A new powerful side-channel attack called MEMORY DISORDER is capable of leaking information from modern CPUs and GPUs from Intel, Apple, and AMD, without relying on timers.
The implications of the research are far-reaching, demonstrating practical covert channels and application fingerprinting across multiple platforms, including AMD's Radeon GPUs.
The technical paper explores how common microarchitectural behavior, specifically memory re-orderings, can be repurposed as a timerless signal between processes. These re-orderings are an optimization feature in modern processors, where memory operations are executed out of order to improve performance. Crucially, these behaviors are part of the hardware-level memory consistency models (MCMs) of most CPUs and GPUs today.
By leveraging these memory re-orderings, the researchers demonstrate that one process can infer the activity of another, even across virtual machine boundaries in environments like KVM. This is accomplished using small parallel programs called litmus tests, which monitor the memory subsystem for signs of reordering triggered by concurrent activity elsewhere in the system.
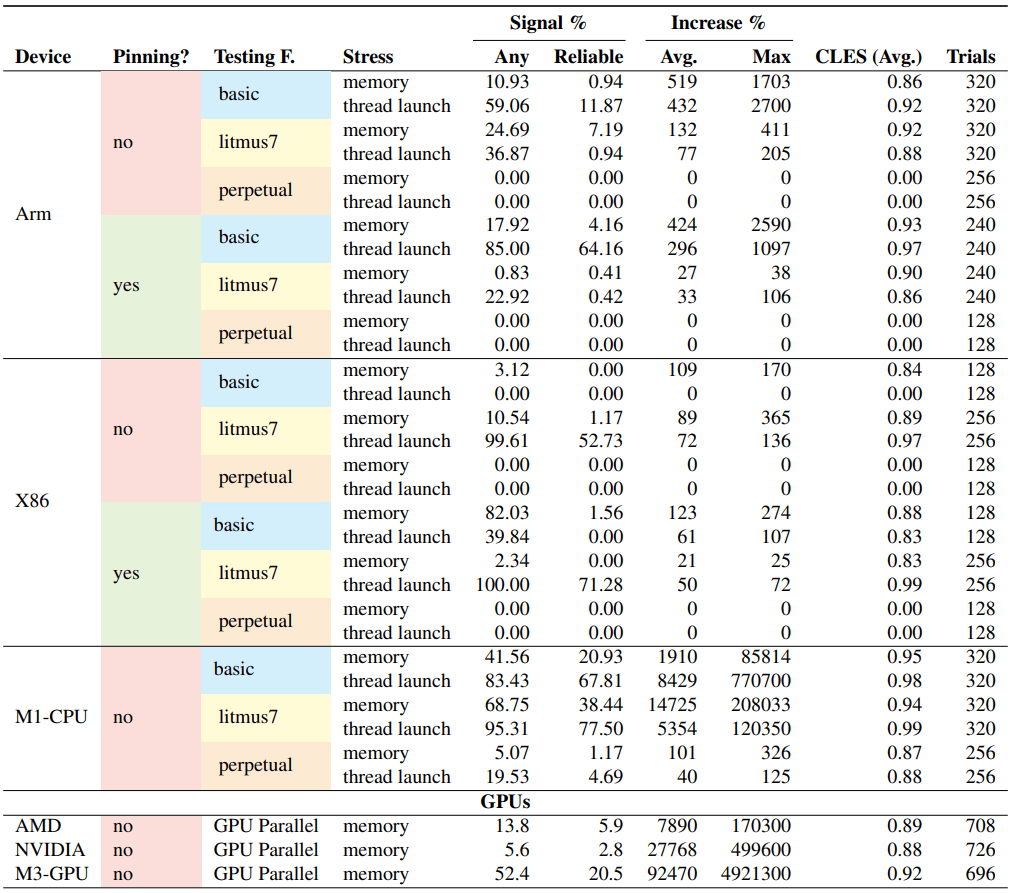
The affected processors include a wide range of architectures, including Apple M1 and M3 CPUs/GPUs, Intel i7 (x86), Arm A78, NVIDIA RTX 4070, and AMD Radeon RX 7900 XT. Even though AMD's GPU architecture doesn't run kernels from different processes in parallel, researchers found that DISORDER-style signals could still be observed due to persistent memory effects across kernel executions.
arxiv.org
AMD acknowledged the research in a security bulletin and credited the academic team with a coordinated disclosure. While the company did not assign a severity rating, labeling it informational, they did release new mitigation guidance. Specifically, AMD has introduced an optional operating mode (identified as AMD-SB-6010) that can restrict concurrent process execution on GPUs and ensure GPU register state is cleared between processes. This mode is disabled by default and must be manually enabled by system administrators.
AMD also reaffirms general secure coding best practices, advising developers to implement constant-time algorithms and to avoid secret-dependent memory access or control flows to reduce side-channel risks.
Although no immediate exploit is known to be in the wild, the implications of the MEMORY DISORDER technique are significant for cloud environments using virtualized workloads on shared hardware, machine learning services running on GPUs, and multitenant servers relying on hardware isolation.
The paper shows that even with minimal privileges, two threads, and shared memory, an attacker can leak information. On Apple's M3 GPU, for instance, researchers achieved 95% accurate covert communication at 16 bits per second. More advanced tuning on x86 CPUs pushed throughput to nearly 30,000 bits per second, highlighting just how serious this class of attacks could become.
Fingerprinting experiments were also successful. The researchers trained classifiers to distinguish deep neural network models (e.g., ResNet50, MobileNetV3, AlexNet) based on their memory reordering footprints. They even demonstrated that launching Google Chrome could be detected using this method on an Apple M1 chip.
As of publication, neither Intel nor Apple has issued a security bulletin about MEMORY DISORDER despite the paper demonstrating reliable data leakage on their platforms.







Leave a Reply