
Researchers have uncovered two active campaigns involving dozens of malicious Chrome extensions still live on official browser extension stores.
These extensions, many disguised as AI productivity tools or utilities, silently steal session tokens, hijack search results, inject ads, exfiltrate data, and even execute remote code, all while appearing legitimate to unsuspecting users.
The most recent discovery comes from LayerX, which identified a coordinated cluster of 16 malicious Chrome extensions designed to steal ChatGPT session tokens. Separately, Symantec has published an investigation into multiple browser add-ons with user bases exceeding 100,000 that expose clipboards, exfiltrate cookies, and execute code via command-and-control infrastructure.
ChatGPT account theft
LayerX discovered a campaign masquerading as a suite of ChatGPT enhancement tools. Despite being marketed with innocuous names like ChatGPT Voice Download and Prompt Manager, the extensions quietly intercept users’ authentication tokens and transmit them to a remote server. Possession of these tokens grants attackers full access to the user’s ChatGPT account, including conversation history, code snippets, and linked third-party services such as GitHub, Google Drive, or Slack.
The extensions inject JavaScript content scripts into ChatGPT’s frontend, operating within the MAIN JavaScript world, giving them access to sensitive in-memory objects and functions. By hooking into window.fetch, the scripts extract authentication headers and forward them to attacker-controlled infrastructure. This enables persistent impersonation of the user’s session, effectively bypassing authentication without needing credentials or exploiting vulnerabilities in OpenAI's platform.
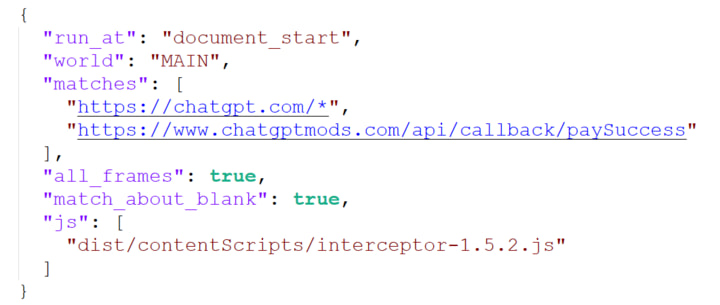
LayerX
All 16 variants, including one listed as “featured” in the Chrome Web Store, share a common minified codebase and branding strategy, suggesting a single coordinated threat actor. Fifteen of the extensions are distributed via the Chrome Web Store and one via Microsoft Edge Add-ons. As of this writing, they remain online. While the cumulative install count is just under 900, LayerX warns this is likely an early-stage deployment, an attempt to seed trust and test efficacy before scaling distribution.
Broader threat landscape
In parallel, Symantec published a report examining several malicious Chrome extensions with larger footprints and broader attack surfaces. These include:
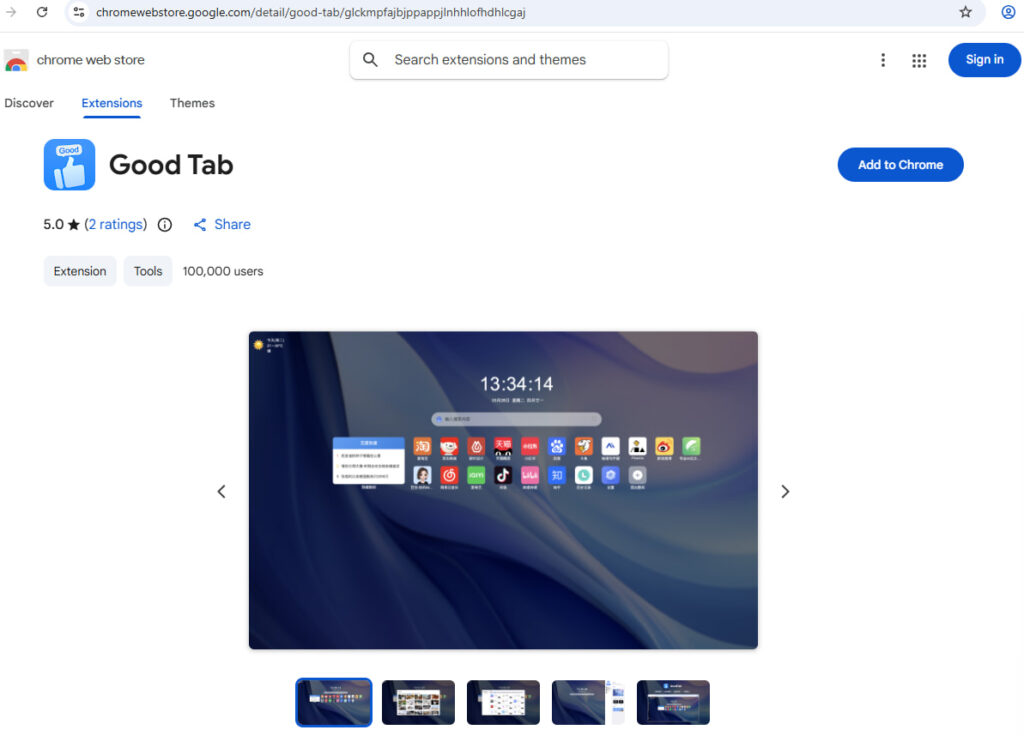
Good Tab: A “new tab” utility that silently grants clipboard access to a remote domain via an insecure iframe. This exposes sensitive clipboard data such as passwords and cryptocurrency wallet addresses to interception or manipulation.
Children Protection: Poses as parental control software but incorporates full C&C capabilities, cookie exfiltration, ad injection, and a domain generation algorithm (DGA) to cycle C&C domains daily. It can remotely execute arbitrary JavaScript in any browser tab, enabling total browser compromise.
DPS Websafe: A search hijacker that impersonates the Adblock Plus brand while redirecting user queries to monetized domains. It collects telemetry and sends it to a tracking domain without user consent.
Stock Informer: A market info tool embedding an exploitable XSS vulnerability (CVE-2020-28707) that allows websites to execute JavaScript in the browser. It also hijacks search and leaks user browsing activity.
While differing in scope and tactics, these extensions all misuse browser permissions, feature obfuscated JavaScript, and vague or misleading functionality. All were available in the Chrome Web Store at the time of Symantec’s examination, while CyberInsider could confirm Good Tab, with 100k downloads, is still available at the time of writing.







Not so ironically AI in itself is a blunt tool to steal everyones data
Guess when its for BigTech/states/governments/political agendas it’s not considered stealing user data
Weird