
A sophisticated cyberattack targeting the XZ Utils software, integral to most major Linux distributions, was recently unveiled, shaking the open-source software community.
XZ Utils is a collection of free software utilities for compressing and decompressing files. It's most commonly used for handling files compressed in the .xz format, which is known for its high compression ratio. The XZ format is utilized in various software distribution and archive systems within the Linux ecosystem, making XZ Utils an essential tool for Linux users and developers.
The attack, which has received the identifier “CVE-2024-3094,” involved the introduction of malicious code that granted unauthorized remote access via SSH, potentially affecting numerous systems globally.
The malicious commit in XZ Utils was discovered by Andres Freund, a software engineer at Microsoft and a developer for the PostgreSQL project. Freund identified the issue when he noticed an uptick in CPU usage by the SSH daemon, which prompted him to investigate further, ultimately leading to the discovery of the malicious code.
The backdoor was introduced by a developer using the pseudonym Jia Tan or JiaT75, who managed to become a trusted contributor to the XZ Utils project over time. Jia Tan concealed the backdoor within two recent versions of XZ Utils, namely 5.6.0 and 5.6.1. This code was designed to hijack the OpenSSH server process, allowing attackers to execute arbitrary commands on affected machines before authentication, thereby gaining complete control. The following diagram, created by Thomas Roccia, provides a good overview of the attack.
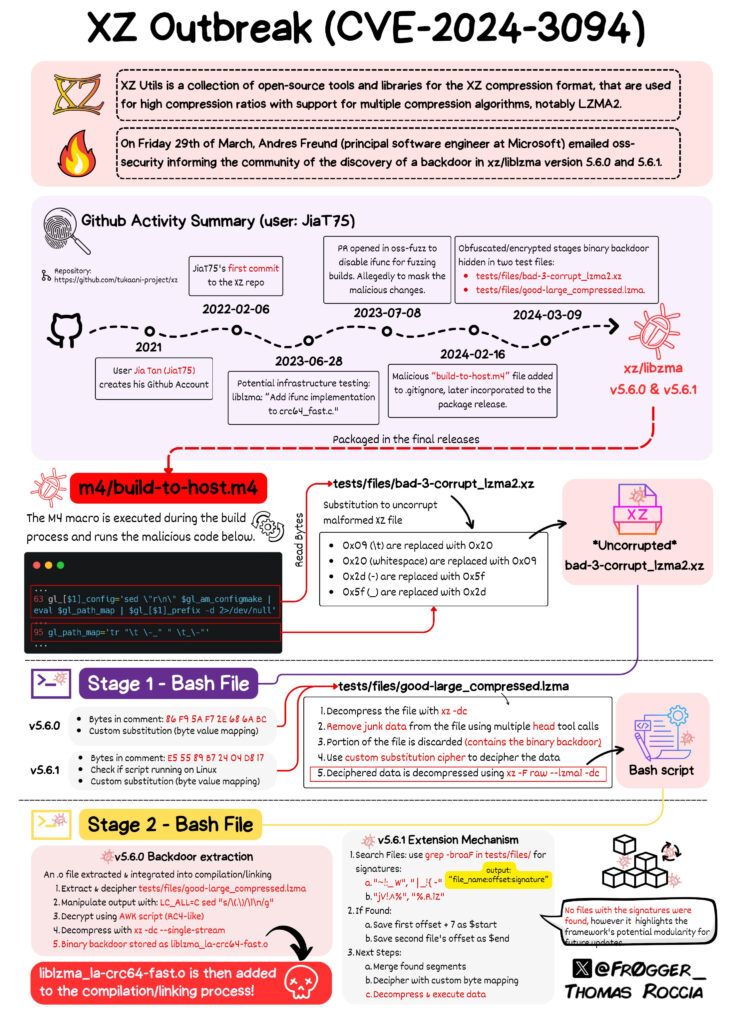
The affected versions were released in a short timeframe and were quickly identified and isolated, with the majority of stable Linux distributions remaining unaffected due to their use of earlier, secure versions.
Affected distributions include Fedora, Debian, Alpine, Kali, OpenSUSE, and Arch Linux, all of which have released security bulletins to provide their users with detailed remediation steps. These involve downgrading to unaffected versions of XZ Utils and applying specific measures to mitigate the risk posed by the compromised software. Due to the delay in most Linux distributions adopting “bleeding-edge” package versions, the impacted XZ Utils versions were primarily only found in beta/experimental and “rolling” releases.
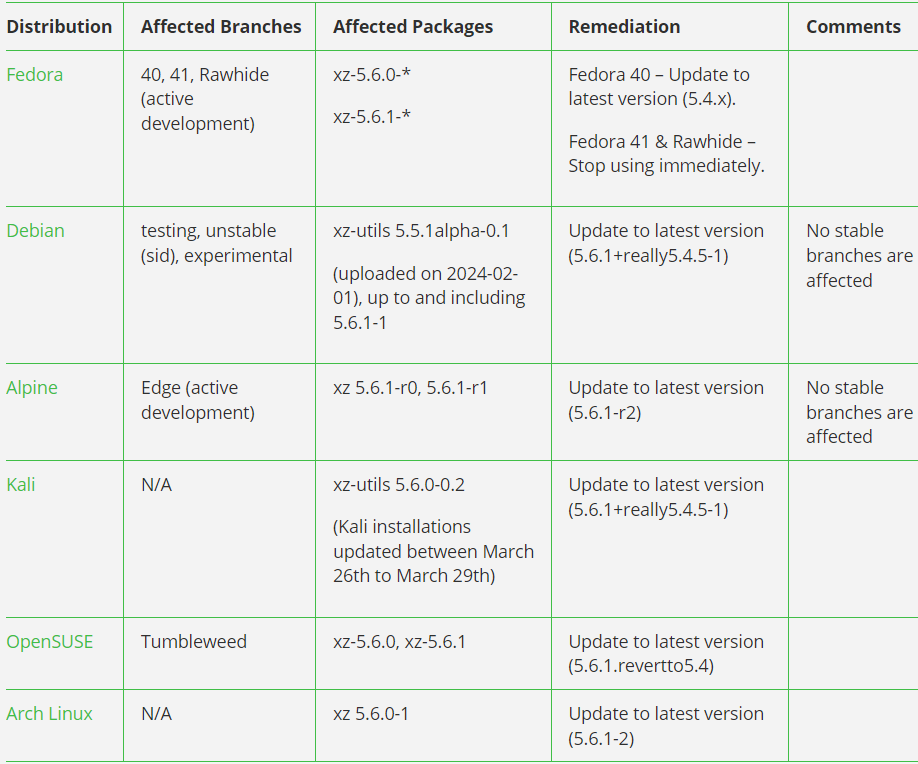
The discovery and analysis of this attack serve as a stark reminder of the critical risks that exist within the software supply chain, particularly in open-source software projects. The response to this incident highlights the crucial role of vigilance, rapid action, and community engagement in safeguarding the security and integrity of widely used software. However, it's clear that more systematic efforts are needed to ensure the security of OSS projects, as Freund's discovery was largely accidental.






Leave a Reply