
Germany’s Federal Office for the Protection of the Constitution (BfV) and the Federal Office for Information Security (BSI) have issued a joint warning about an ongoing phishing campaign leveraging the secure messaging app Signal.
The campaign, which is likely orchestrated by a state-sponsored threat actor, targets politicians, military officials, diplomats, and investigative journalists across Germany and Europe.
According to the advisory published earlier today, the attackers do not exploit software vulnerabilities or deploy malware. Instead, they manipulate legitimate security features of messaging apps using advanced social engineering tactics. The campaign's primary objective is to hijack Signal accounts or covertly eavesdrop on communications, including group chats, by deceiving users into authorizing access.
Exploiting legitimate Signal features
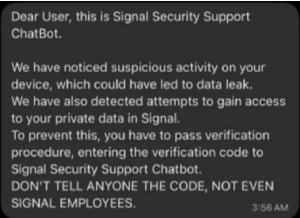
The threat actors employ two distinct but equally deceptive techniques. In the first method, attackers pose as Signal support personnel, using names like “Signal Support” or “Signal Security ChatBot,” and initiate contact via Signal messages. They trigger urgency by warning of a fake security issue and then requesting the victim’s security PIN or an SMS-based verification code. Once obtained, this information allows them to fully take over the account, transferring it to a device and phone number they control. Victims lose access to their account entirely, and the attackers gain full visibility into new messages and contact lists, with the ability to send messages in the victim’s name.
verfassungsschutz.de
The second attack exploits Signal’s legitimate device-linking functionality. The attackers convince users to scan a QR code that, unbeknownst to them, links a new device to their account. This grants the adversaries silent access to all communications for up to 45 days, including contact lists and recent chat history. Unlike the first method, victims retain access to their accounts, making the intrusion much harder to detect.

verfassungsschutz.de
Although technically simple to execute, the attacks are highly effective, blending psychological manipulation with platform-native security mechanisms. The advisory emphasizes that while the threat actor is likely a state-sponsored entity, cybercriminal groups could also replicate the techniques due to their low barrier to entry.
Signal, an encrypted messaging platform popular among privacy-conscious users, is widely used in Europe for secure communication. Despite its robust cryptographic foundations, the platform’s security model still relies heavily on user behavior and the integrity of multi-device authentication processes.
Recommended defenses
BfV and BSI urge users, especially those in sensitive positions, to adopt the following countermeasures:
- Do not respond to messages from accounts claiming to be Signal support; Signal never contacts users via chat.
- Never share your Signal PIN or verification codes in plaintext messages.
- Enable the registration lock in Signal’s options to prevent unauthorized re-registration of your account.
- Only scan QR codes when you are intentionally linking a new device yourself.
- Regularly review devices linked to your account and remove unfamiliar entries.
- Ignore unsolicited group invitations and treat unexpected security code changes from contacts as potential signs of compromise.
Users in Germany who suspect they may have been targeted or compromised are encouraged to contact BSI or BfV immediately.







Leave a Reply