
A new malware campaign has compromised the privacy of over 900,000 Chrome users by stealthily exfiltrating ChatGPT and DeepSeek conversations through two malicious Chrome extensions.
Discovered by OX Security, the malware mimics a legitimate AI assistant plugin to evade suspicion, with one of the extensions even being endorsed by Google as a “Featured” extension on the Chrome Web Store.
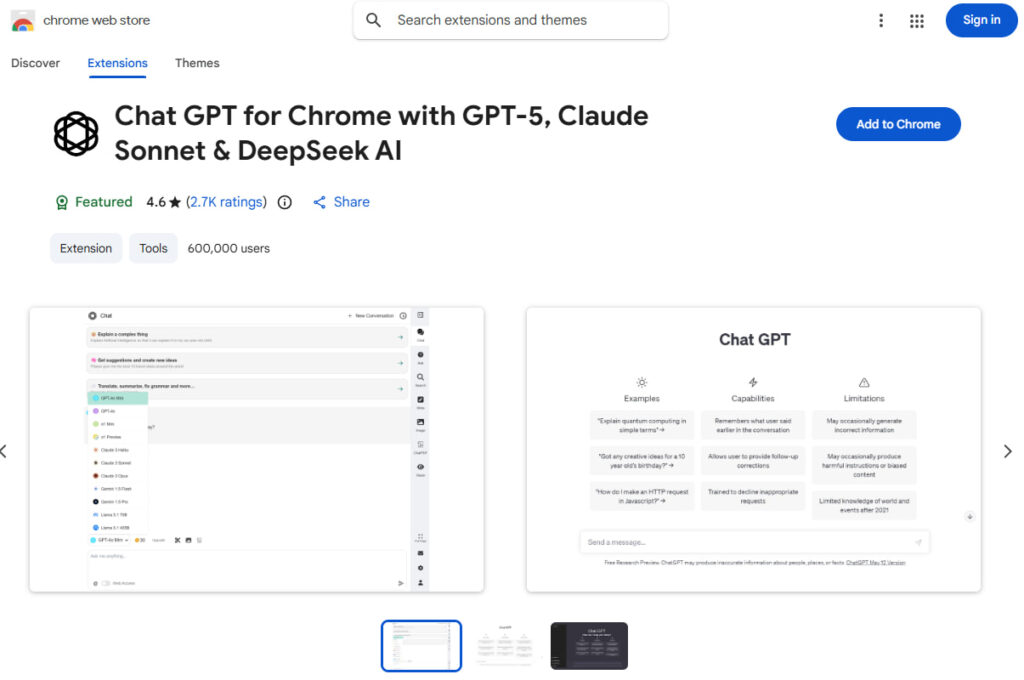
The campaign was uncovered by the OX Research team during a routine threat analysis. The investigation revealed that the malicious extensions impersonated the legitimate AITOPIA Chrome extension, which adds a sidebar for interacting with popular large language models. Instead of merely replicating this functionality, the clones secretly harvested sensitive chat data and browsing activity, transmitting it to attacker-controlled servers at 30-minute intervals.
OX Security reported the issue to Google on December 29, 2025. As of December 30, both extensions remain publicly available on the Chrome Web Store, and the most popular variant still bears Google's “Featured” badge, a designation meant to signal compliance with best practices.
The two malicious extensions uncovered in this campaign are:
- “Chat GPT for Chrome with GPT-5, Claude Sonnet & DeepSeek AI” – 600k installs
- “AI Sidebar with Deepseek, ChatGPT, Claude, and more” – 300k installs
These extensions masquerade as enhanced LLM chat tools but quietly siphon off full conversations, browsing URLs, session tokens, and even internal corporate information. They manipulate Chrome's permissions system by requesting access under the guise of collecting “anonymous, non-identifiable analytics,” which they then abuse for widespread surveillance.
Additionally, the extensions harvest all active tab URLs, exposing users' browsing habits, research keywords, and potentially sensitive query parameters. This data is encoded in Base64 and sent to command-and-control (C2) servers like deepaichats[.]com and chatsaigpt[.]com.
The attackers cloned AITOPIA's user interface and behavior, presenting a virtually identical user experience. The legitimate AITOPIA extension discloses in its privacy policy that it stores user conversations on its servers hosted in Amazon's US region. However, it does not exfiltrate browser content or other unrelated data.
The impersonators went as far as referencing AITOPIA in their privacy policies, confusing users seeking legitimacy. The malware's infrastructure is hosted on Lovable, which further complicates tracking and attribution.
Once installed, the malware assigns a unique user identifier and begins monitoring browser tabs. If a user visits ChatGPT or DeepSeek, the malware scrapes the chat content directly from the DOM. The extension uses Chrome's tabs.onUpdated API to gather URLs and caches this data locally before batch-uploading it to the C2 every half hour.
Uninstalling one malicious extension automatically opens a tab suggesting the user install the other one, a tactic seen before in other persistence-focused malware campaigns.
This incident follows a similar discovery from earlier this month, when Koi Security revealed that several “free VPN” Chrome and Edge extensions, also marked as “Featured,” had been capturing AI chat conversations since July 2025. Those extensions, with over 8 million downloads, embedded JavaScript payloads to intercept prompts and responses across platforms, including Gemini, Copilot, and Grok.
In both cases, the core attack strategy revolves around misusing trusted browser extension permissions and silently harvesting AI interactions, an increasingly sensitive category of data in both consumer and enterprise contexts.







Like with Google reviews in the Chrome store, you can’t flag them (anymore). And how people glaze over Gemini and everything that Google does is just insane! I can’t wait for sheet to hit the fan in 2026.