
A novel infection chain involving a fake uBlock Origin Lite extension triggers a PowerShell-delivered browser crash mechanism dubbed “CrashFix” to drop a Python backdoor named ModeloRAT.
The operation was discovered in January 2026 by Huntress analyst Tanner Filip during an investigation into suspicious browser behavior on a corporate machine. Huntress attributes this campaign to KongTuke, a group active since early 2025.
The infection begins with a malicious Chrome extension called NexShield, which poses as a lightweight ad blocker and was available through the official Chrome Web Store. The extension was reportedly found by a victim searching for ad-blocking tools, ironically while trying to avoid malvertising, and served via a sponsored result pointing to a seemingly legitimate Chrome Web Store page. The extension mimics uBlock Origin Lite almost byte-for-byte, even falsely attributing development to Raymond Hill, the creator of the legitimate uBO project. However, its background script (background.js) contains approximately 3KB of additional code used for malicious telemetry and browser manipulation.
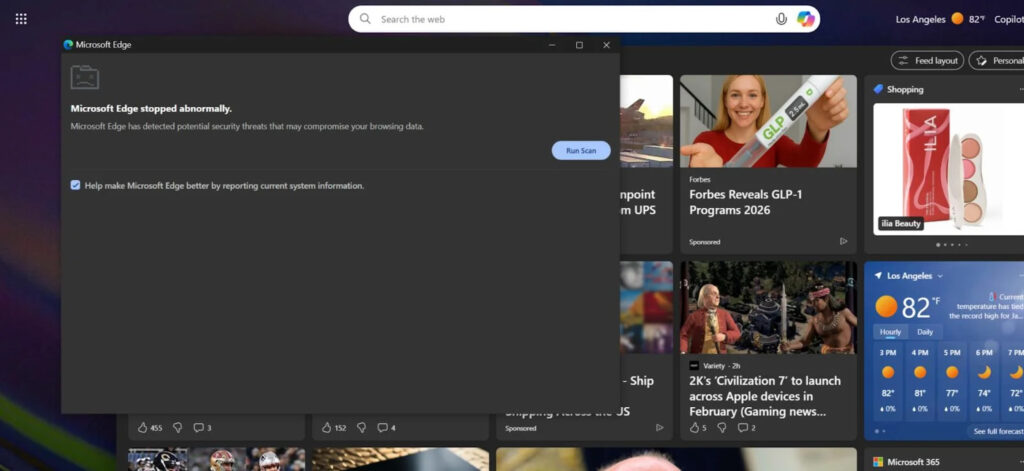
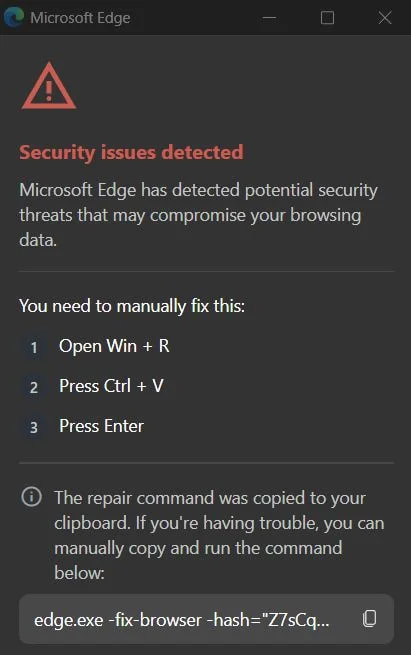
NexShield’s core payload delays its malicious activity for 60 minutes after installation to avoid detection, using the Chrome Alarms API. It then floods the browser with internal port connections, causing resource exhaustion and freezing it. When the user force-quits and restarts their browser, a CrashFix pop-up appears, mimicking a Chrome diagnostic page claiming the browser stopped abnormally. The user is instructed to open the Windows Run dialog and paste a command, which is actually a PowerShell payload silently copied to the clipboard by the extension.
Huntress
The command abuses finger.exe, a legacy Windows binary turned Living-off-the-Land Binary (LOLBin), to pull remote code from an attacker-controlled IP (199.217.98[.]108). The server returns obfuscated PowerShell that downloads and executes additional payloads, and removes traces afterward.
Huntress
Once executed, the infection chain checks whether the host is domain-joined, distinguishing corporate environments from home users. Non-domain machines receive an incomplete payload, often ending in a test message (“TEST PAYLOAD!!!!”), while domain-joined machines are served a ZIP archive containing a full WinPython distribution and a script named modes.py, the main payload.
This script is ModeloRAT, a custom Python Remote Access Trojan featuring:
- RC4-encrypted communications over hardcoded C2 IPs
- Beacon intervals that adapt based on connectivity and C2 responses, varying between 150 milliseconds and 15 minutes.
- Full system reconnaissance, including OS info, running processes, network details, and privilege levels.
- Registry-based persistence under misleading names like “Spotify47” or “Adobe2841” to blend with legitimate software.
- Support for multiple payload types, including EXEs, DLLs, and Python scripts, dispatched as encrypted command types.
ModeloRAT is highly obfuscated, using verbose naming conventions and bloated with junk code designed to confuse reverse engineers. Its data encoding uses RC4 with a version marker and zlib compression, making it difficult to extract indicators of compromise through simple scanning.
To defend against campaigns like this, avoid installing extensions from ads, even if they link to the Chrome Web Store, and always verify the developer’s identity and source code when possible.







Leave a Reply