
ESET analysts have identified a novel phishing method that exploits Progressive Web Applications (PWAs) to target mobile users on both Android and iOS.
This sophisticated attack method, first reported by CSIRT KNF in Poland and later observed in Czechia by ESET, bypasses traditional security measures, allowing phishing apps to be installed on users' devices without the typical warnings associated with third-party installations.
The technique involves tricking users into installing PWAs that mimic legitimate banking applications. On iOS, users are instructed to add a PWA to their home screen, while on Android, a WebAPK—a native Android application generated from a PWA—can be silently installed, often appearing as though it was downloaded from the Google Play store. These phishing apps are nearly indistinguishable from the real banking apps they impersonate, making detection by the average user incredibly challenging.
PWA-based phishing
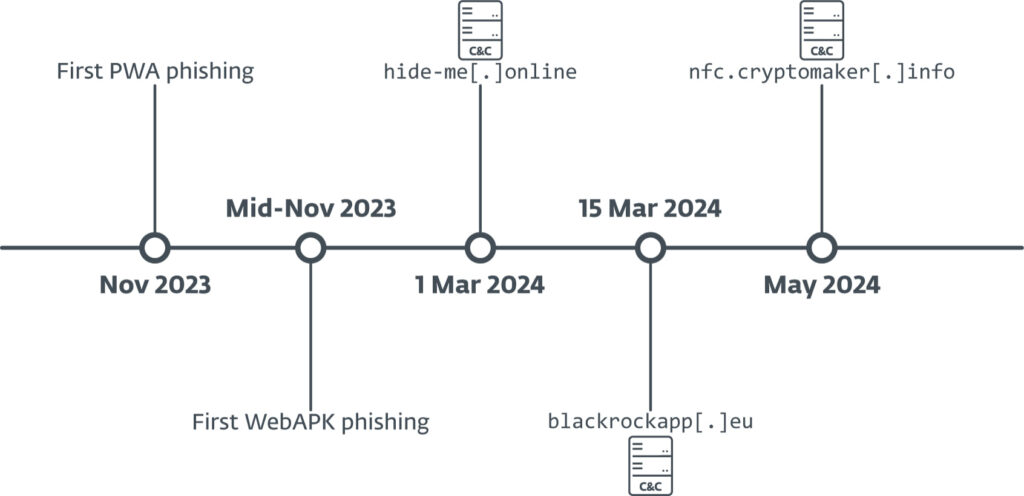
The first instance of this phishing method was detected in early November 2023, with a shift to WebAPK usage by mid-November. C&C servers linked to the campaigns were first discovered in March 2024, confirming the ongoing nature of these attacks. The phishing domains and C&C servers, including “hide-me[.]online” and “cryptomaker[.]info,” were hosted by various providers, including Cloudflare and NETH LLC.
ESET
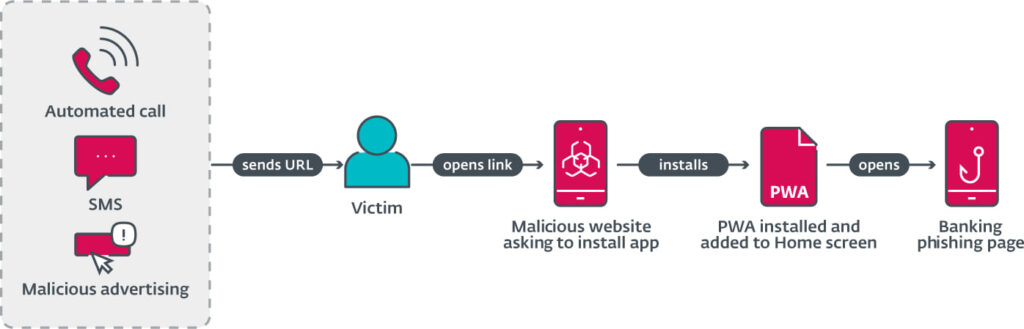
ESET's analysis reveals that the phishing campaigns begin with the distribution of malicious URLs through various channels, including automated voice calls, SMS messages, and social media advertisements. The voice calls claim that the user's banking app is outdated and prompts them to press a button to receive an SMS with a link to update the app. SMS messages are sent indiscriminately, urging recipients to click a link under the guise of a critical update.
Additionally, malicious ads on platforms like Facebook and Instagram lure victims with offers or warnings, directing them to download a supposed app update.
ESET
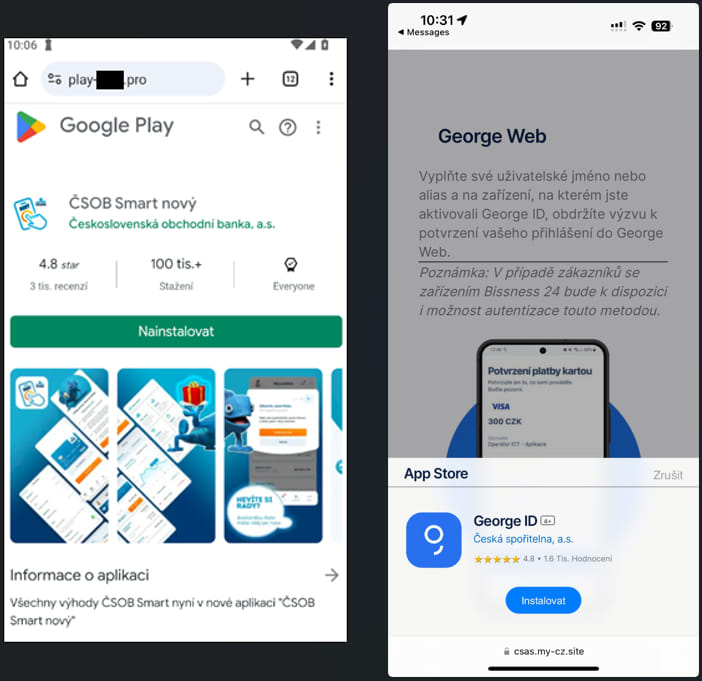
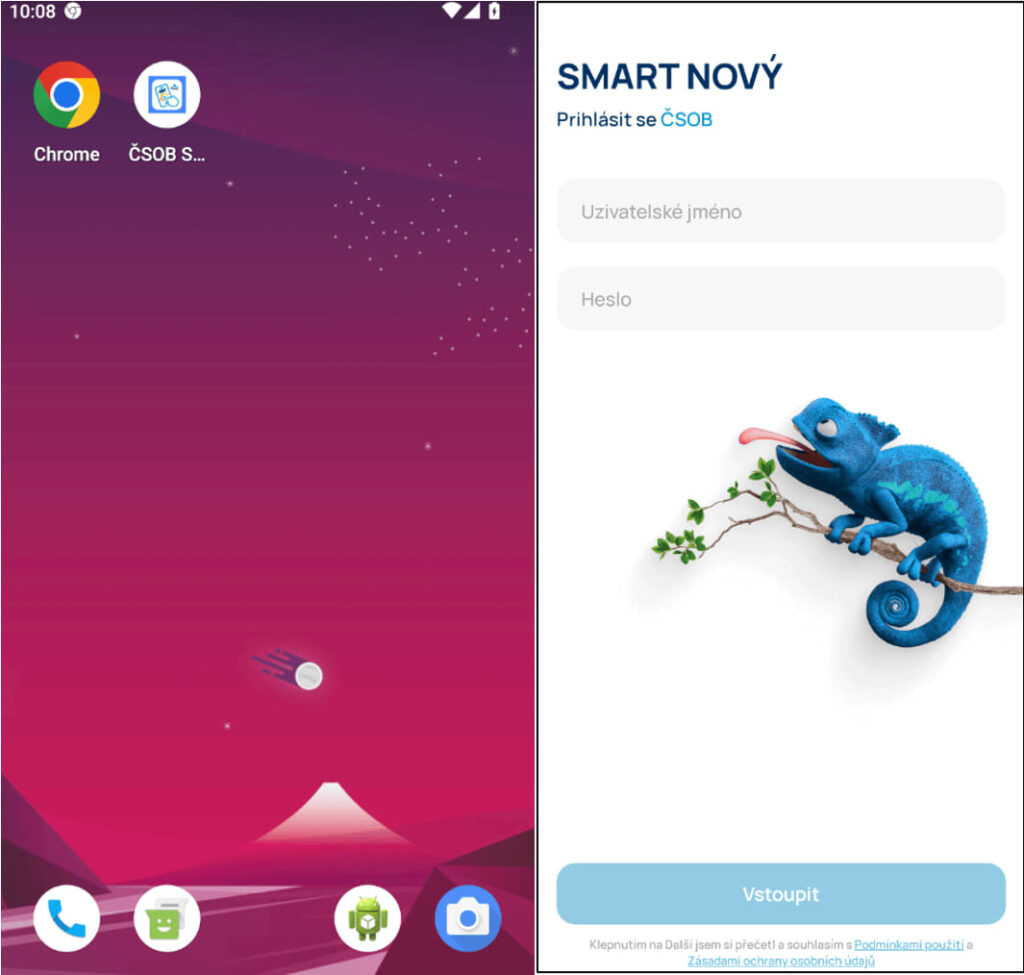
Once the user clicks the link, they are directed to a convincing phishing page. Android users are presented with a fake Google Play store page, while iOS users see a prompt to install a PWA. These phishing apps, once installed, function as a gateway for attackers to harvest sensitive banking credentials. The apps' icons and installation processes mimic those of legitimate apps, further enhancing their deceptive appearance.
ESET
Technical analysis
PWAs and WebAPKs, central to this phishing strategy, are typically used to deliver web applications with the look and feel of native apps. However, in this phishing campaign, these technologies are weaponized to bypass security protocols. PWAs run cross-platform and can be installed on both Android and iOS devices. WebAPKs, specific to Android, eliminate the usual warnings about installing third-party apps, making them particularly dangerous.
ESET's investigation into these campaigns revealed that two distinct threat actors were behind the attacks. The first group used a Telegram bot to log stolen credentials, sending them to a private group chat. The second group employed a more traditional command-and-control (C&C) server to manage the stolen data and control the phishing operations. The campaigns primarily targeted clients of banks in Czechia but also extended to banks in Hungary and Georgia.
ESET
Defense and mitigation
ESET has taken steps to mitigate the impact of these phishing campaigns by notifying the affected banks and working to have the malicious domains and C&C servers taken down. Users are advised to be vigilant about unexpected prompts to install apps, especially from sources outside official app stores. It is crucial to scrutinize URLs and be wary of installation requests that do not follow the usual security protocols.
For further protection, users should ensure that their mobile devices are set to block installations from unknown sources and that they only download apps directly from trusted platforms like the Google Play store or Apple's App Store.







Once again, stupid people who click on links are responsible, as are financial institutions and corporations who include links in SMS and emails.