
Have I Been Pwned (HIBP) has added a massive, yet unconfirmed, data breach allegedly impacting Under Armour, exposing the email addresses and personal details of over 72 million individuals.
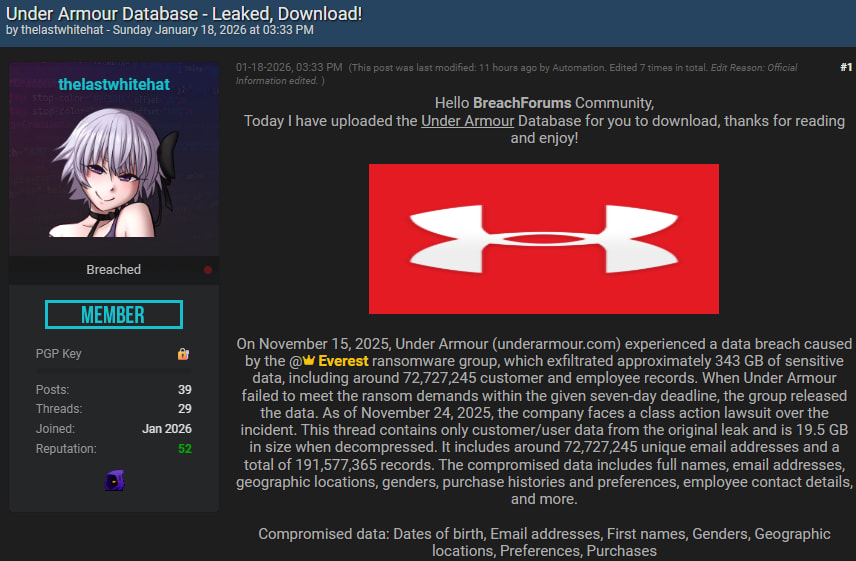
The breach, attributed to the Everest ransomware group, is believed to have occurred in November 2025, with the stolen data surfacing on public hacking forums in January 2026.
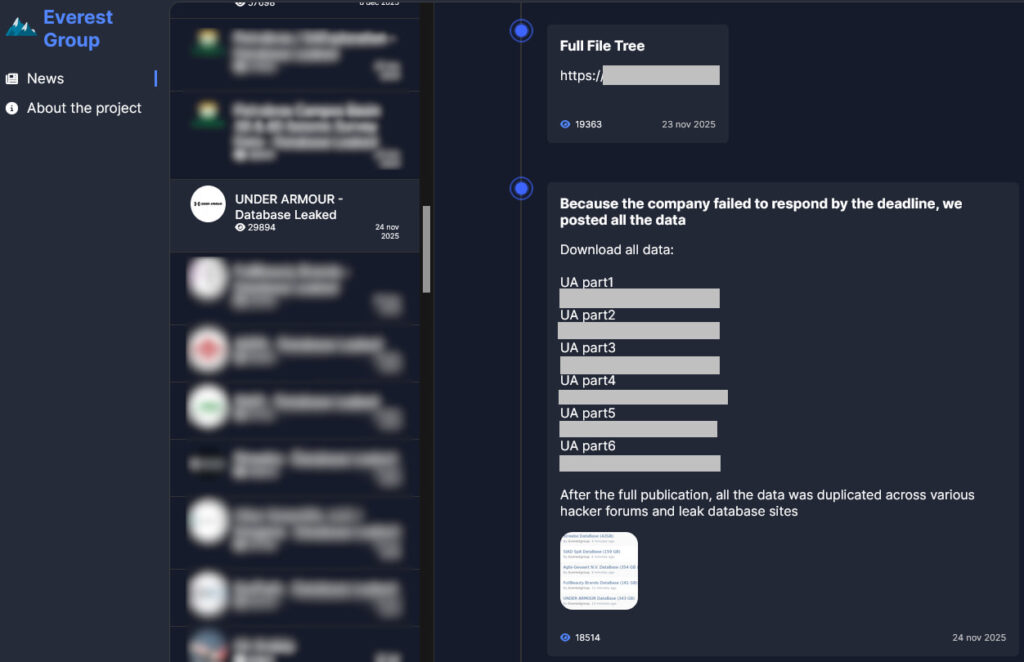
The breach was first publicly claimed by Everest in late 2025 as part of a ransomware extortion attempt. The group alleged it had exfiltrated 343GB of data from Under Armour and threatened to leak the information unless a ransom was paid within a seven-day deadline. After no ransom payment was reported, the attackers published the data on their dark web leak site. By January 2026, the dataset had spread to underground forums.
CyberInsider
The data has since been indexed by DeHashed and added to HIBP today. According to the platform, the breach includes 72.7 million unique email addresses, of which 76% are already present in the HIBP database from previous incidents. However, many records also include extensive personal data, such as:
- Full names
- Dates of birth
- Gender
- Physical addresses
- Purchase history
- Behavioral data, such as shopping preferences and last viewed product categories
In addition to customer information, some leaked documents reportedly contain internal data, including employee contact details and loyalty program records. The decompressed leak amounts to roughly 19.5GB across 191 million records, suggesting a deeply detailed dataset that could fuel phishing, identity theft, and long-term profiling.
CyberInsider
Under Armour, an American sportswear and footwear company known for its global retail operations and e-commerce presence, has not yet confirmed the full scale of the breach. As of writing, the company had not issued official breach notifications to affected customers. Meanwhile, multiple class action lawsuits have already been filed in the US, accusing Under Armour of failing to implement adequate security measures to protect customer data.
The combination of email addresses, names, purchase data, and physical locations makes users vulnerable to targeted phishing campaigns, especially ones impersonating customer support or order-related communications. The availability of addresses and phone numbers also opens the door to harassment, spam, and potential physical threats. Furthermore, if users reused passwords, the exposed information could be used in credential-stuffing attacks on other platforms.
If you received an HIBP alert, monitor bank accounts and credit activity for signs of fraud, and treat unsolicited emails and SMS with heightened vigilance. Finally, change reused passwords on any accounts that may overlap with the email involved in the breach.







I am happy Under Armour didn´t pay the hackers a cent, if everybody did the same we would quickly see how hacking for profit stops.