compatible with nearly all modern smartphones. From this centralized dashboard, operators can:
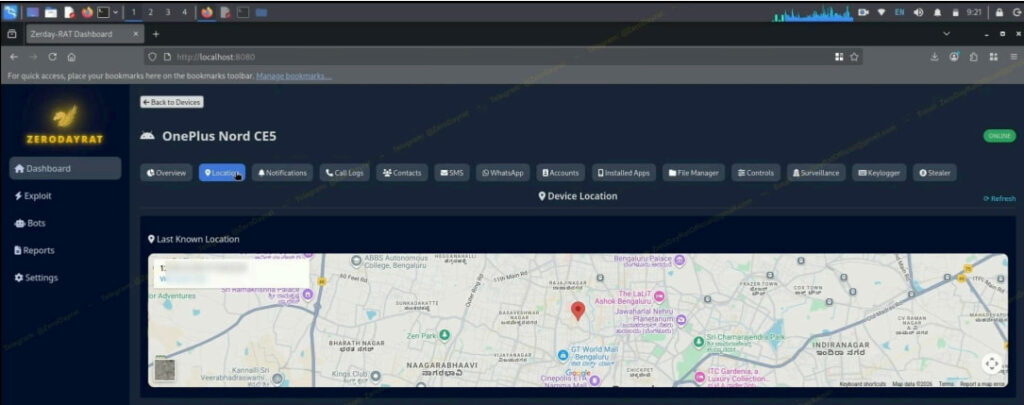
- Track GPS locations with history and embedded Google Maps support.
- Intercept real-time notifications from apps like WhatsApp, Instagram, Telegram, YouTube, and more.
- View registered accounts on the device (e.g., Google, Facebook, Amazon, Paytm), facilitating social engineering or account takeovers.
- Search SMS inboxes, intercept OTP codes, and even send messages from the victim’s number, effectively neutralizing SMS-based 2FA.
iVerify
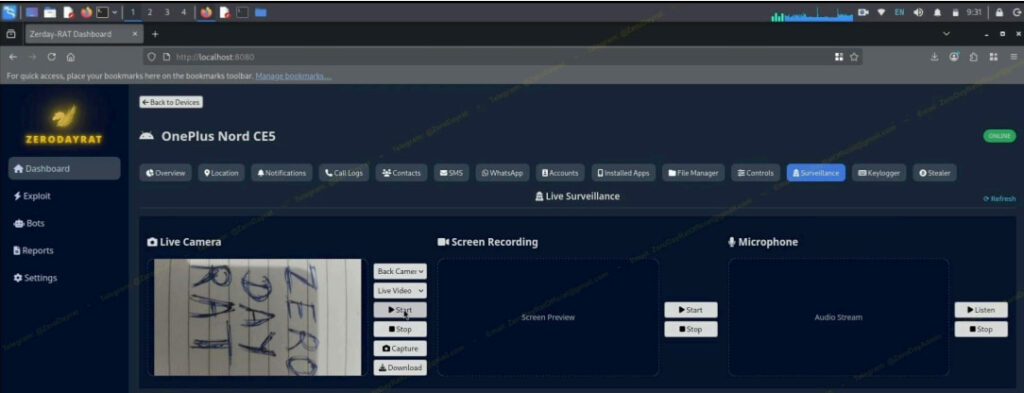
Beyond passive monitoring, ZeroDayRAT grants attackers live access to the victim’s environment. Through the “Surveillance” panel, they can stream video from the front or rear cameras, record the screen in real time, and activate the microphone to eavesdrop on conversations.
iVerify
Keylogging is also built in, recording every keystroke and gesture with millisecond precision, along with contextual app information. A screen preview on the same interface ensures the attacker sees what the victim sees, synchronizing keylogging with visual cues.
iVerify
ZeroDayRAT includes two theft modules: a crypto stealer and a bank stealer.
The crypto stealer scans for popular crypto wallet apps like MetaMask, Trust Wallet, Binance, and Coinbase, logs wallet IDs and balances, and silently replaces copied wallet addresses in the clipboard with the attacker’s, rerouting transactions.
The bank stealer targets mobile banking apps, UPI services (e.g., PhonePe, Google Pay), and digital wallets (e.g., Apple Pay, PayPal) via overlay attacks to steal login credentials.
ZeroDayRAT represents a significant escalation in the commoditization and open sale of mobile surveillance tools. Unlike APT-level spyware that was once exclusive to nation-states or high-end mercenary groups, this platform is now accessible to virtually anyone with a Telegram account and funds to purchase it.
With victims already identified in countries like India and the U.S., and the spyware’s infrastructure designed for scalability and ease of use, ZeroDayRAT is set up to enable widespread abuse.







Zerodayrat scam telegram ,ludzie są oszukani