
A China-aligned APT group dubbed PlushDaemon has executed a supply-chain attack on IPany, a South Korean VPN provider, by embedding a sophisticated backdoor named SlowStepper into its installer. According to ESET researchers, the attack, which began in late 2023, targeted users across South Korea, Japan, and China, with particular focus on industries like semiconductors and software development.
The breach was detected in May 2024, when ESET researchers identified malicious code within an NSIS-based Windows installer downloaded from IPany's official website. The compromised installer, hosted at https://ipany[.]kr/download/IPanyVPNsetup.zip, installed both the legitimate VPN software and the SlowStepper backdoor.
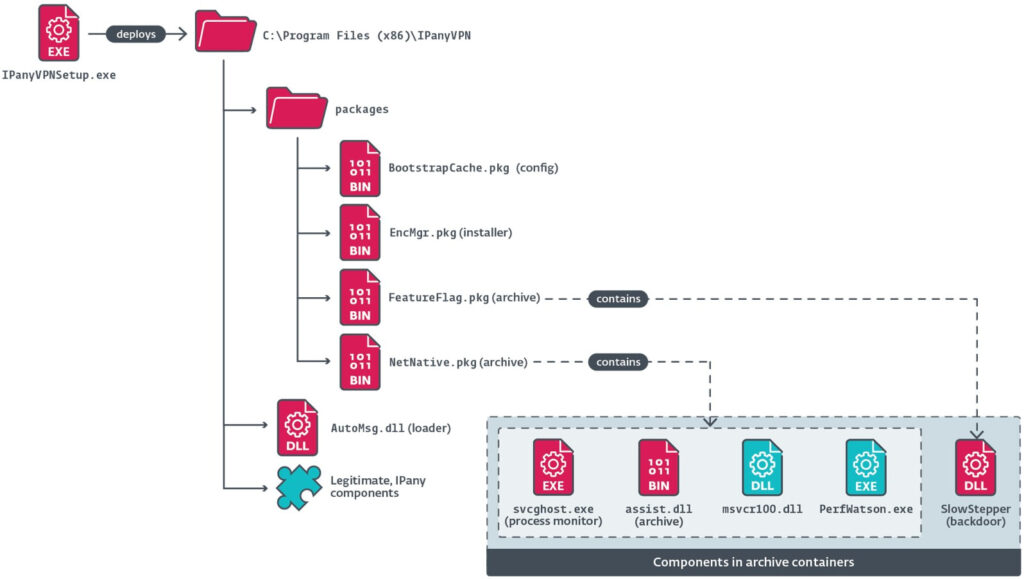
PlushDaemon, active since at least 2019, is known for hijacking legitimate software updates and exploiting vulnerabilities in web servers to gain access. The IPany compromise represents a significant shift in its tactics, marking its first observed supply-chain attack. Once discovered, ESET contacted IPany's developers, leading to the removal of the malicious installer.
Planting an espionage tool
SlowStepper, PlushDaemon's signature implant, is a feature-rich backdoor developed in C++, with additional modules written in Python and Go. The malware is capable of extensive data collection, persistent access, and real-time monitoring of infected systems.
Key capabilities of SlowStepper include:
- Credential theft from browsers and applications
- Surveillance features, including audio and video recording
- File scanning for sensitive documents
- Persistence via Windows Registry modifications
- Encrypted communication with C&C servers via DNS TXT records
- Custom-built Python execution environment for modular operations
The malware's command-and-control (C&C) infrastructure uses Google Public DNS (8.8.8.8), Alibaba DNS, and 114dns.com to resolve attacker-controlled domains, dynamically retrieving an AES-encrypted list of C&C servers. This multi-stage C&C mechanism makes the malware highly resilient against takedowns.
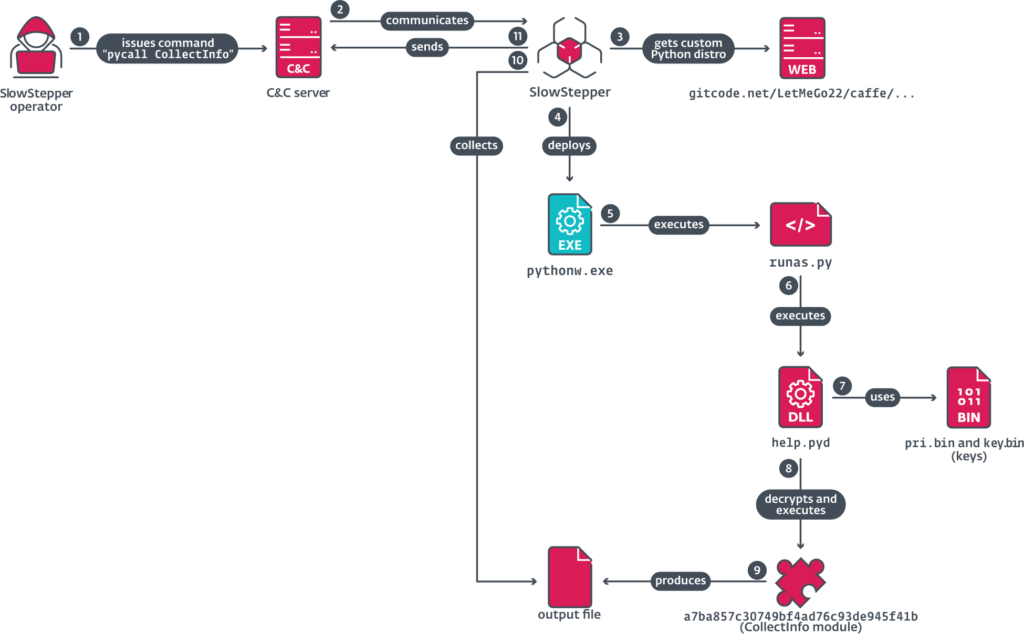
IPany VPN users compromised
The attack primarily affected IPany VPN users in South Korea, but ESET telemetry indicates infections in Japan and China as well. Notably, the malware was detected on networks of a South Korean semiconductor company and a software development firm, suggesting an espionage focus on technology and industrial intelligence.
PlushDaemon's operations align with broader Chinese cyber-espionage campaigns targeting Taiwan, Hong Kong, the United States, and New Zealand. The group's reliance on Chinese-based infrastructure, such as GitCode repositories, further strengthens suspicions of state-sponsored backing.
Given the sophistication of the attack, organizations and individuals using IPany VPN should reinstall the VPN software from a verified clean source and check for unknown system modifications. Additionally, monitor for signs of SlowStepper on system persistence mechanisms, including Registry keys and startup processes. Known C&C domains like “7051.gsm.360safe[.]company” and “st.360safe[.]company” as well as IP addresses linked to PlushDaemon should be blocked.







Leave a Reply