Researchers from the University of the West Indies have uncovered a novel vulnerability in Wi-Fi Protected Access 3 (WPA3) networks, exploiting a combination of downgrade attacks, social engineering, and captive portals to extract network passwords. This method challenges the robust security reputation of WPA3, highlighting practical risks for networks using its transition mode.
WPA3 was introduced in 2018 as the successor to WPA2, incorporating advanced security features like Simultaneous Authentication of Equals (SAE) to resist offline dictionary attacks and provide forward secrecy. However, its transition mode, designed to ease adoption by supporting WPA2 devices, has been a focal point for vulnerabilities.
The Wi-Fi Alliance, which certifies WPA3, asserts that transition mode ensures backward compatibility, but this latest research underscores that such features can also weaken network defenses.
Attacking WPA3 security
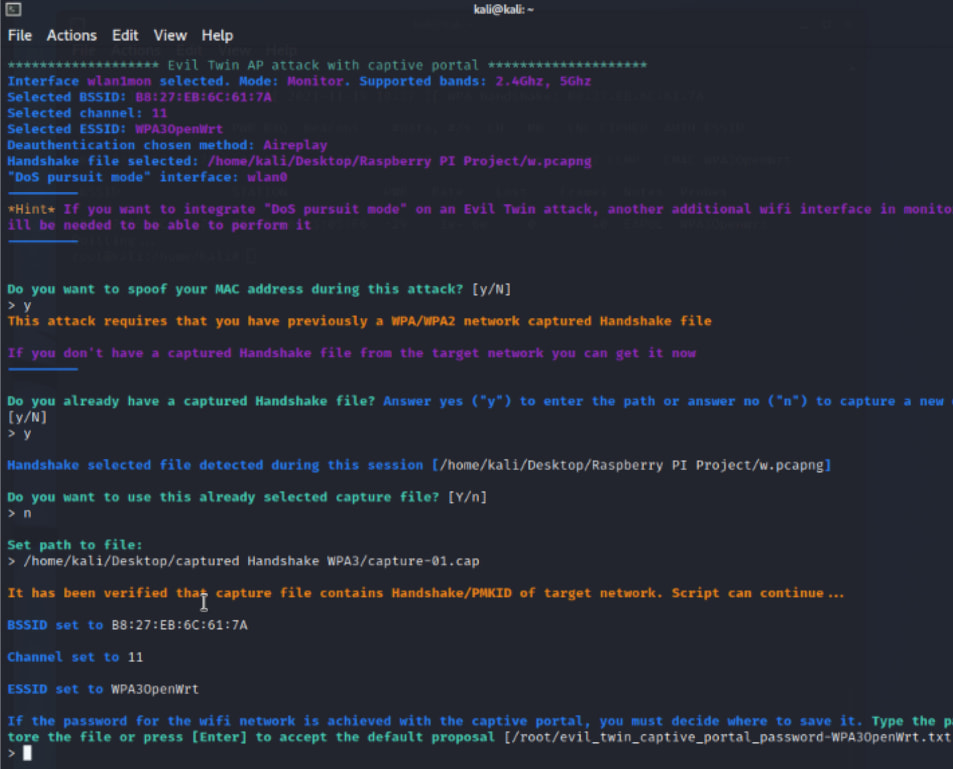
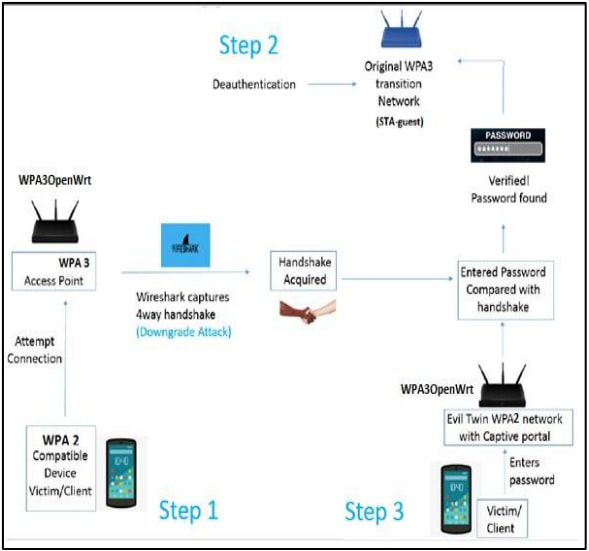
The researchers demonstrated how a WPA3 network can be compromised by exploiting its transition mode, building on known vulnerabilities such as the “Dragonblood” downgrade attack, allowing attackers to force a WPA3 network into WPA2 compatibility mode. This enabled them to capture WPA2/WPA3 handshakes, a prerequisite for their proof-of-concept attack.
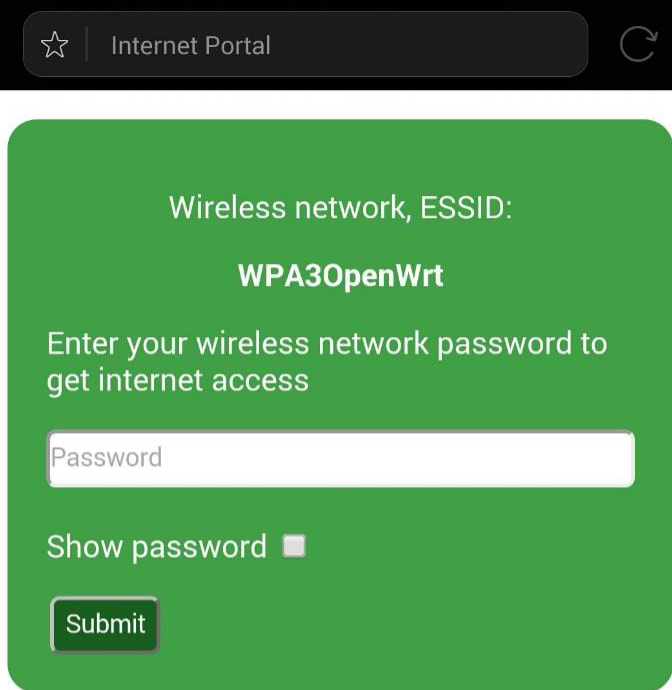
Utilizing inexpensive hardware, such as Raspberry Pi devices, the team set up a rogue WPA3 network with a captive portal, mimicking the legitimate network's SSID. Users attempting to reconnect were redirected to the rogue network's captive portal, where they unwittingly entered their network credentials. The captured handshake was then verified against the password entered in the portal to ensure authenticity.
arxiv.org
The attack followed these three main steps:
- Handshake capture: Using a downgrade attack, researchers captured the initial handshake between the client and the WPA3 access point.
- Deauthentication: Legitimate users were disconnected from the original network using denial-of-service methods, such as bad token injections or CPU overload exploits.
- Captive portal: The rogue network, created using Airgeddon, presented a portal to unsuspecting users where passwords were harvested.
arxiv.org
The experiment utilized tools like Wireshark for packet capture and OpenWrt to simulate a WPA2/WPA3 environment. It highlighted that key security features, like Protected Management Frames, are critical in preventing such attacks but are often disabled due to misconfigurations.
The main takeaway from the experiment is that the social engineering aspect of the attack proved effective, especially against users unfamiliar with network security. Also, WPA3's reliance on transition mode allowed attackers to capture WPA2-compatible handshakes, but not all devices behaved predictably. For instance, some failed to connect or misclassified WPA3 encryption standards.
arxiv.org
Protecting WPA3 networks
This study highlights critical gaps in WPA3's implementation and user awareness, especially for networks relying on transition mode.
The findings underscore the need for administrators to enable protected management frames to guard against deauthentication attacks, and, when possible, enforce WPA3-only settings to eliminate vulnerabilities stemming from backward compatibility.
Ultimately, users should look out for suspicious network prompts, verify the legitimacy of captive portals, and consider the possibility of rogue SSIDs mimicking legitimate networks.







Leave a Reply