
Proton has accused Google of failing to promptly remove malicious Chrome extensions impersonating its VPN service, warning that fake listings remained available for weeks despite repeated reports.
The privacy firm says attackers are exploiting delays in Google’s review and takedown process to steal user credentials and sensitive data.
In a series of posts published on X, Proton VPN stated that it had notified Google three separate times since the beginning of the year about fraudulent Proton VPN extensions hosted on the Chrome Web Store. According to the company, the malicious listings were created by unverified developers who used Proton’s name and branding to trick users into installing spyware disguised as legitimate VPN tools.
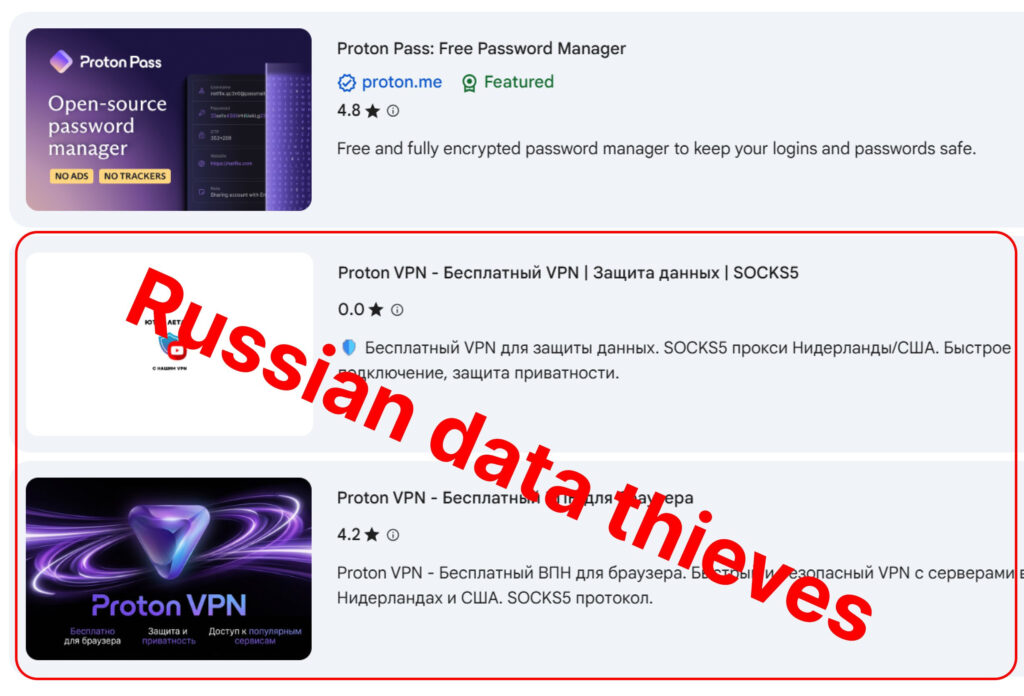
Proton says the issue goes beyond simple trademark abuse. The fake extensions were allegedly capable of harvesting login credentials, collecting personal data, and monitoring users’ browsing activity. In some cases, Proton warned, stolen internet traffic could potentially be relayed to third parties such as advertisers or even hostile state actors, although the company did not publicly attribute the campaign to a specific threat group.
The repeated discovery of the fake add-ons was made through Proton’s internal monitoring and user reports, after which the company says it promptly alerted Google. Despite what Proton described as “blatantly obvious” signs of impersonation and prior reporting, the removal process reportedly took several weeks in multiple cases. During that period, unsuspecting users searching for Proton VPN in the Chrome Web Store could encounter and install the malicious extensions.
Proton AG, the Swiss-based company behind Proton VPN and Proton Mail, provides privacy-focused services to tens of millions of users worldwide. Its products are widely used by journalists, activists, businesses, and privacy-conscious individuals seeking encrypted communications and secure internet access. Because of the company’s strong brand recognition in the privacy space, Proton says it has become a frequent target for impersonation campaigns.
Proton outlined steps users can take to protect themselves from malicious browser extensions:
- Download software only from Proton’s official website, proton.me, rather than searching directly within extension or app stores.
- Verify that the publisher is listed as “Proton AG” and that the store page links back to proton.me.
- Avoid relying on store search results for branded terms, as attackers often exploit brand-name queries.
- Carefully review requested permissions and be wary of extensions asking for broad access, such as the ability to “read and change all your data on all websites,” especially when such access is unrelated to the tool’s function.
Proton emphasized that app stores are not a guarantee of safety and that the most secure download path is through a company’s official website.







Leave a Reply